Initial investigation
While examining an .ad1 artifact lately, I saw activities that I suspected to be an exfiltration using removable media.
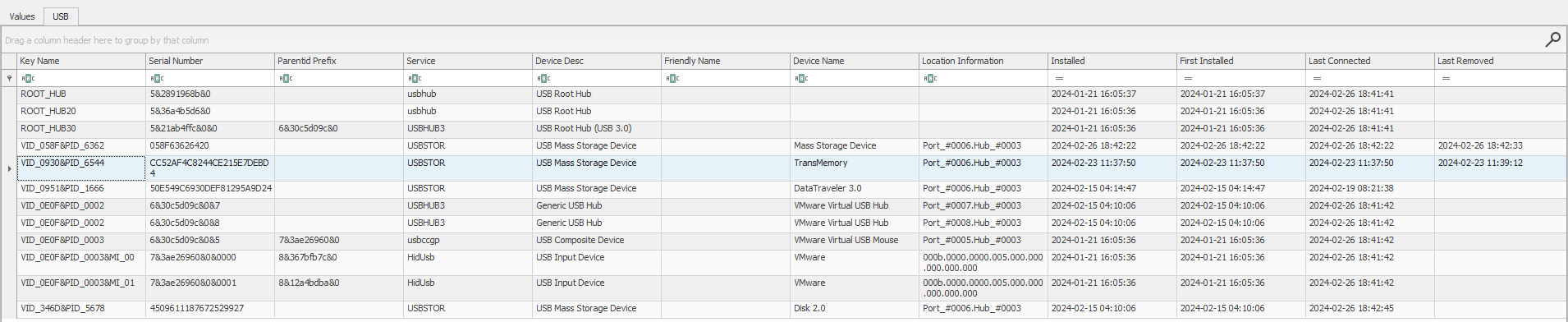
USBSTOR is a key in the Windows Registry which contains information about USB storage devices. Unfortunately, the registry does not store the detailed activity of the USB. But we have the connected and removed time, which would be very useful in terms of finding exfiltrated data.
Windows automatically creates .lnk files in the Recent folder as a “history” of files accessed by the user. Unlike temporary USB registry entries, .lnk files remain even after the USB is unplugged. This creates “orphaned” shortcuts that still reference the USB drive letter/path. This give us an opportunity to figure out what kind of data has been copied or moved to the USB.
- For Windows 7 to 11:
Users\<User>\AppData\Roaming\Microsoft\Windows\Recent - For Windows XP:
Documents and Settings\<User>\Recent
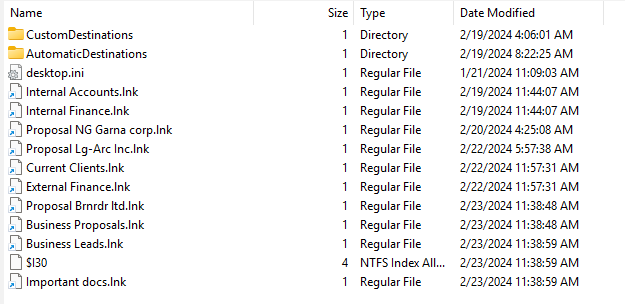
I will use LECmd by Eric Zimmerman to decode all available information contained in shortcut files found on Windows operating systems.
# Sample usage and exporting to csv file
.\LECmd.exe -d ..\..\Recent --csv ..\..\Recent\Extend investigation
There are more information we can gather. Under SOFTWARE\Microsoft\Windows Portable Devices contains information of USB that connected to our machine.
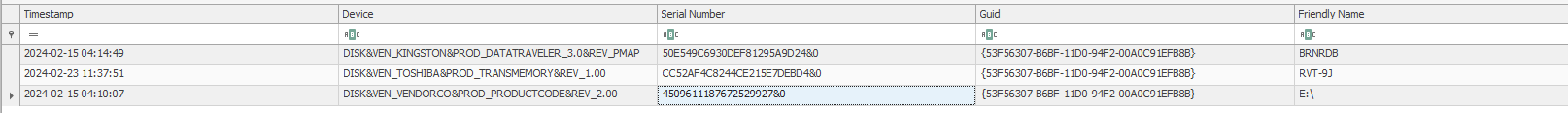
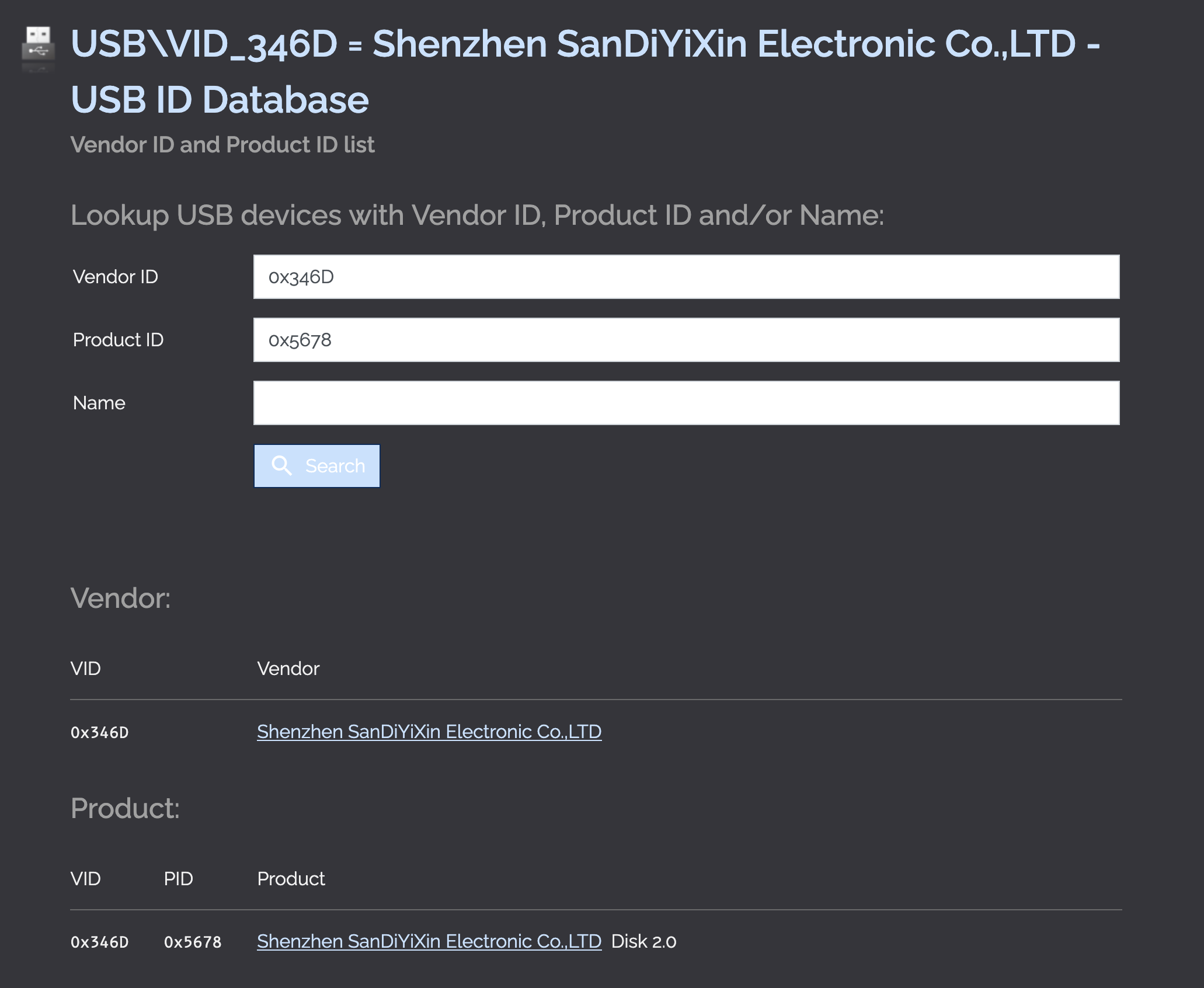
The serial number can be used to search through Windows Registry to find more relatable details of the USB. Among them is the Vendor ID and Product ID.
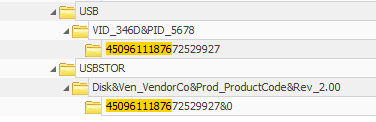
VID_346D&PID_5678
I have tried searching online with search engine but did not go well, so I went looking for USB Database to query instead, but they seems to not contain the ID I got. Fortunately, a person help me out by giving me this link point to the USB ID Database: