Work in situation where the user are positioned in a domain with either an inbound or bidirectional domain/forest trust.
Kerberos attacks such as Kerberoasting and AS-REP Roasting can be performed across trusts, depending on the trust direction. Sometimes it is not possible to escalate privileges in the current domain, but instead can obtain a Kerberos ticket and crack a hash for an administrative user in another domain that has Domain/Enterprise Admin privileges in both domains.
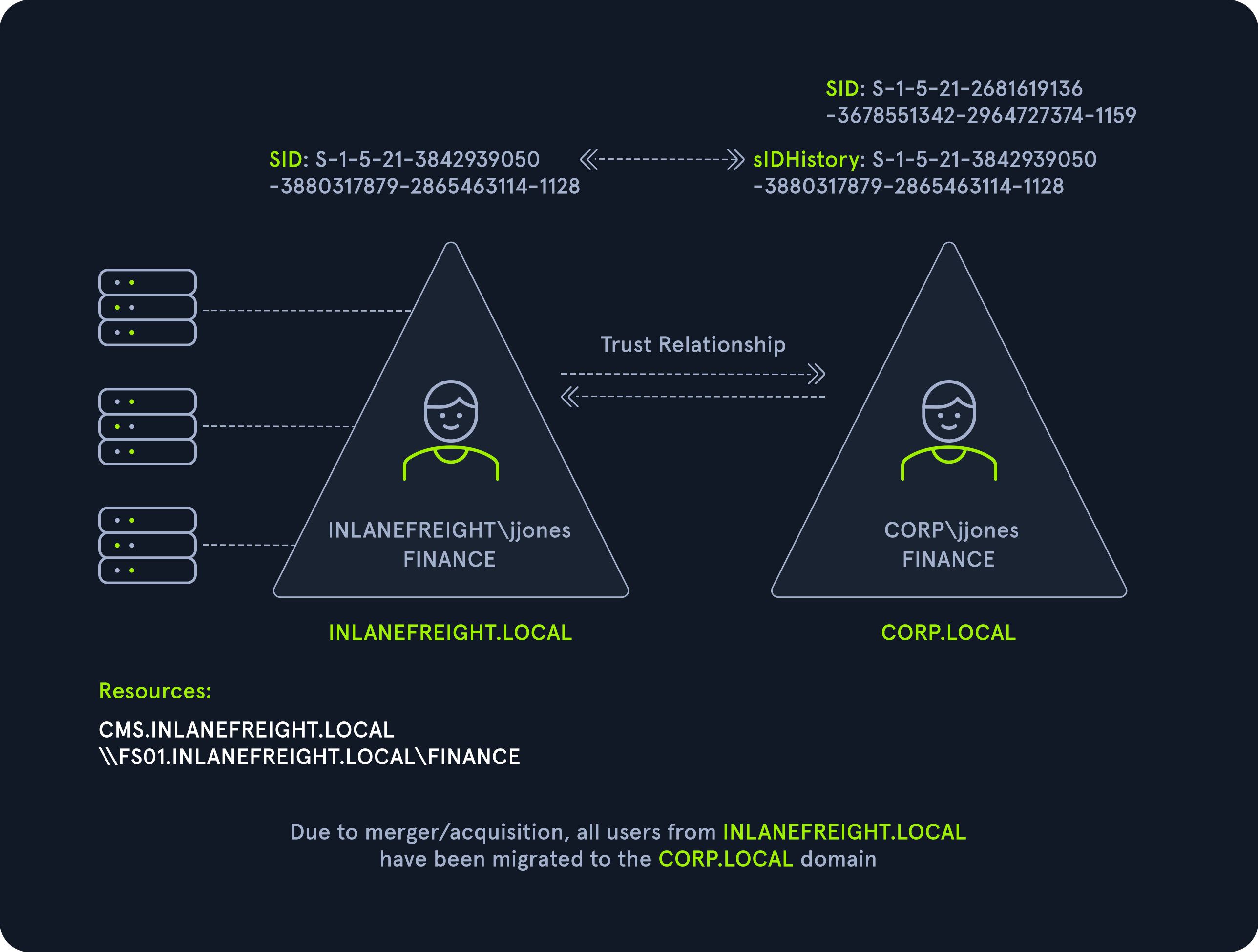
SID History Abuse - Cross Forest
SID History can also be abused across a forest trust. If a user is migrated from one forest to another and SID Filtering is not enabled, it becomes possible to add a SID from the other forest, and this SID will be added to the user’s token when authenticating across the trust. If the SID of an account with administrative privileges in Forest A is added to the SID history attribute of an account in Forest B, assuming they can authenticate across the forest, then this account will have administrative privileges when accessing resources in the partner forest.
 Source: HackTheBox
Source: HackTheBox