One of the first steps in Kerberos authentication is preauthentication. Pre-authentication uses the user’s password to encrypt a timestamp. The domain controller (DC) will decrypt this to validate the correct password and not have a previous request replayed. A vulnerability can result when preauthentication is disabled.
Once this is disabled, a hacker can request authentication data for any user, and the DC will return an encrypted TGT. It can then be used to brute force in an offline environment to crack the password.
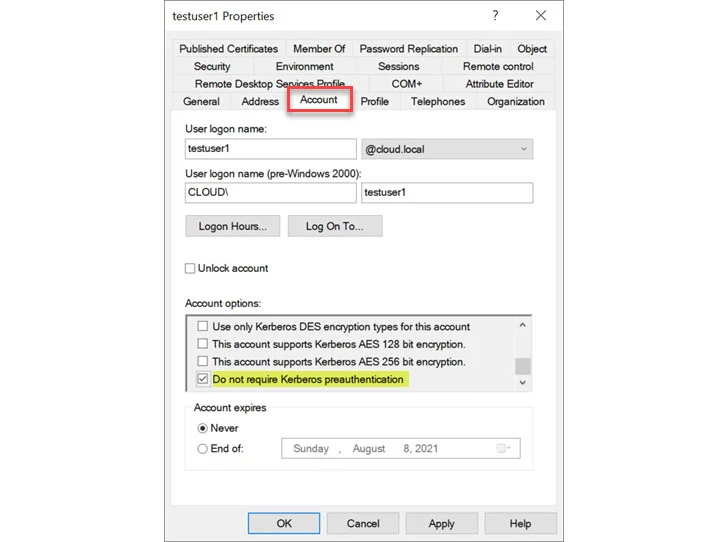
Preauthentication can be disabled on any user account in Active Directory on the Account tab under the Account options. Look for the checkbox “Do not require Kerberos preauthentication.”
AS-REP Roasting is the technique that allows retrieving password hashes for users that have this flag set in Active Directory. Additionally, various cybersecurity and hacking tools allow cracking the TGTs harvested from Active Directory. These include Rubeus and Hashcat.
Using a tool like Rubeus, attackers can find the accounts that do not require preauthentication and then extract the TGT data for cracking the password offline.
Data can be transformed into a format that can be cracked by an offline tool such as Hashcat, which can use brute force password cracking against the hashes. This process incorporates the use of a dictionary file for brute-force password guessing
TL;DR
AS_REP Roasting is taking place during the initial authentication procedure within Kerberos. It´s abusing the fact, that for accounts with the option Do not require Kerberos preauthentication set, there is no need to send the (normally required) encrypted timestamp (with the users password hash) at the very beginning. Thus everyone on the network who knows the name of an affected account may ask the KDC to authenticate as that user and in return fetch a AS_REP response which partly is encrypted with the AS_REP roast-able account’s password hash. Once obtained, an attacker can try to offline crack the hash and fetch the cleartext credentials.