Enumeration
Firstly, I checked for open ports on the target machine using Nmap:
cat nmap.txt
# Nmap 7.94SVN scan initiated Sat Jul 20 22:44:21 2024 as: nmap -Pn -p- -sC -sV -oN nmap.txt -v 10.129.116.102
Nmap scan report for 10.129.116.102
Host is up (0.050s latency).
Not shown: 65532 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 57:d6:92:8a:72:44:84:17:29:eb:5c:c9:63:6a:fe:fd (ECDSA)
|_ 256 40:ea:17:b1:b6:c5:3f:42:56:67:4a:3c:ee:75:23:2f (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://greenhorn.htb/
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: nginx/1.18.0 (Ubuntu)
3000/tcp open ppp?
| fingerprint-strings:
| GenericLines, Help, RTSPRequest:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 200 OK
| Cache-Control: max-age=0, private, must-revalidate, no-transform
| Content-Type: text/html; charset=utf-8
| Set-Cookie: i_like_gitea=2826470014a49d27; Path=/; HttpOnly; SameSite=Lax
| Set-Cookie: _csrf=UN-81XP8xq0YBfbAzmSIzsLfRkY6MTcyMTUwNDczNzQ5OTQyNzU5NA; Path=/; Max-Age=86400; HttpOnly; SameSite=Lax
| X-Frame-Options: SAMEORIGIN
| Date: Sat, 20 Jul 2024 19:45:37 GMT
| <!DOCTYPE html>
| <html lang="en-US" class="theme-auto">
| <head>
| <meta name="viewport" content="width=device-width, initial-scale=1">
| <title>GreenHorn</title>
| <link rel="manifest" href="data:application/json;base64,eyJuYW1lIjoiR3JlZW5Ib3JuIiwic2hvcnRfbmFtZSI6IkdyZWVuSG9ybiIsInN0YXJ0X3VybCI6Imh0dHA6Ly9ncmVlbmhvcm4uaHRiOjMwMDAvIiwiaWNvbnMiOlt7InNyYyI6Imh0dHA6Ly9ncmVlbmhvcm4uaHRiOjMwMDAvYXNzZXRzL2ltZy9sb2dvLnBuZyIsInR5cGUiOiJpbWFnZS9wbmciLCJzaXplcyI6IjUxMng1MTIifSx7InNyYyI6Imh0dHA6Ly9ncmVlbmhvcm4uaHRiOjMwMDAvYX
| HTTPOptions:
| HTTP/1.0 405 Method Not Allowed
| Allow: HEAD
| Allow: HEAD
| Allow: GET
| Cache-Control: max-age=0, private, must-revalidate, no-transform
| Set-Cookie: i_like_gitea=d7257a3ef135f06e; Path=/; HttpOnly; SameSite=Lax
| Set-Cookie: _csrf=AVPQQ6QR9C8_q7CGXC8vy6boHMo6MTcyMTUwNDc0Mjc4NTIxMzQ2Ng; Path=/; Max-Age=86400; HttpOnly; SameSite=Lax
| X-Frame-Options: SAMEORIGIN
| Date: Sat, 20 Jul 2024 19:45:42 GMT
|_ Content-Length: 0
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port3000-TCP:V=7.94SVN%I=7%D=7/20%Time=669C13E1%P=aarch64-unknown-linux
SF:-gnu%r(GenericLines,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-T
SF:ype:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400
SF:\x20Bad\x20Request")%r(GetRequest,2A60,"HTTP/1\.0\x20200\x20OK\r\nCache
SF:-Control:\x20max-age=0,\x20private,\x20must-revalidate,\x20no-transform
SF:\r\nContent-Type:\x20text/html;\x20charset=utf-8\r\nSet-Cookie:\x20i_li
SF:ke_gitea=2826470014a49d27;\x20Path=/;\x20HttpOnly;\x20SameSite=Lax\r\nS
SF:et-Cookie:\x20_csrf=UN-81XP8xq0YBfbAzmSIzsLfRkY6MTcyMTUwNDczNzQ5OTQyNzU
SF:5NA;\x20Path=/;\x20Max-Age=86400;\x20HttpOnly;\x20SameSite=Lax\r\nX-Fra
SF:me-Options:\x20SAMEORIGIN\r\nDate:\x20Sat,\x2020\x20Jul\x202024\x2019:4
SF:5:37\x20GMT\r\n\r\n<!DOCTYPE\x20html>\n<html\x20lang=\"en-US\"\x20class
SF:=\"theme-auto\">\n<head>\n\t<meta\x20name=\"viewport\"\x20content=\"wid
SF:th=device-width,\x20initial-scale=1\">\n\t<title>GreenHorn</title>\n\t<
SF:link\x20rel=\"manifest\"\x20href=\"data:application/json;base64,eyJuYW1
SF:lIjoiR3JlZW5Ib3JuIiwic2hvcnRfbmFtZSI6IkdyZWVuSG9ybiIsInN0YXJ0X3VybCI6Im
SF:h0dHA6Ly9ncmVlbmhvcm4uaHRiOjMwMDAvIiwiaWNvbnMiOlt7InNyYyI6Imh0dHA6Ly9nc
SF:mVlbmhvcm4uaHRiOjMwMDAvYXNzZXRzL2ltZy9sb2dvLnBuZyIsInR5cGUiOiJpbWFnZS9w
SF:bmciLCJzaXplcyI6IjUxMng1MTIifSx7InNyYyI6Imh0dHA6Ly9ncmVlbmhvcm4uaHRiOjM
SF:wMDAvYX")%r(Help,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type
SF::\x20text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x2
SF:0Bad\x20Request")%r(HTTPOptions,1A4,"HTTP/1\.0\x20405\x20Method\x20Not\
SF:x20Allowed\r\nAllow:\x20HEAD\r\nAllow:\x20HEAD\r\nAllow:\x20GET\r\nCach
SF:e-Control:\x20max-age=0,\x20private,\x20must-revalidate,\x20no-transfor
SF:m\r\nSet-Cookie:\x20i_like_gitea=d7257a3ef135f06e;\x20Path=/;\x20HttpOn
SF:ly;\x20SameSite=Lax\r\nSet-Cookie:\x20_csrf=AVPQQ6QR9C8_q7CGXC8vy6boHMo
SF:6MTcyMTUwNDc0Mjc4NTIxMzQ2Ng;\x20Path=/;\x20Max-Age=86400;\x20HttpOnly;\
SF:x20SameSite=Lax\r\nX-Frame-Options:\x20SAMEORIGIN\r\nDate:\x20Sat,\x202
SF:0\x20Jul\x202024\x2019:45:42\x20GMT\r\nContent-Length:\x200\r\n\r\n")%r
SF:(RTSPRequest,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x2
SF:0text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad
SF:\x20Request");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelThe scan revealed three open ports: 22 (SSH), 80 (HTTP), and 3000 (PPP).
The web page:
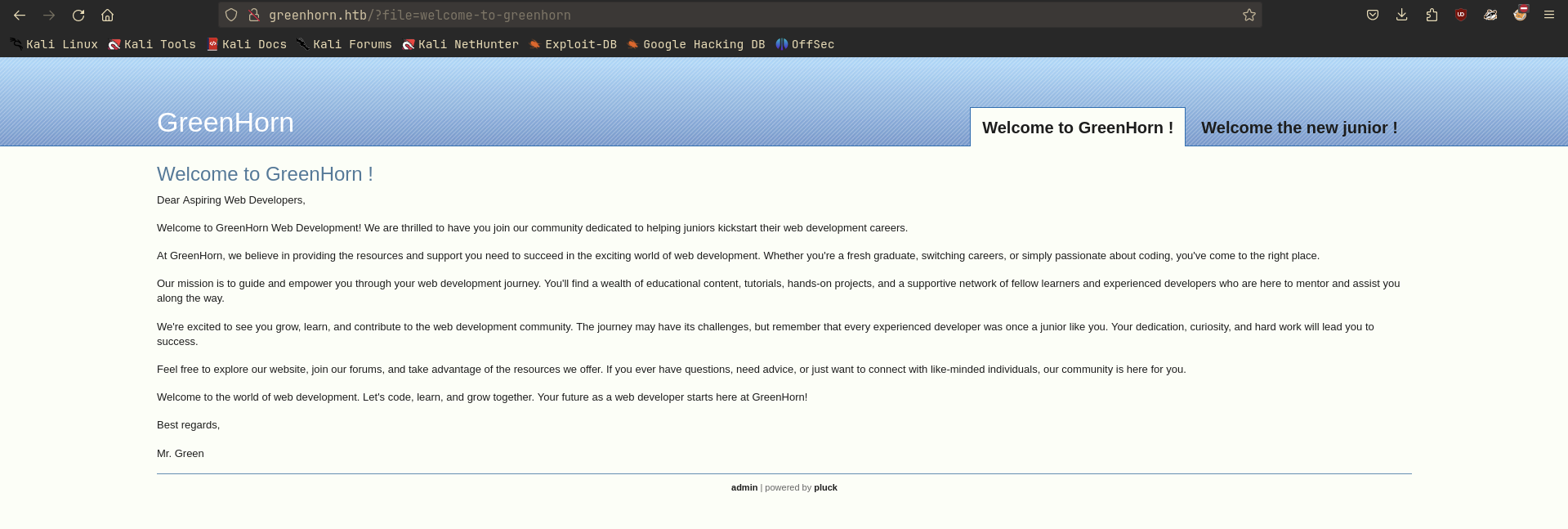
It contains a link to admin panel, however, it is password protected.
I checked the 3000 port and found a Gitea instance running.
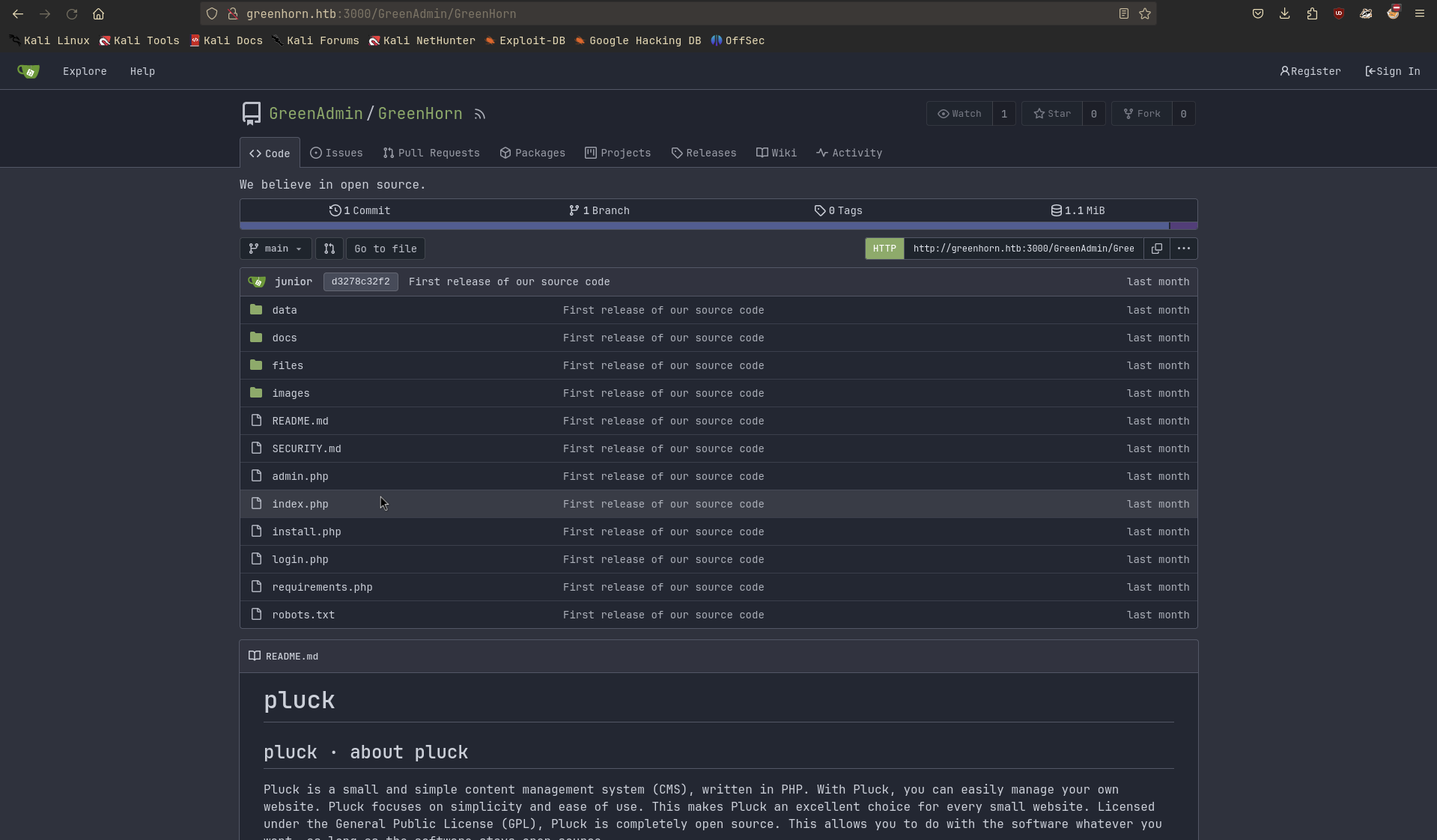
GreenHorn is using Gittea for version control. So I guessed that there might be some credentials in the repository.
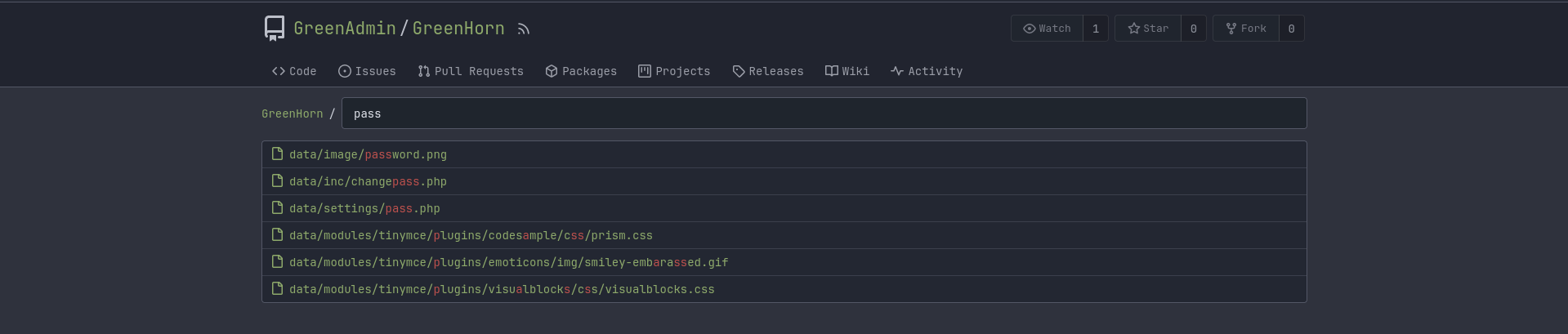
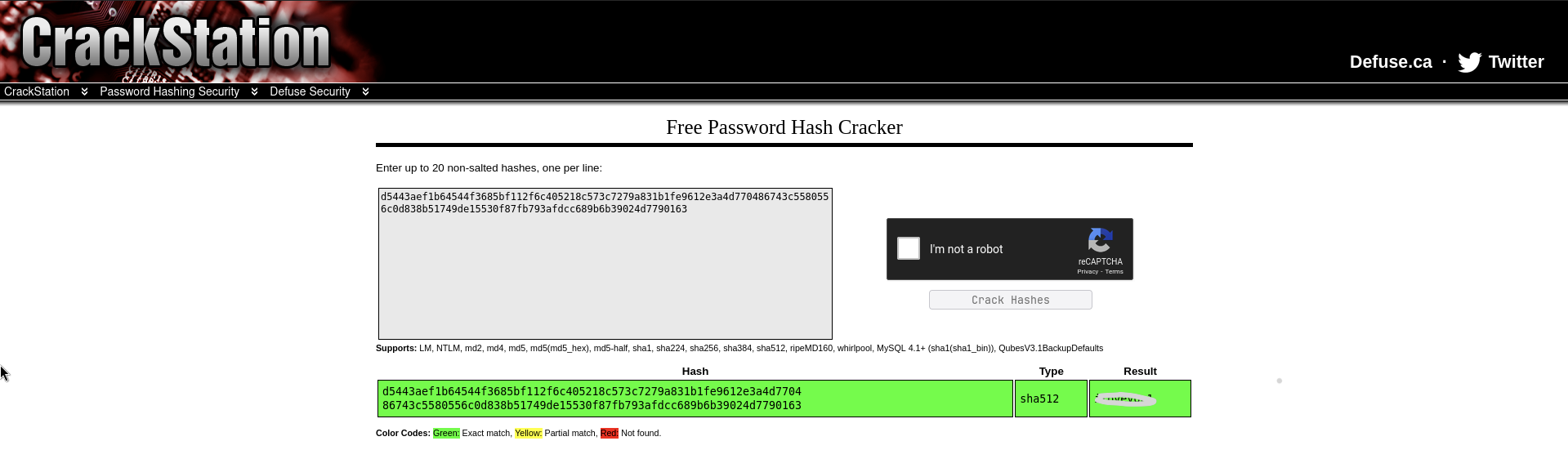
No surprise, I found the admin credentials in the repository. Using crackstation I cracked the password.
Exploitation
Initial Foothold
I logged in to the admin panel using the cracked credentials. It is running Pluck CMS version 4.7.18.
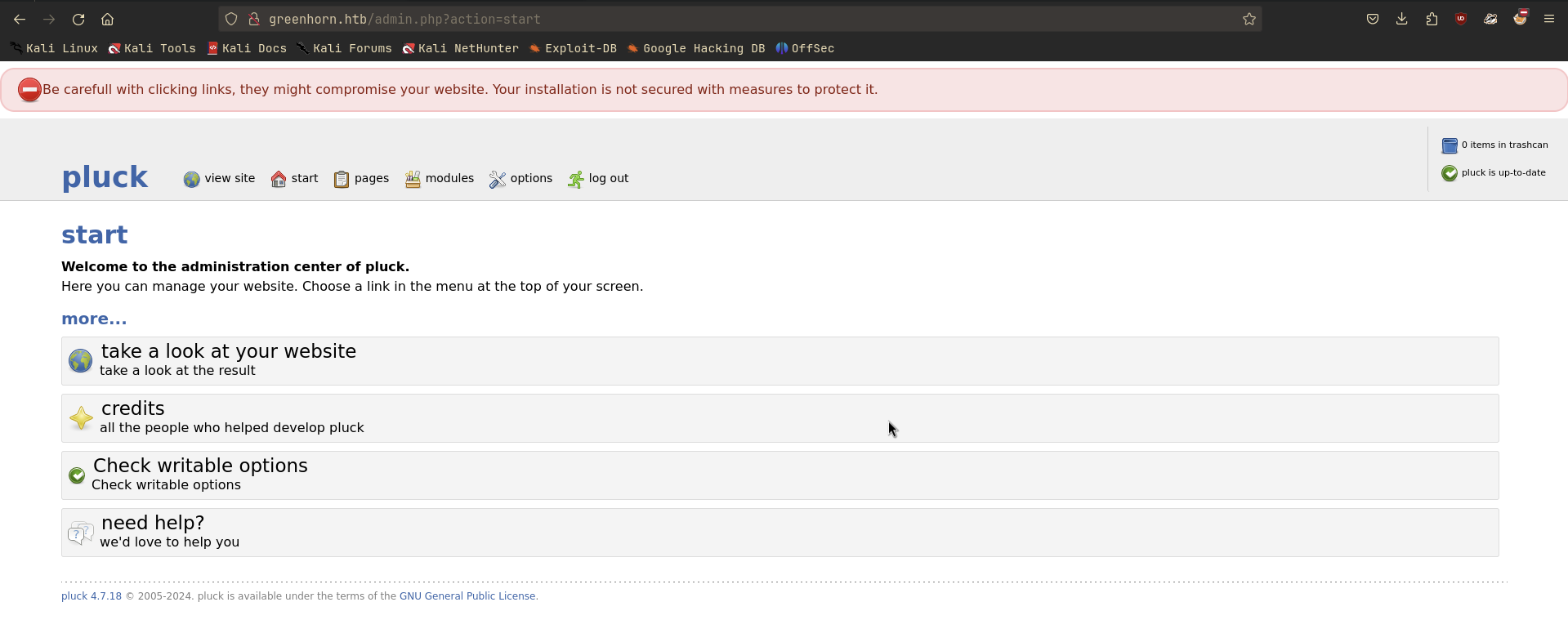
I did some research on Pluck CMS and found an authenticated Remote Code Execution (RCE) exploit: Pluck CMS 4.7.18 - Remote Code Execution.
It will upload a ZIP file containing a PHP reverse shell script. So I created one using pentestmonkey php-reverse-shell
Zip it with zip command:
zip -r rev.zip rev.phpThen upload the ZIP file to the admin panel.
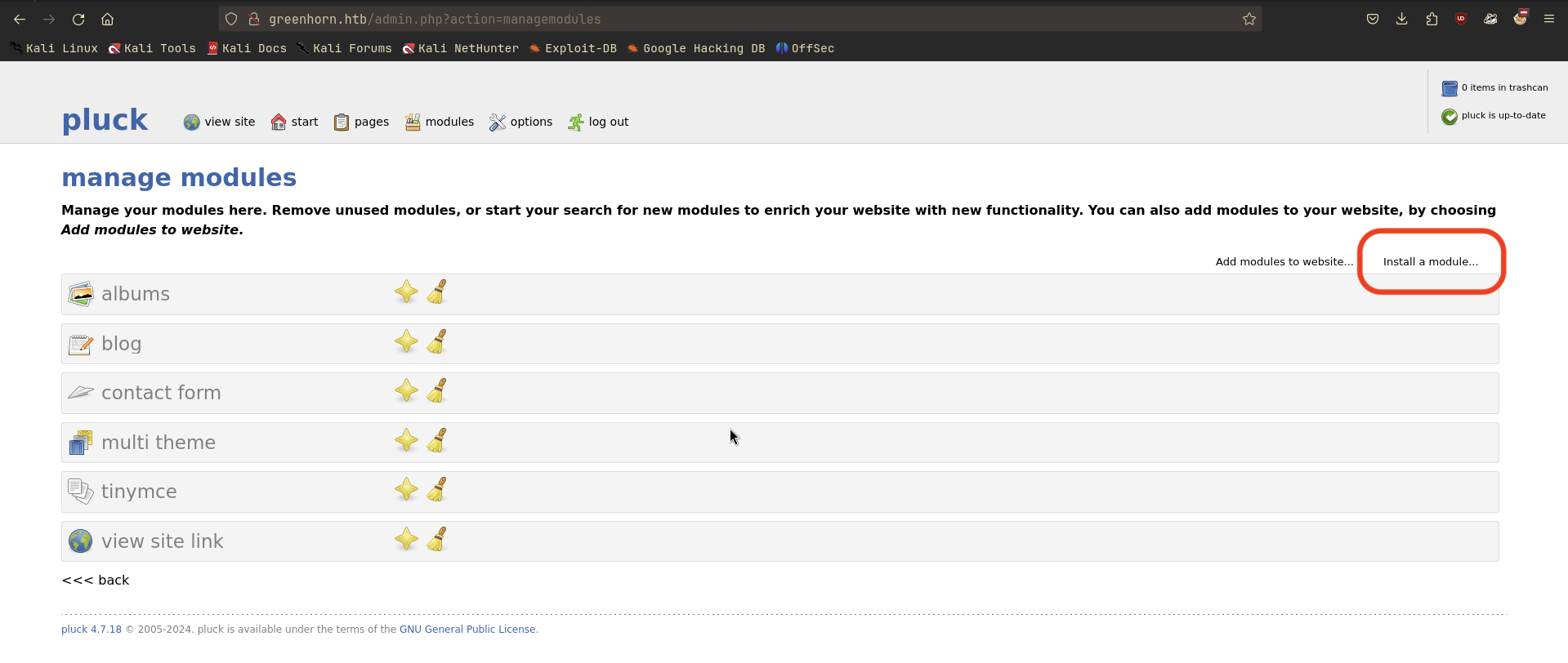
Here I uploaded the ZIP file and gained a reverse shell.

Next step, stabilize the shell:
python3 -c 'import pty; pty.spawn("/bin/bash")'
CTRL+Z
stty raw -echo; fgHowever this user is not the one containing the user flag. After a while of enumeration, I found out that it is using the same password for the admin panel.
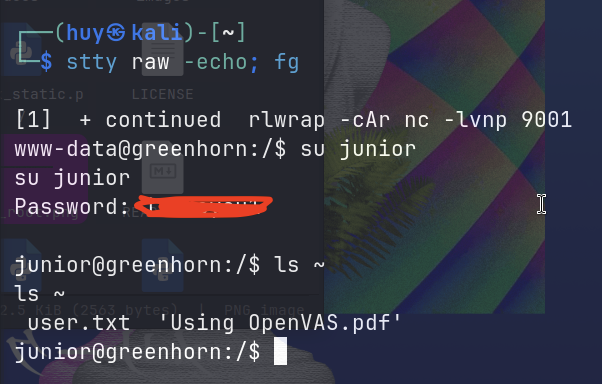
Privilege Escalation
There is a pdf file in the home directory. I downloaded it to my local machine and found that it contains a pixelated image.

Working with pixelated images is a common challenge in CTFs. I used the Depix tool. However, the image is within the PDF file. Which means I need to extract the image first.
I used pdfimages to extract the image:
sudo apt install poppler-utils
pdfimages -j openvas.pdf output_prefixThen I used the Depix tool to extract the password:
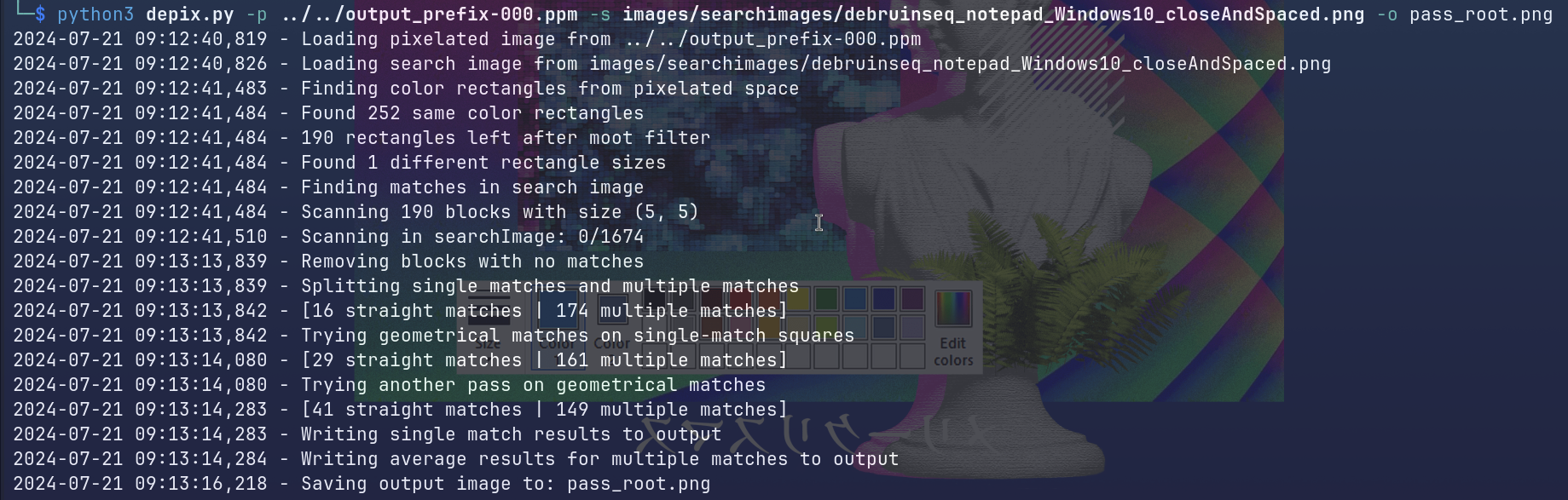
Gain root access:
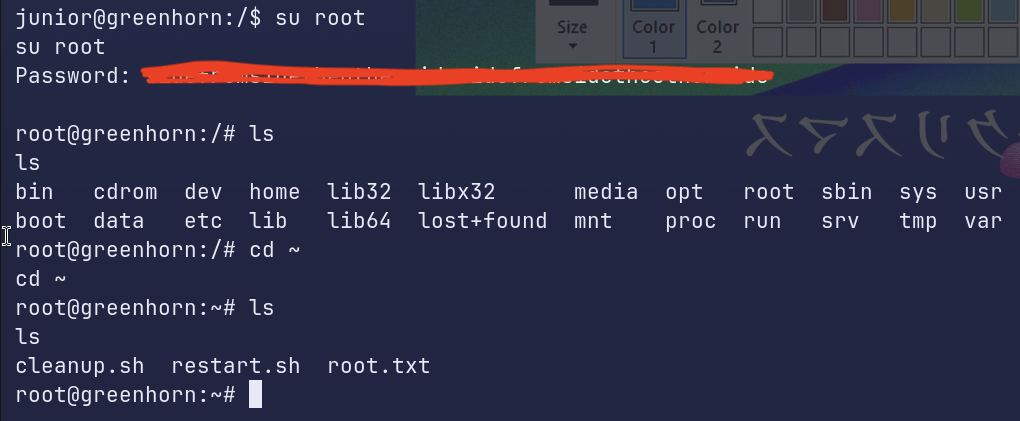 And that’s it! The machine is now rooted.
And that’s it! The machine is now rooted.
Conclusion
This machine was a bit strange. The fact that it is using the same password for the admin panel and the user account is a bit unrealistic. However, it was a fun machine to work on. The Depix tool was a new tool for me, and I learned how to extract passwords from pixelated images. I hope you enjoyed reading this write-up. Stay tuned for more!