While traditional network analysis tools like Wireshark provide detailed packet-level information, security-focused tools often offer additional context and correlation capabilities that can help us quickly identify malicious communication patterns. For this analysis, we’re using Zui, a specialized security analysis tool that can process PCAP files and highlight security alerts based on known threat signatures and behavioral patterns.
This is an example usage of Zui, nothing has been compromised during the process.
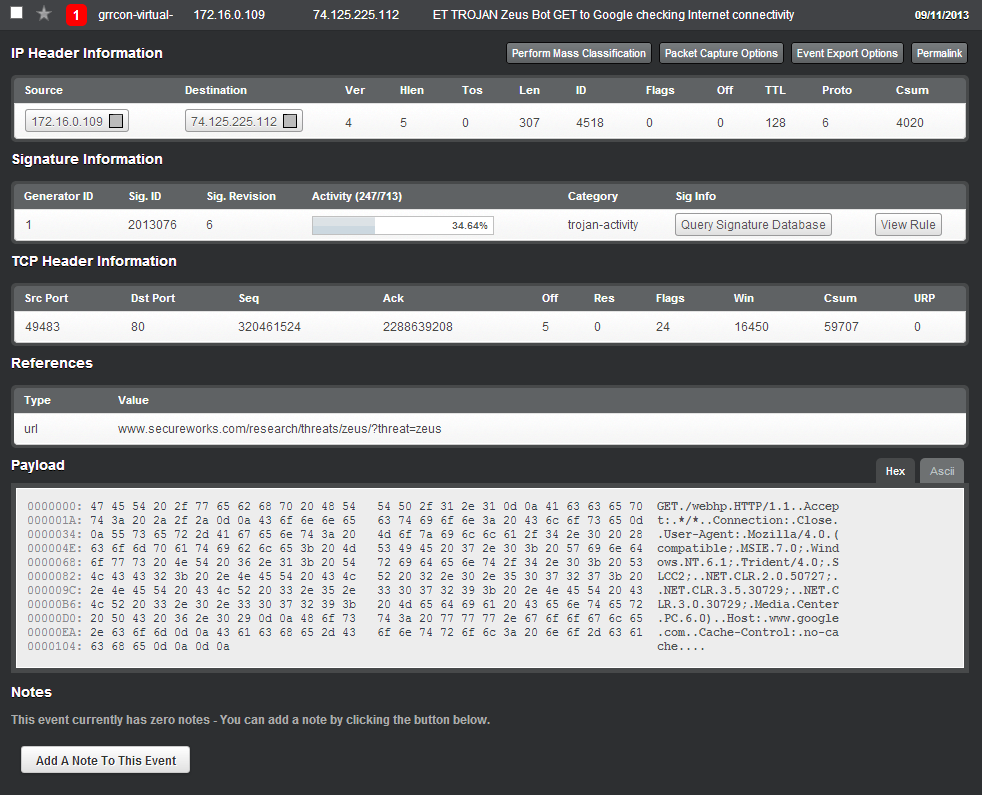
As our investigation into the Zeus malware infection deepens, we need to identify the most critical component of the malicious infrastructure - the Command and Control (C2) server. The C2 server is the central hub from which attackers control infected systems, issue commands, receive stolen data, and coordinate their malicious activities. Identifying and blocking communication to this server is a top priority for the infrastructure team to contain the incident and prevent further data exfiltration.
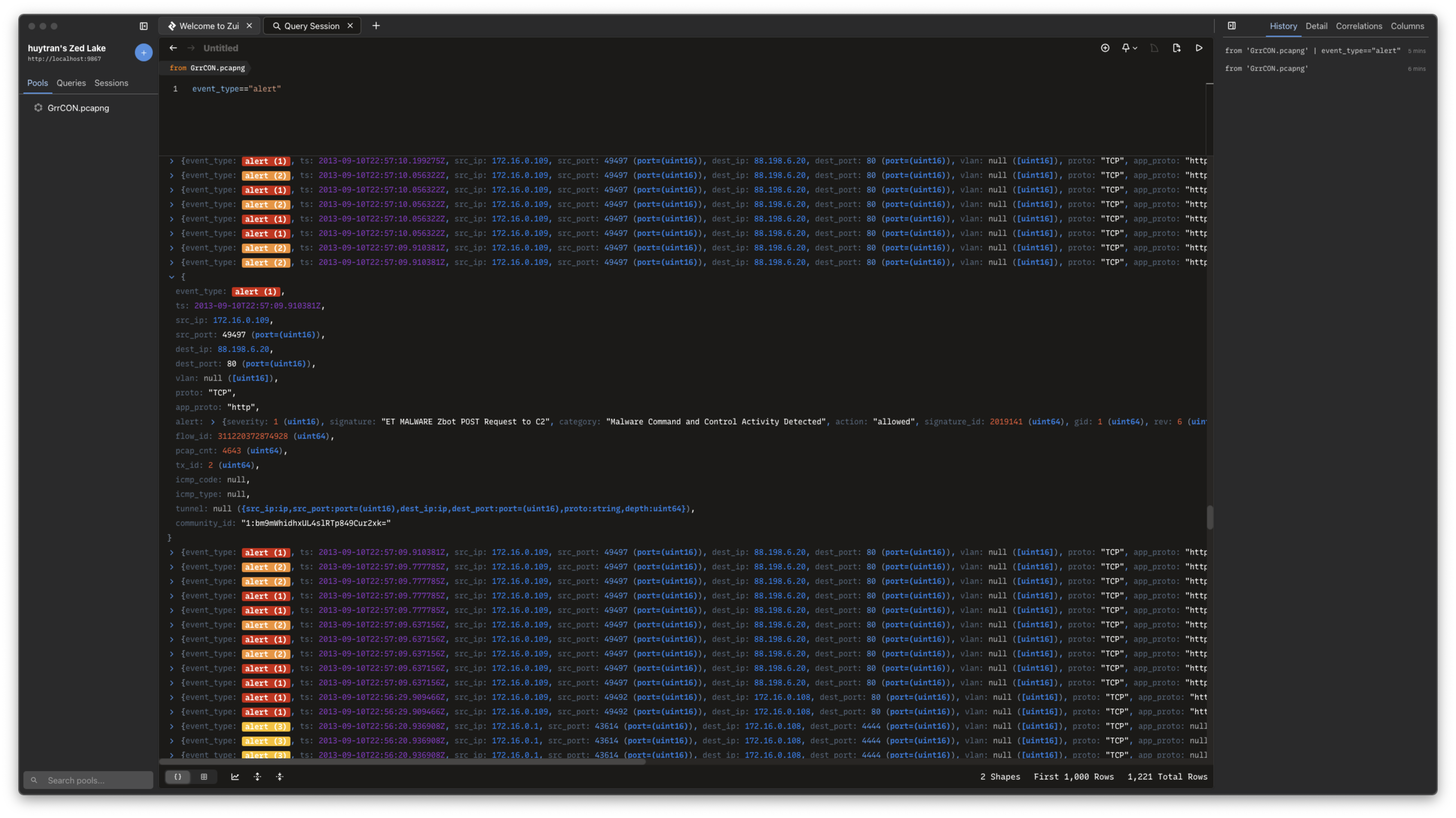
Examining the detailed alert information, we can see a particularly concerning alert with the signature ET MALWARE Zbot POST Request to C2 and a category of Malware Command and Control Activity Detected. This alert identifies Zeus (also known as Zbot) malware communication with its command and control infrastructure. The alert has a severity level of 1, indicating high severity, and was detected at timestamp 2013-09-10 22:56:09, which aligns with our established incident timeline.