If you ever see a web application that allow you to upload a file, it is worth trying to fuzz different file types. A misconfiguration in the web server or the application itself may allow you to upload a file that is not intended to be uploaded.
Using Burp Suite
After capturing the request, send it to Intruder. In the Positions tab, select the file name and click on Add §. This will add a marker around the file name.
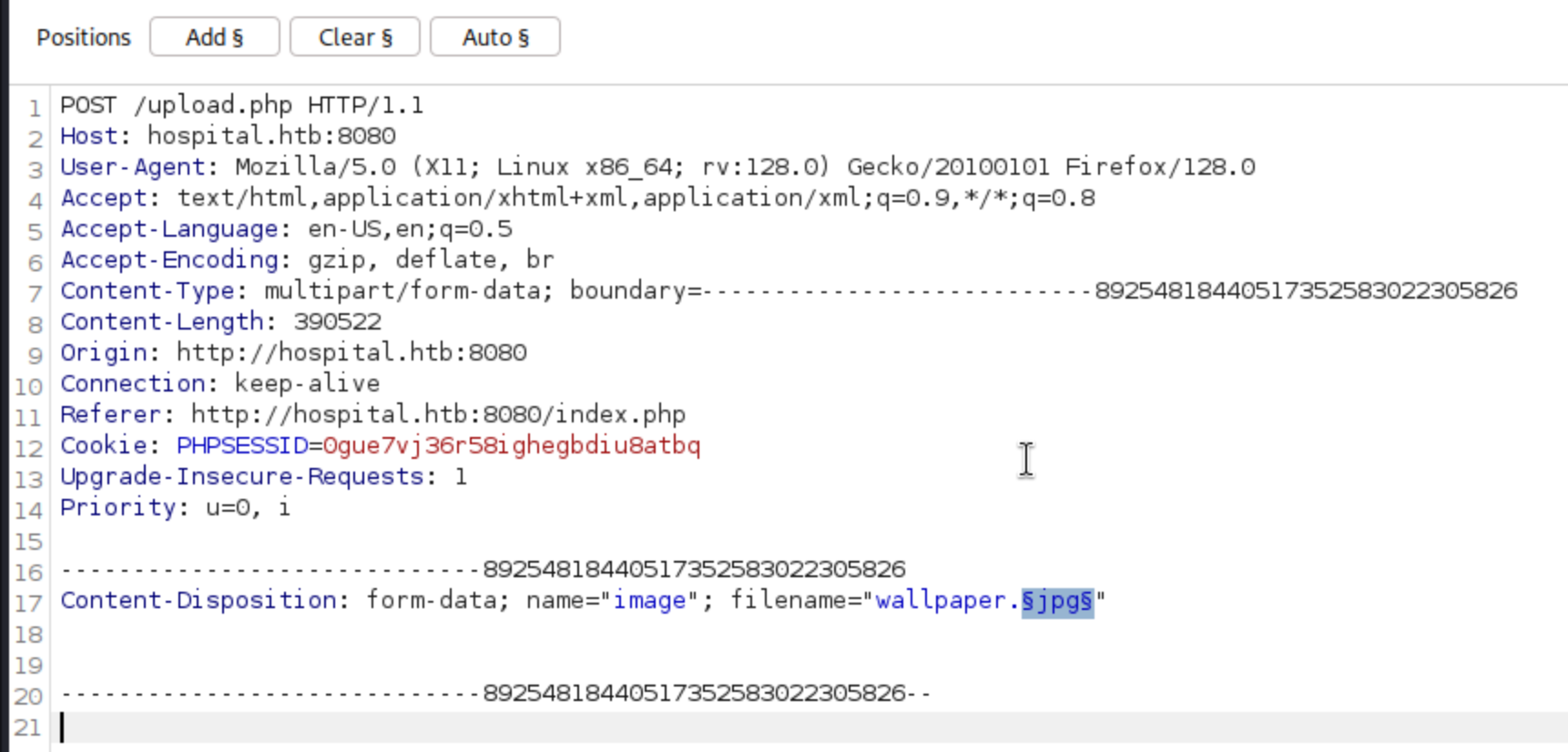
In the Payloads tab, select the Simple list option and add the payloads you want. Personally, SecLists/Discovery/Web-Content/web-extensions.txt is good enough for most cases. You can also add your own payloads if you want to test specific file types.

Go for the Start Attack when you prepared.
The results are different depending on the web application. You may see a 200 OK response, which means that the file was uploaded successfully. The Response Received or Length might stand out as well. However, in my case, the successful upload was indicated within the Response Body. The web application returned the location of Location: /success.php.
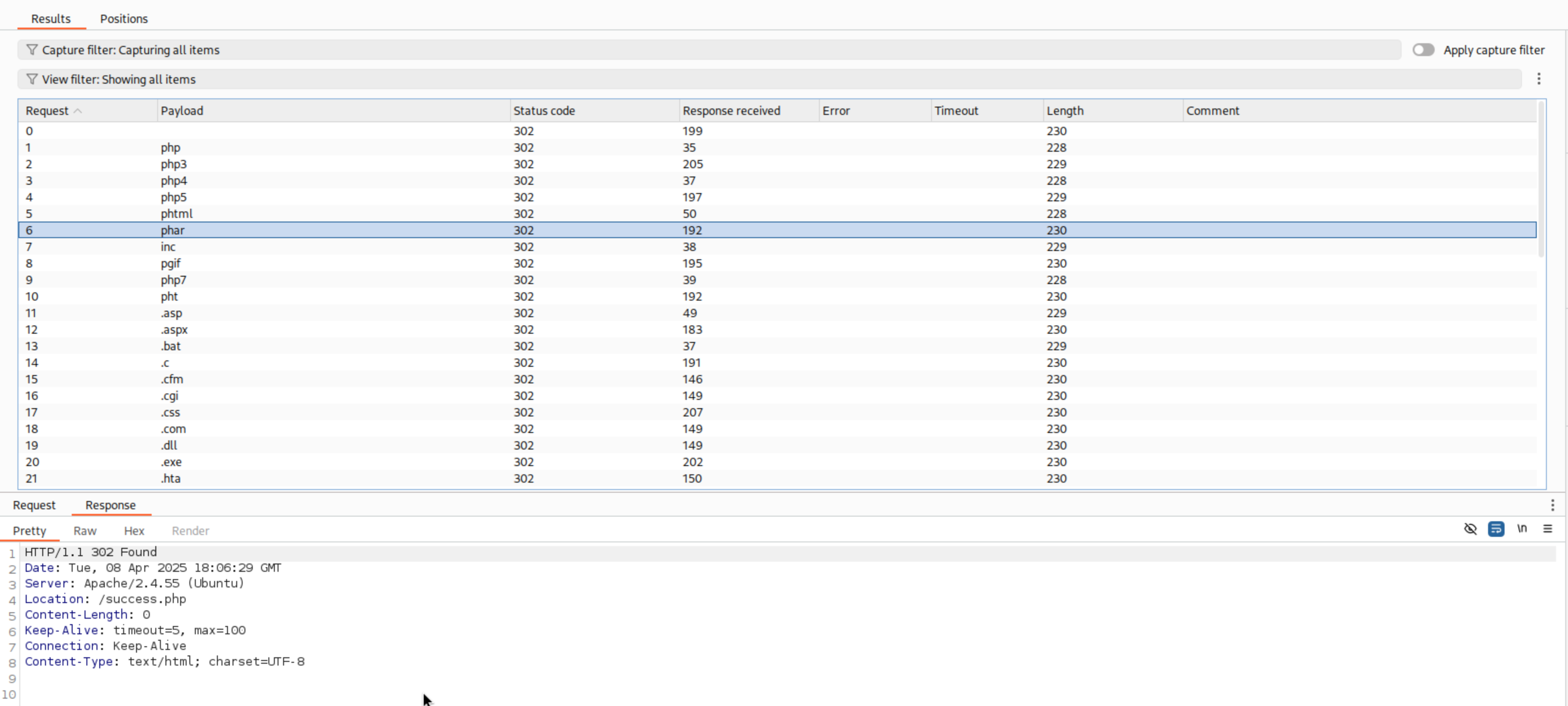
Using ffuf
This is a bit harder for those who are not familiar with the command line. However, it is a better option for fuzzing using huge payloads due to the limitation of Burp Suite Community Edition.
ffuf -w /usr/share/seclists/Discovery/Web-Content/web-extensions.txt -u http://hospital.htb:8080/upload.php -X POST \
-H "Content-Type: multipart/form-data; boundary=---------------------------89254818440517352583022305826" \
-H "Cookie: PHPSESSID=0gue7vj36r58ighegbdiu8atbq" \
-d $'-----------------------------89254818440517352583022305826\r\nContent-Disposition: form-data; name="image"; filename="test.FUZZ"\r\nContent-Type: image/jpeg\r\n\r\n\r\n-----------------------------89254818440517352583022305826--' \
-fr "Location: /failed.php"-wis the wordlist to use. In this case, I used the web extensions list from SecLists.-uis the URL to fuzz. In this case, it is the upload.php page.-Xis the HTTP method to use. In this case, it is POST.-His the HTTP header to use. In this case, I used the Content-Type and Cookie headers.-dis the data to send. In this case, it is the multipart/form-data request with the file name set to FUZZ.-fris the filter to use. In this case, it is the Location header that indicates a failed upload.
Only the successful uploads will be shown in the results. You can also use -o to save the results to a file.
Further Reading: